
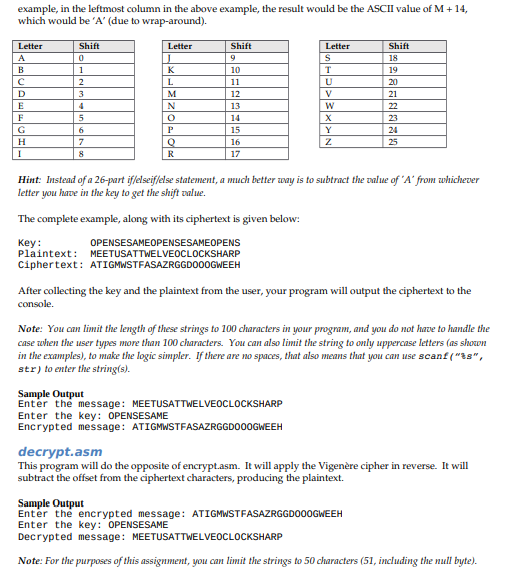
Overview In this assignment, you will create the ultimate encryption program. The program will ask the user for a message and a key, and will use that key to encrypt the message, then again to revive the original message. Part 1 (6 marks) encrypt.asm This part of the program will input two strings, with appropriate prompts. The program will then take, character by character, the original message and the key and apply the Vigenre cipher [1] (algorithm for encryption) to it. To collect a single byte from memory, try something like the following: mov dl, [rax] In the above example, dl' is an 8-bit register (actually, the low order 8 bits of the 64-bit register rdx) Similarly, there are al, bl, cl (and even ah, bh, ch, and dh. The Vigenre cipher is a relatively old idea. It takes a key of any size, which is a series of letters (eg. a word). The key is used repeatedly so that each character in the plaintext has a corresponding letter from the key. For example, here is the match-up for the key 'OPENSESAME' and the message MEETUSATTWELVEOCLOCKSHARP OPENSESAMEOPENSESAMEOPENS key Plaintext: MEETUSATTWELVEOCLOCKSHARP Note: Duplicating the key so that it is the same length as the message is one of the trickiest parts of this program. Create a sufficiently large string variable for the result (eg. duplicatedKey), copy the letters from key until you get to the mull-terminator (a character equal to zero). Keep a count of how many characters have been copied, and stop when that count reaches the message length. Whenever you get to the end of the key, go back to the first character. The letter 'O above the 'M' in the leftmost column in the above example means that your algorithm will apply a Caesar-O shift. This is a fancy way of saying that you will add 14 to the ASCII value for M (with wrap-around if the value goes beyond "Z'). A full table of the shifts is given in the table below. For Overview In this assignment, you will create the ultimate encryption program. The program will ask the user for a message and a key, and will use that key to encrypt the message, then again to revive the original message. Part 1 (6 marks) encrypt.asm This part of the program will input two strings, with appropriate prompts. The program will then take, character by character, the original message and the key and apply the Vigenre cipher [1] (algorithm for encryption) to it. To collect a single byte from memory, try something like the following: mov dl, [rax] In the above example, dl' is an 8-bit register (actually, the low order 8 bits of the 64-bit register rdx) Similarly, there are al, bl, cl (and even ah, bh, ch, and dh. The Vigenre cipher is a relatively old idea. It takes a key of any size, which is a series of letters (eg. a word). The key is used repeatedly so that each character in the plaintext has a corresponding letter from the key. For example, here is the match-up for the key 'OPENSESAME' and the message MEETUSATTWELVEOCLOCKSHARP OPENSESAMEOPENSESAMEOPENS key Plaintext: MEETUSATTWELVEOCLOCKSHARP Note: Duplicating the key so that it is the same length as the message is one of the trickiest parts of this program. Create a sufficiently large string variable for the result (eg. duplicatedKey), copy the letters from key until you get to the mull-terminator (a character equal to zero). Keep a count of how many characters have been copied, and stop when that count reaches the message length. Whenever you get to the end of the key, go back to the first character. The letter 'O above the 'M' in the leftmost column in the above example means that your algorithm will apply a Caesar-O shift. This is a fancy way of saying that you will add 14 to the ASCII value for M (with wrap-around if the value goes beyond "Z'). A full table of the shifts is given in the table below. For








