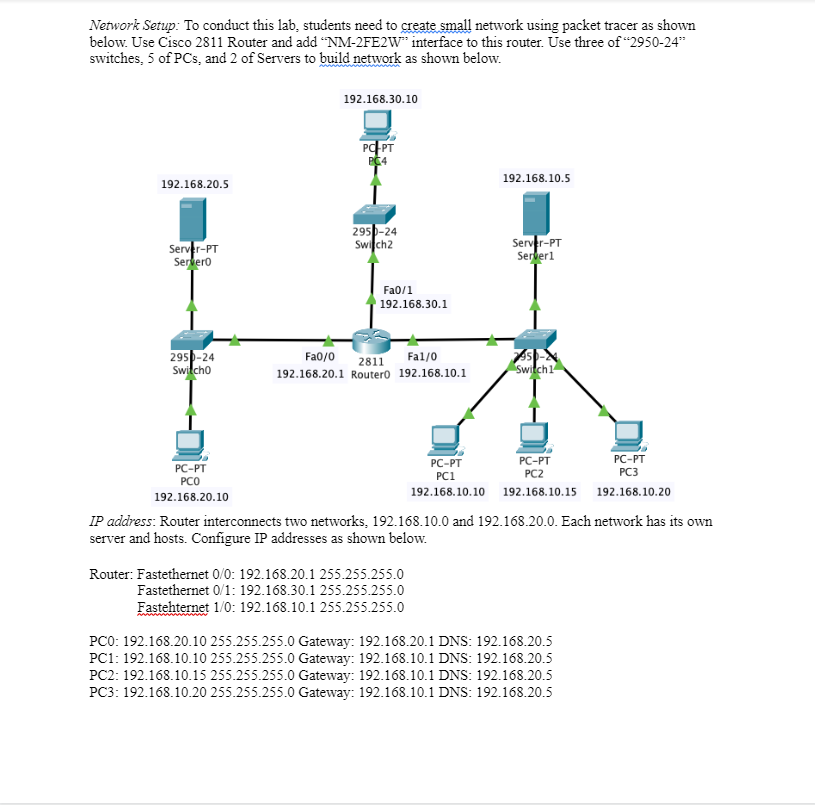


Network Setup: To conduct this lab, students need to create small network using packet tracer as shown below. Use Cisco 2811 Router and add "NM-2FE2W" interface to this router. Use three of "2950-24" switches, 5 of PCs, and 2 of Servers to build network as shown below. IP address: Kouter interconnects two networks, 192.108.1U.U and 19L.108.2U.U. Each network has its own server and hosts. Configure IP addresses as shown below. Router: Fastethernet 0/0: 192.168.20.1 255.255.255.0 Fastethernet 0/1: 192.168.30.1255.255.255.0 Fastehternet 1/0: 192.168.10.1 255.255.255.0 PC0: 192.168.20.10255.255.255.0 Gateway: 192.168.20.1 DNS: 192.168.20.5 PC1: 192.168.10.10255.255.255.0 Gateway: 192.168.10.1 DNS: 192.168.20.5 PC2: 192.168.10.15255.255.255.0 Gateway: 192.168.10.1 DNS: 192.168.20.5 PC3: 192.168.10.20 255.255.255.0 Gateway: 192.168.10.1 DNS: 192.168.20.5 PC4: 192.168.30.10255.255.255.0 Gateway: 192.168.30.1 DNS: 192.168.20.5 Server0: 192.168.20.5 255.255.255.0 Gateway: 192.168.20.1 Server1: 192.168.10.5255.255.255.0 Gateway: 192.168.10.1 Applications: HTTP, FTP, and DNS are running at Server0 while only HTTP and FTP are running at Server1. Use for Server 0 and for Server 1. For the FTP account, use user ID of "server0" and password of "lab3" for FTP at server 0 . For FTP server 1 , use "server 1 " for user ID and "lab3" for the password. 1. What are the formats of standard and extended ACL syntax? Write the general ACL syntax for IP, ICMP, TCP, and UDP. (5 points) Before proceeding, make sure all PCs ping each other and access both web and ftp services at both servers. "show access-list"' can show current ACL on the router and use it to show your ACL. 2. Show screenshot of ping from PC0 to all other PCs, both website access, and both ftp servers. (5 points) Scenario 1. Allow one host PCl to access the 192.168.20.0 network. We will use standard ACL to prevent the connection from one network to another network. 3. Write your standard ACL that will allow only PC1 to 192.168.20.0 network. Show all ACL commands that you use for this question. ( 5 points) 4. Apply above ACL to interface Fa1/0 and do ping tests from PC1,PC2, and PC3 to PCO and PC4. Does it only block traffic from 192.168.10.0 network to 192.168.20.0 network? What happen and why? Explain and show your screenshot of ping results. Show all ACL commands that you use for this question. (10 points) 5. Remove ACL on Fa//0 and apply it on Fa0/0. Now do ping tests from PC1,PC2, and PC3 to PCO and PC4. Are they all successful? Explain the results with screenshots of ping tests. At this moment, PC1 should be able to ping both PCO and PC4 while all other PCs (i.e., PC2 and PC3 ) can ping only PC4. Show all ACL commands that you use for this question. (10 points) 6. Now at PC4, ping all other PCs. Which PCs can PC4 successfully