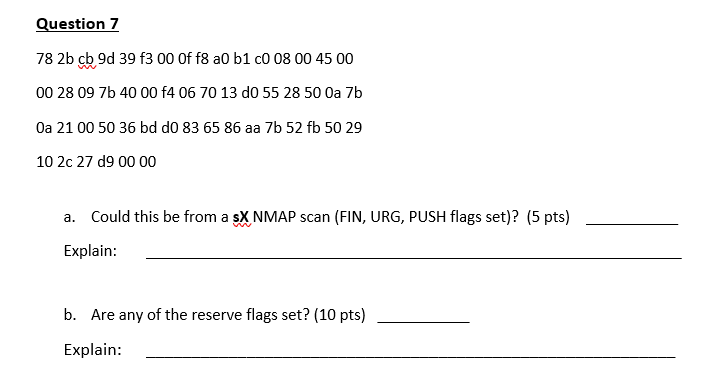
Question: Packet Notes: uestion 7 78 2b cb 9d 39 f3 00 0f f8 a0 b1 c0 08 00 45 00 00 28 09 7b 40
Packet Notes: 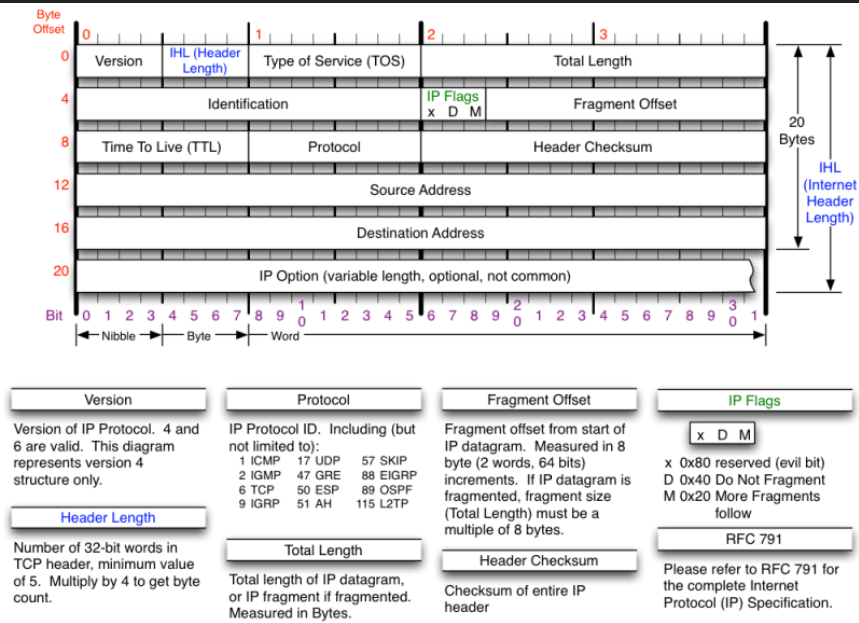
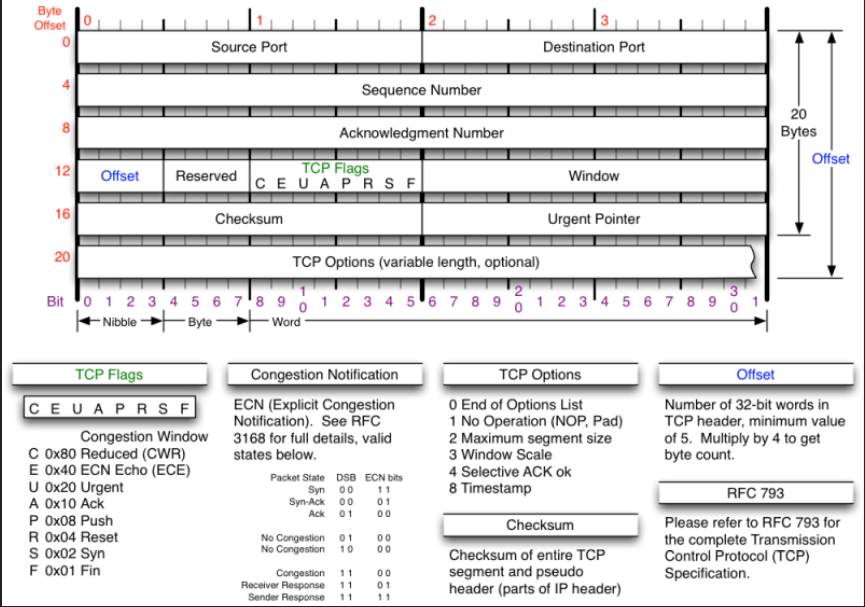
uestion 7 78 2b cb 9d 39 f3 00 0f f8 a0 b1 c0 08 00 45 00 00 28 09 7b 40 00 f4 06 70 13 d0 55 28 50 0a 7b 0a 21 00 50 36 bd d0 83 65 86 aa 7b 52 fb 50 29 10 2c 27 d9 00 00 a. Could this be from a sX NMAP scan (FIN, URG, PUSH flags set)? (5 pts) Explain: b. Are any of the reserve flags set? (10 pts) Explain: Byte 2 IHL (Header Version Type of Service (TOS) Total Length gth) P Flags x D M 4 Identification Fragment Offset 20 Bytes Time To Live (TTL) Protocol Header Checksum HL (Internet Header 12 Source Address 16 Destination Address 20 IP Option (variable length, optional, not common) 1234 56789 0 3 1 2 3'4 5678 9 o Bit 01 2 3 4567'89 Nibble Byte Word Version Protocol Fragment Offset IP Flags Version of IP Protocol. 4 and P Protocol ID. Including (but Fragment offset from start of 6 are valid. This diagram represents version4 structure only not limited to) IP datagram. Measured in 8 1 ICMP 2 IGMP 6 TCP 9 IGRP 17 UDP 47 GRE 50 ESP 51 AH 57 SKIPbyte (2 words, 64 bits) 88 EIGRP 89 OSPF 115 L2TP increments. If IP datagram is fragmented, fragment size Total Length) must be a multiple of 8 bytes. x 0x80 reserved (evil bit) D0x40 Do Not Fragment M 0x20 More Fragments Header Length RFC 791 Number of 32-bit words in TCP header, minimum value of 5. Multiply by 4 to get byte Total Length Header Checksum Please refer to RFC 791 for the complete Internet Protocol (IP) Specification. Total length of IP datagram or IP fragment if fragmented.Checksum of entire IP Measured in Bytes count. header Byte Offset 0 2 Type Code Checksum Bytes Other message specific information... 2 3 Bit 01 2 345678902 3 45678902 345 6789 01 Nibble-yeWord ICMP Message Types Checksum Type Code/Name Type Code/Name Type Code/Name Checksum of ICMP header 11 Time Exceded 0Echo Reply 3 Destination Unreachable 3 Destination Unreachable (continued) 12 Host Unreachable for TOS O TTL Exceeded 0 Net Unreachable 1 Host Unreachable 2 Protocol Unreachable 13 Communication Administratively Prohibited 4 Source Quench 5 Redirect Fragment Reassembly Time Exceeded RFC 792 12 Parameter Problenm 0 Pointer Problem Port Unreachable 4 Fragmentation required, and DF set 5 Source Route Failed 6 Destination Network Unknown 7 Destination Host Unknown 8 Source Host Isolated 9 Network Administratively Prohibited 0 Host Administratively Prohibited 11 Network Unreachable for TOS Please refer to RFC 792 for the Internet Control Message protocol (ICMP) 0 Redirect Datagram for the Network Missing a Required Operand Redirect Datagram for the Host 2 Redirect Datagram for the TOS& Network 3 Redirect Datagram for the TOS& Host14 Timestamp Reply 2 Bad Length 13 Timestamp 5 Information Request 16 Information Reply 17 Address Mask Request 8 Address Mask Reply 30 Traceroute 8 Echo 9 Router Advertisement specification. 