Question
NOTE: THIS IS FROM DISCRETE MATH COURSE FOR COMPUTER SCIENCE I RECOMMEND YOU TO DO THIS ASSIGNMENT ON VISUAL STUDIO SINCE I HAVE NEVER TAKING
NOTE:
THIS IS FROM "DISCRETE MATH" COURSE FOR COMPUTER SCIENCE
I RECOMMEND YOU TO DO THIS ASSIGNMENT ON VISUAL STUDIO
SINCE I HAVE NEVER TAKING C++, I MAY HAVE SOME DIFFICULTY FOR THIS ASSIGNMENT. THEREFORE, I HOPE YOU CAN DO THIS ASSIGNMENT THOROUGHLY
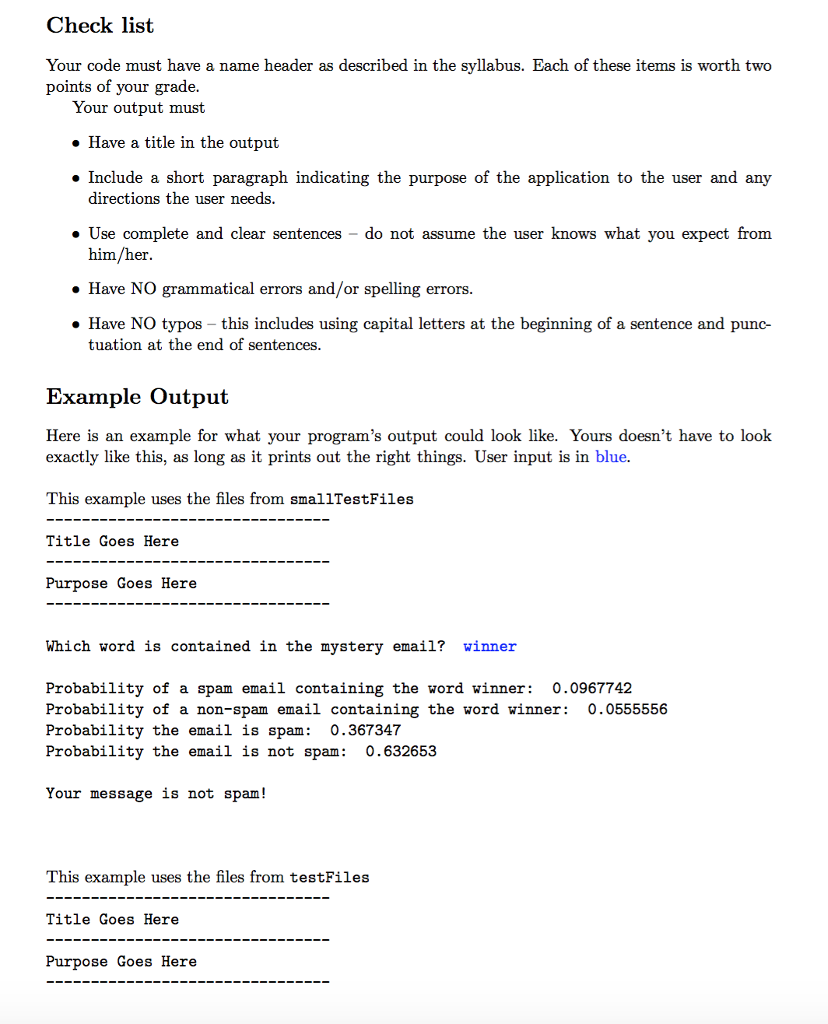
BELOW IS TWO OF THE SAMPLES TO TEST THE PROGRAM ON, WHICH IS "email1.txt" AND ""spam1.txt" FOR each folder testFiles and smallTestFiles that my professor included for this assignment.
I JUST POST TWO FOR EACH FOLDER(TESTFILES and SMALLTESTFILES) SINCE THERE ARE STILL MORE in each folder , SO I POST THEM HERE IN ORDER FOR YOU TO HAVE AN IDEA TO WRITE THE CODE ON THIS.
*From smallTestFiles folder* (Total 4 files)
email1.txt
hi, thank you so much! you're the best!
spam1.txt
you've been selected as a winner! click now to get the best anti-virus scanner!
