Question
NetLab Assignment: Security+ Lab 2 Analyze and Differentiate Types of Malware and Applications Attacks. The Assignment says Directions: In your assigned group and only your
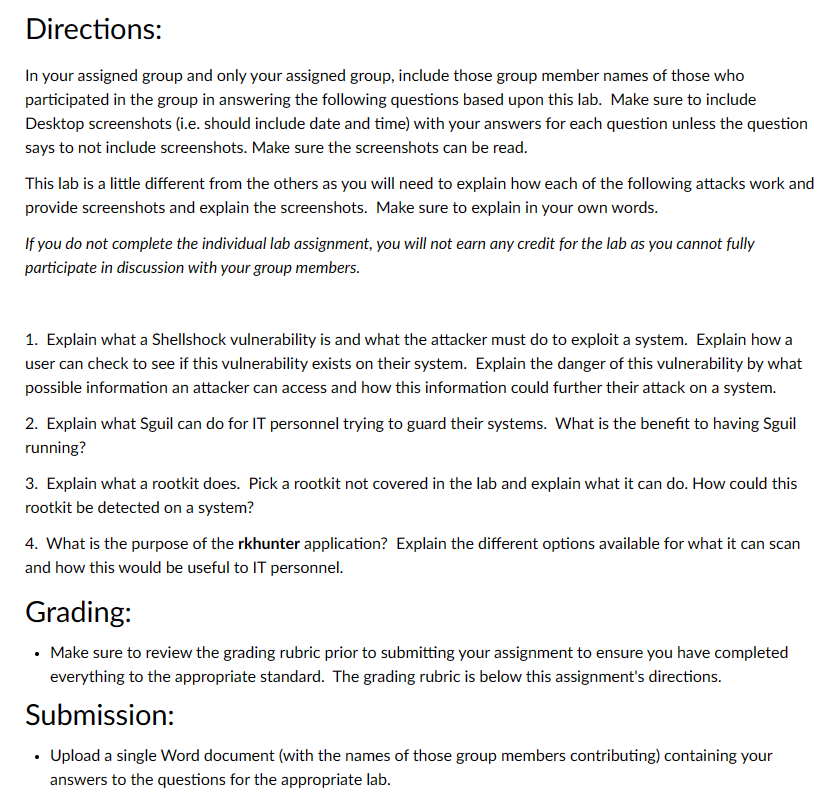
NetLab Assignment: Security+ Lab 2 Analyze and Differentiate Types of Malware and Applications Attacks. The Assignment says "Directions:
In your assigned group and only your assigned group, include those group member names of those who participated in the group in answering the following questions based upon this lab. Make sure to include Desktop screenshots (i.e. should include date and time) with your answers for each question unless the question says to not include screenshots. Make sure the screenshots can be read.
This lab is a little different from the others as you will need to explain how each of the following attacks work and provide screenshots and explain the screenshots. Make sure to explain in your own words.
If you do not complete the individual lab assignment, you will not earn any credit for the lab as you cannot fully participate in discussion with your group members.
1. Explain what a Shellshock vulnerability is and what the attacker must do to exploit a system. Explain how a user can check to see if this vulnerability exists on their system. Explain the danger of this vulnerability by what possible information an attacker can access and how this information could further their attack on a system.
2. Explain what Sguil can do for IT personnel trying to guard their systems. What is the benefit to having Sguil running?
3. Explain what a rootkit does. Pick a rootkit not covered in the lab and explain what it can do. How could this rootkit be detected on a system?
4. What is the purpose of the rkhunter application? Explain the different options available for what it can scan and how this would be useful to IT personnel.
Grading:
- Make sure to review the grading rubric prior to submitting your assignment to ensure you have completed everything to the appropriate standard. The grading rubric is below this assignment's directions.
Submission:
- Upload a single Word document (with the names of those group members contributing) containing your answers to the questions for the appropriate lab."
Do I have to upload on Word Document and also do I need to upload a Lab?
Here's the images I took about the Assignment.
Directions: In your assigned group and only your assigned group, include those group member names of those who participated in the group in answering the following questions based upon this lab. Make sure to include Desktop screenshots (i.e. should include date and time) with your answers for each question unless the question says to not include screenshots. Make sure the screenshots can be read. This lab is a little different from the others as you will need to explain how each of the following attacks work and provide screenshots and explain the screenshots. Make sure to explain in your own words. If you do not complete the individual lab assignment, you will not earn any credit for the lab as you cannot fully participate in discussion with your group members. 1. Explain what a Shellshock vulnerability is and what the attacker must do to exploit a system. Explain how a user can check to see if this vulnerability exists on their system. Explain the danger of this vulnerability by what possible information an attacker can access and how this information could further their attack on a system. 2. Explain what Sguil can do for IT personnel trying to guard their systems. What is the benefit to having Sguil running? 3. Explain what a rootkit does. Pick a rootkit not covered in the lab and explain what it can do. How could this rootkit be detected on a system? 4. What is the purpose of the rkhunter application? Explain the different options available for what it can scan and how this would be useful to IT personnel. Grading: . Make sure to review the grading rubric prior to submitting your assignment to ensure you have completed everything to the appropriate standard. The grading rubric is below this assignment's directions. Submission: Upload a single Word document (with the names of those group members contributing) containing your answers to the questions for the appropriate lab.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