ping? Why? Explain and show your ping results. ( 5 points) 7. Remove current ACL and write your new ACL to allow all traffic. But block the traffic from PC1 only to 192.168.20.0 network. Show your command and specify the interface to apply. Also include your ping tests (i.e., ping from PC1,2, and 3 to PCO and PC4, and from PC4 to PC0 ). You should include all ACL commands that you use for this question here. (10 points) 8. Remove current ACL and write new ACL to allow all traffics to 192.168.20.0 network from all outside network but not from 192.168.10.0 network. For the traffic from 192.168.10.0 network, it allows only IP addresses between 192.168.10.8 and 192.168.10.15 to 192.168.20.0 network while all other IP addresses of 192.168.10.0 network should be blocked. You should explain how your ACL satisfies the requirements and which interface should be applied your ACL. Also include your ping tests (i.e., ping from PC1, 2, and 3 to PC0 and PC4, and from PC4 to PC0). You must use Wildcard Masking bit. (Note: Your ACL should include "permit any" statement.) You should include all ACL commands that you use for this question here. (10 points) Scenario 2. Extended IP ACL We will use extended version of ACL to control the traffic more flexibly. Delete current ACL and proceed. 9. File server (FTP) at Server0 is just for internal users only (i.e., 192.168.20.0 network). All other services such as web or DNS should be allowed. However, PC0 in 192.168.20.0 network should be able to access FTP and HTTP of server1 in 192.168.10.0 network. Explain and write your ACL to accomplish it. You should show that PC0 can get web or file transfer service from the server while other PCs in 192.168.10.0 and 192.168.30.0 network can have all services but file transfer from server 0 . Show your screenshot for successful or unsuccessful services. You should include all ACL commands that you use for this question here. (10 points) 10. In addition, the admin at 192.168.20.0 network decides not to allow incoming ping traffic from outside in order to protect the network from possible attacks. Explain how it can be done this using ACL. You should explain it in high level, not just ACL commands. Write your ACL and apply it to proper interface and prove the 192.168.20.0 network blocks the ping request only while allows all other traffics such as DNS and HTTP (e.g., show successful blocking ping and FTP traffics from outside, but allowing DNS and HTTP service to outside). However, PCs in 192.168.20.0 network should be able to ping PCs in other networks (i.e., PC0 to PC1, 2, 3, or 4). Show all appropriate screenshots of ping, DNS, and HTTP results to prove that your ACL commands are successfully achieve this goal. You should include all ACL commands that you use for this question here. (Hint: ping uses couple of service types of ICMP) (10 points)