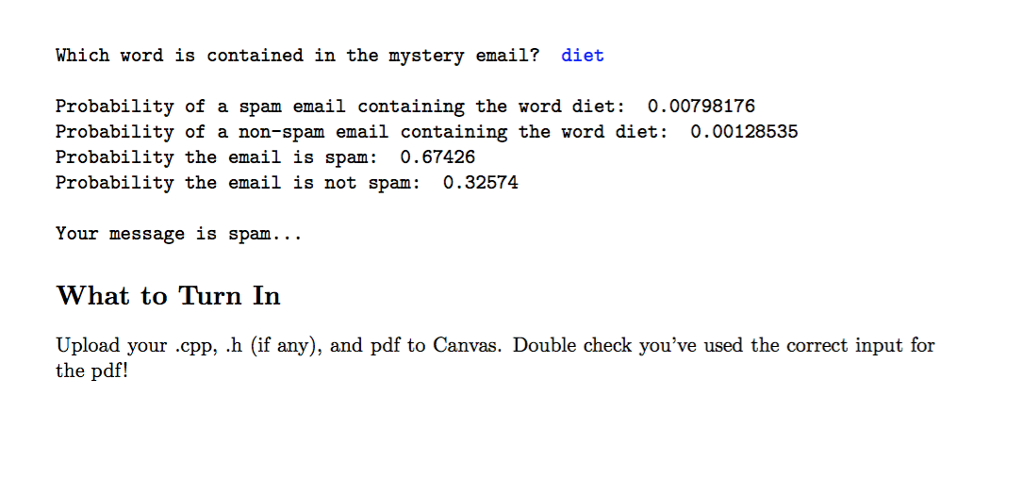
*From "testFiles" folder* (Total 10 files)
email1.txt
dear all,
on behalf of thrill company, i am glad to invite you for a luncheon party with all the senior employees, team members, and other staff members associated with the company. since according to associations policies, we have five working days, therefore we have planned to set a lunch party for saturday, 13th january 2012.
please mark your presence on this party. together, we would get an opportunity to interact with our boss, expand our contacts, learn more about our field and of course eat some mouth watering dishes. this luncheon would be held in a new york cafe situated at park lane. kindly be present by 12:00 noon so that your taste buds do not miss any of the tempting dishes being served!
i request you to confirm your presence latest by wednesday, 9th january 2012 so that we make appropriate bookings.
looking forward to see you on this thrills luncheon party!
sincerely, jacob thomas hr head thrill company
spam1.txt
it training tuition scholarships for college faculty, students and staff
national education foundation cyberlearning, a non-profit organization dedicated to bridging the digital divide since 1994, is offering "no excuse" tuition-free on-line training in information technology to the first 10,000 applicants.
nef cyberlearning courses, sponsored by the u.s. department of commerce in the federal learning exchange, have recently been acclaimed as "the best of the web" in online it training by the forbes magazine. two online course programs are available:
1) personal computing (300+ self-study and instructor-led courses including all microsoft office, web design, lotus notes, internet etc, tuition value of $3,000) for a $75 registration fee, the only cost.
2) information technology (650+ self-study and instructor-led courses, including the above and 350+ certification courses in microsoft, cisco, oracle, novell, web master etc, tuition value of $6,500) for a $270 registration fee, the only cost.
for either program, registration is valid through june 30, 2001 and there are no tuition costs for classes. the registrant receives free unlimited access to the courses, a vast online library, chat areas, certification skill tests and evaluations. this is an exceptional value and a great way for anyone to upgrade it skills and learn new skills.
to sign up, visit www.cyberlearning.org and click on "pc scholarships(300+ courses)" or click on "it scholarships (650+ courses)." then, complete the "teachers and others in education" application. manycolleges, schools and other educational organizations reimburse the training registration fee. over 5,000 educators, faculty and students have already registered.
to bridge the digital divide, nef also provides "no excuse" it training scholarships to disadvantaged school and college students and teachers throughout the nation.
please forward this information to all interested colleagues and others in education, colleges, universities and schools.
to unsubscribe, please reply with "unsubscibe" in the subject line.
about nef: the non-profit national education foundation cyberlearning has provided tuition-free it training to thousands of students, teachers, government and non-profit employees and disadvantaged individuals since 1994.
nef is well on its way to training 100,000 it professionals and a million disadvantaged students nationally through its "no excuse" it training program. nef has earned many distinctions including "the ivy league of it training," "1995 fairfax human rights award," and " a leader in bridging the digital divide."
"you are helping to empower america. i salute you for your ongoing commitment to creating a better america," --- president clinton
"congratulations on a wonderful program," --- congressional leader tom davis(r-va)
"this is an awesome opportunity. you are making a difference."-- washingtonjobs.com
"nef can make a positive difference in the lives of a great number of individuals." --- microsoft
" the best online it training program i have come across. i am using it to train my students in it certification," --- doug bertain, palo alto high school it teacher
" i just want to say thank you on behalf of the many people that benefit from your incredible benevolence." --- lilia nunez, a registrant and a digital divide program beneficiary
"i have found the cyberlearning online courses to be extremely easy and useful. i liked pre-course self-assessment and it books online and available 24/7. the course screens were interactive and made me feel as if i was in the application itself. the site looks and feels very professional. the list of courses is huge. it includes something for almost everyone. i find this to be a very worthy cause." --- ken horowitz, it training coordinator
PROMPT:



Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