10 Router Selection Byte 2 0 Source Port Destination Port Bytes 4 Length Checksum 2 3 Bit 012 3456 7890 12 34 5678 902 3 456 7890 Nibble Byte Word Checksum RFC 768 Checksum of entire UDP segment and pseudo header (parts of IP header) Please refer to RFC 768 for the complete User Datagram Protocol (UDP) Specification 3 Offset 0 Source Port Destination Port 4 Sequence Number 20 Bytes 8 Acknowledgment Number TCP Flags Offset Reserved Windoww CEU AP R S Checksum Urgent Pointer 20 TCP Options (variable length, optional) 2 Bit 0 1 23,4 5 6 7'8 9 o 12 3 4 5678 9 0 1 2 3 456 789 Nibble Byte TCP Flags TCP Options Offset Congestion Notification CEUA PRS FECN (Explicit Congestion Congestion Window 3168 for full details, valid 0 End of Options List 1No Operation (NOP, Pad 2 Maximum segment size Number of 32-bit words in Notification). See RFC TCP header, minimum value of 5. Multiply by 4 to get byte count. C 0x80 Reduced (CWR) E 0x40 ECN Echo (ECE) U 0x20 Urgent A 0x10 Ack P 0x08 Push R 0x04 Reset S 0x02 Syn F 0x01 Fin states below Window Scale 4 Selective ACK ok 8 Timestamp Packet State DSB ECN bits Syn 001 RFC 793 Syn-Ack 00 01 Ack 01 00 Please refer to RFC 793 for the complete Transmission Control Protocol (TCP) Specification Checksum No Congestion 01 00 No Congestion 10 00 Congestion 00 Receiver Response 1 01 Sender Response 111 Checksum of entire TCP segment and pseudo header (parts of IP header) uestion 7 78 2b cb 9d 39 f3 00 0f f8 a0 b1 c0 08 00 45 00 00 28 09 7b 40 00 f4 06 70 13 d0 55 28 50 0a 7b 0a 21 00 50 36 bd d0 83 65 86 aa 7b 52 fb 50 29 10 2c 27 d9 00 00 a. Could this be from a sX NMAP scan (FIN, URG, PUSH flags set)? (5 pts) Explain: b. Are any of the reserve flags set? (10 pts) Explain: Byte 2 IHL (Header Version Type of Service (TOS) Total Length gth) P Flags x D M 4 Identification Fragment Offset 20 Bytes Time To Live (TTL) Protocol Header Checksum HL (Internet Header 12 Source Address 16 Destination Address 20 IP Option (variable length, optional, not common) 1234 56789 0 3 1 2 3'4 5678 9 o Bit 01 2 3 4567'89 Nibble Byte Word Version Protocol Fragment Offset IP Flags Version of IP Protocol. 4 and P Protocol ID. Including (but Fragment offset from start of 6 are valid. This diagram represents version4 structure only not limited to) IP datagram. Measured in 8 1 ICMP 2 IGMP 6 TCP 9 IGRP 17 UDP 47 GRE 50 ESP 51 AH 57 SKIPbyte (2 words, 64 bits) 88 EIGRP 89 OSPF 115 L2TP increments. If IP datagram is fragmented, fragment size Total Length) must be a multiple of 8 bytes. x 0x80 reserved (evil bit) D0x40 Do Not Fragment M 0x20 More Fragments Header Length RFC 791 Number of 32-bit words in TCP header, minimum value of 5. Multiply by 4 to get byte Total Length Header Checksum Please refer to RFC 791 for the complete Internet Protocol (IP) Specification. Total length of IP datagram or IP fragment if fragmented.Checksum of entire IP Measured in Bytes count. header Byte Offset 0 2 Type Code Checksum Bytes Other message specific information... 