Question
on line 8, which is in bold below, find the following: package class_exercise; import java.sql.Connection; import java.sql.DriverManager; import java.sql.ResultSet; import java.sql.SQLException; import java.sql.Statement; import java.sql.PreparedStatement;
on line 8, which is in bold below, find the following:
package class_exercise;
import java.sql.Connection; import java.sql.DriverManager; import java.sql.ResultSet; import java.sql.SQLException; import java.sql.Statement; import java.sql.PreparedStatement;
public class QuestionSecurityBug { Connection getConnection() throws SQLException { Connection connection = null; try { Class.forName("com.mysql.jdbc.Driver"); } catch (final ClassNotFoundException e) { e.printStackTrace(); } connection = DriverManager.getConnection(Util.URL(), Util.ID(), Util.PWD()); return connection; }
void question1(final String owner) { Statement statement = null; ResultSet resultSet = null; try { final String query = "SELECT * FROM myTable WHERE owner= '" + owner + "'"; statement = getConnection().createStatement(); 28. resultSet = statement.executeQuery(query); while (resultSet.next()) { System.out.println(resultSet.getString("NAME")); System.out.println(resultSet.getString("PHONE")); } } catch (final SQLException e) { e.printStackTrace(); } finally { if (null != resultSet) { try { resultSet.close(); } catch (final SQLException e) { } } if (null != statement) { try { statement.close(); } catch (final SQLException e) { } } } }
}
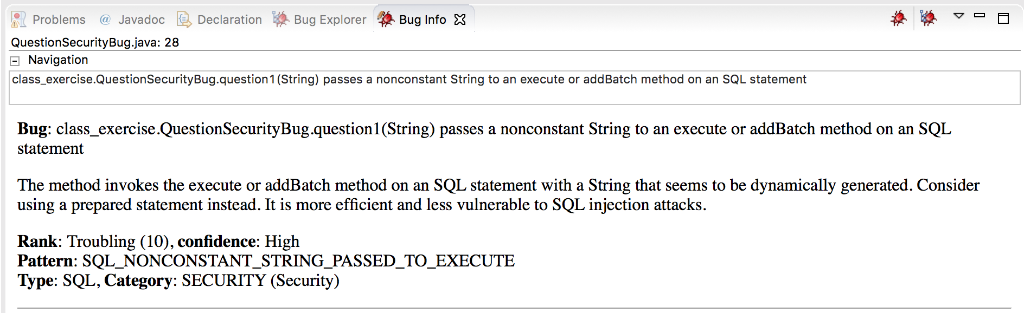
Find a security bug in the following Java source file by using an Eclipse plug-in, SpotBugs FindBugs). Method: void questionl (final String owner) Inspect the security bug based on the bug report and create a repaired method, R Problems @ Javadoc Declaration QuestionSecurityBug.java: 28 Bug ExplorerBug info X Navigation class_exercise.QuestionSecurityBug.question 1 (String) passes a nonconstant String to an execute or addBatch method on an SQL statement Bug: class_ exercise.QuestionSecurityBug.questionl(String) passes a nonconstant String to an execute or addBatch method on an SQL statement The method invokes the execute or addBatch method on an SQL statement with a String that seems to be dynamically generated. Consider using a prepared statement instead. It is more efficient and less vulnerable to SQL injection attacks. Rank: Troubling (10), confidence: High Pattern: SQL_NONCONSTANT_STRING_PASSED_TO_EXECUTE Type: SQL, Category: SECURITY (Security) ICOSTANTL STRING PASSED.TO EXECUTE
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


