Answered step by step
Verified Expert Solution
Question
1 Approved Answer
need help working this out pls You are presented three challenges related to events in a simulated penetration test. Using the Framework for Ethical Decision
need help working this out pls 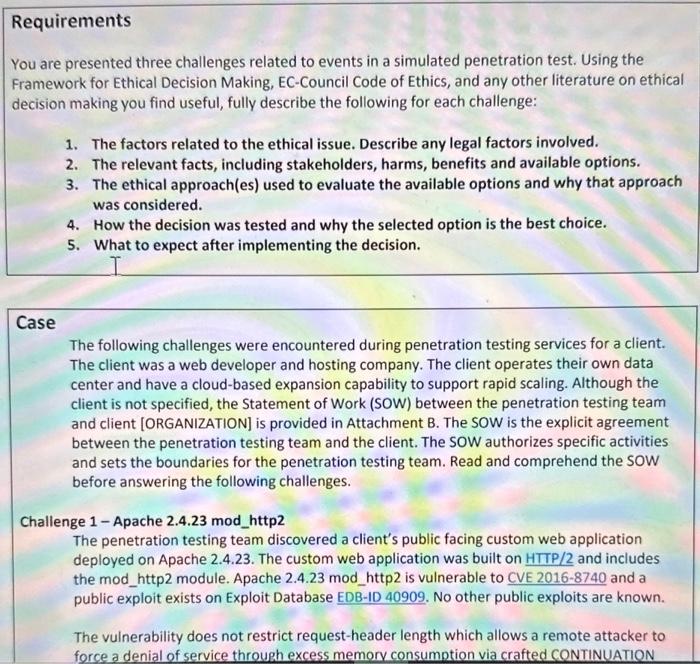
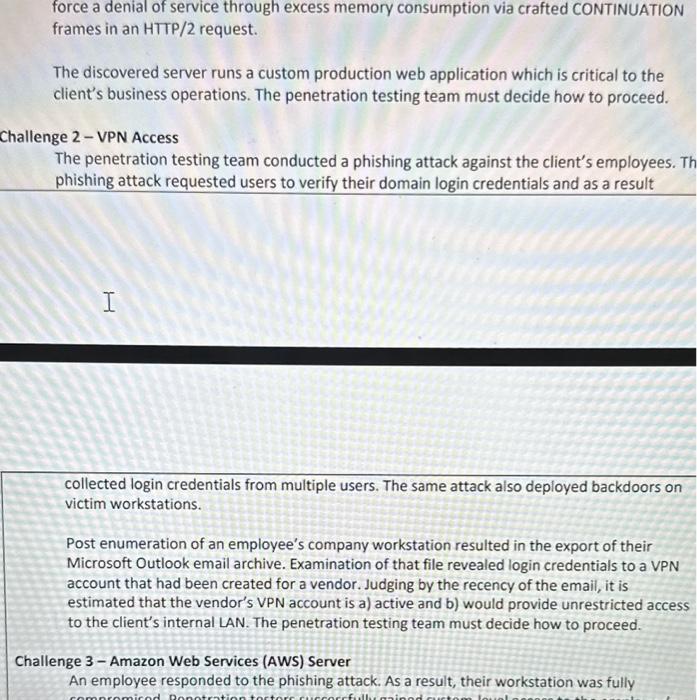

You are presented three challenges related to events in a simulated penetration test. Using the Framework for Ethical Decision Making, EC-Council Code of Ethics, and any other literature on ethical decision making you find useful, fully describe the following for each challenge: 1. The factors related to the ethical issue. Describe any legal factors involved. 2. The relevant facts, including stakeholders, harms, benefits and available options. 3. The ethical approach(es) used to evaluate the available options and why that approach was considered. 4. How the decision was tested and why the selected option is the best choice. 5. What to expect after implementing the decision. Case The following challenges were encountered during penetration testing services for a client. The client was a web developer and hosting company. The client operates their own data center and have a cloud-based expansion capability to support rapid scaling. Although the client is not specified, the Statement of Work (SOW) between the penetration testing team and client [ORGANIZATION] is provided in Attachment B. The SOW is the explicit agreement between the penetration testing team and the client. The SOW authorizes specific activities and sets the boundaries for the penetration testing team. Read and comprehend the SOW before answering the following challenges. Challenge 1-Apache 2.4.23 mod_http2 The penetration testing team discovered a client's public facing custom web application deployed on Apache 2.4.23. The custom web application was built on HTTP/2 and includes the mod_http2 module. Apache 2.4.23 mod_http2 is vulnerable to CVE 2016-8740 and a public exploit exists on Exploit Database EDB-ID 40909. No other public exploits are known. The vulnerability does not restrict request-header length which allows a remote attacker to force a denial of service through excess memory consumption via crafted CONTINUATION force a denial of service through excess memory consumption via crafted CONTINUATION frames in an HTTP/2 request. The discovered server runs a custom production web application which is critical to the client's business operations. The penetration testing team must decide how to proceed. hallenge 2 - VPN Access The penetration testing team conducted a phishing attack against the client's employees. T phishing attack requested users to verify their domain login credentials and as a result collected login credentials from multiple users. The same attack also deployed backdoors on victim workstations. Post enumeration of an employee's company workstation resulted in the export of their Microsoft Outlook email archive. Examination of that file revealed login credentials to a VPN account that had been created for a vendor. Judging by the recency of the email, it is estimated that the vendor's VPN account is a) active and b) would provide unrestricted access to the client's internal LAN. The penetration testing team must decide how to proceed. Challenge 3 - Amazon Web Services (AWS) Server An employee responded to the phishing attack. As a result, their workstation was fully An employee responded to the phishing attack. As a result, their workstation was fully compromised. Penetration testers successfully gained system-level access to the employee's workstation. During post attack enumeration the penetration testers discovered documentation for a development network. It was not initially clear where that development network resided, but with additional work testers discovered the development network resided in an AWS project. The developer's documentation was thorough. It included network topology, IP addresses, operating system version information, and service version information. It also included system and application login credentials, vulnerability testing results and documentation for installed and failed patches. The penetration testing team must decide how to proceed 


Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