2 3 Bit 01 2 345678902 3 45678902 345 6789 01 Nibble-yeWord ICMP Message Types Checksum Type Code/Name Type Code/Name Type Code/Name Checksum of ICMP header 11 Time Exceded 0Echo Reply 3 Destination Unreachable 3 Destination Unreachable (continued) 12 Host Unreachable for TOS O TTL Exceeded 0 Net Unreachable 1 Host Unreachable 2 Protocol Unreachable 13 Communication Administratively Prohibited 4 Source Quench 5 Redirect Fragment Reassembly Time Exceeded RFC 792 12 Parameter Problenm 0 Pointer Problem Port Unreachable 4 Fragmentation required, and DF set 5 Source Route Failed 6 Destination Network Unknown 7 Destination Host Unknown 8 Source Host Isolated 9 Network Administratively Prohibited 0 Host Administratively Prohibited 11 Network Unreachable for TOS Please refer to RFC 792 for the Internet Control Message protocol (ICMP) 0 Redirect Datagram for the Network Missing a Required Operand Redirect Datagram for the Host 2 Redirect Datagram for the TOS& Network 3 Redirect Datagram for the TOS& Host14 Timestamp Reply 2 Bad Length 13 Timestamp 5 Information Request 16 Information Reply 17 Address Mask Request 8 Address Mask Reply 30 Traceroute 8 Echo 9 Router Advertisement specification. 10 Router Selection Byte 2 0 Source Port Destination Port Bytes 4 Length Checksum 2 3 Bit 012 3456 7890 12 34 5678 902 3 456 7890 Nibble Byte Word Checksum RFC 768 Checksum of entire UDP segment and pseudo header (parts of IP header) Please refer to RFC 768 for the complete User Datagram Protocol (UDP) Specification 3 Offset 0 Source Port Destination Port 4 Sequence Number 20 Bytes 8 Acknowledgment Number TCP Flags Offset Reserved Windoww CEU AP R S Checksum Urgent Pointer 20 TCP Options (variable length, optional) 2 Bit 0 1 23,4 5 6 7'8 9 o 12 3 4 5678 9 0 1 2 3 456 789 Nibble Byte TCP Flags TCP Options Offset Congestion Notification CEUA PRS FECN (Explicit Congestion Congestion Window 3168 for full details, valid 0 End of Options List 1No Operation (NOP, Pad 2 Maximum segment size Number of 32-bit words in Notification). See RFC TCP header, minimum value of 5. Multiply by 4 to get byte count. C 0x80 Reduced (CWR) E 0x40 ECN Echo (ECE) U 0x20 Urgent A 0x10 Ack P 0x08 Push R 0x04 Reset S 0x02 Syn F 0x01 Fin states below Window Scale 4 Selective ACK ok 8 Timestamp Packet State DSB ECN bits Syn 001 RFC 793 Syn-Ack 00 01 Ack 01 00 Please refer to RFC 793 for the complete Transmission Control Protocol (TCP) Specification Checksum No Congestion 01 00 No Congestion 10 00 Congestion 00 Receiver Response 1 01 Sender Response 111 Checksum of entire TCP segment and pseudo header (parts of IP header)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


