Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Part 1. Configuring FTP Server in Packet Tracer The File Transfer Protocol (FTP) is a standard network protocol used for the transfer of computer
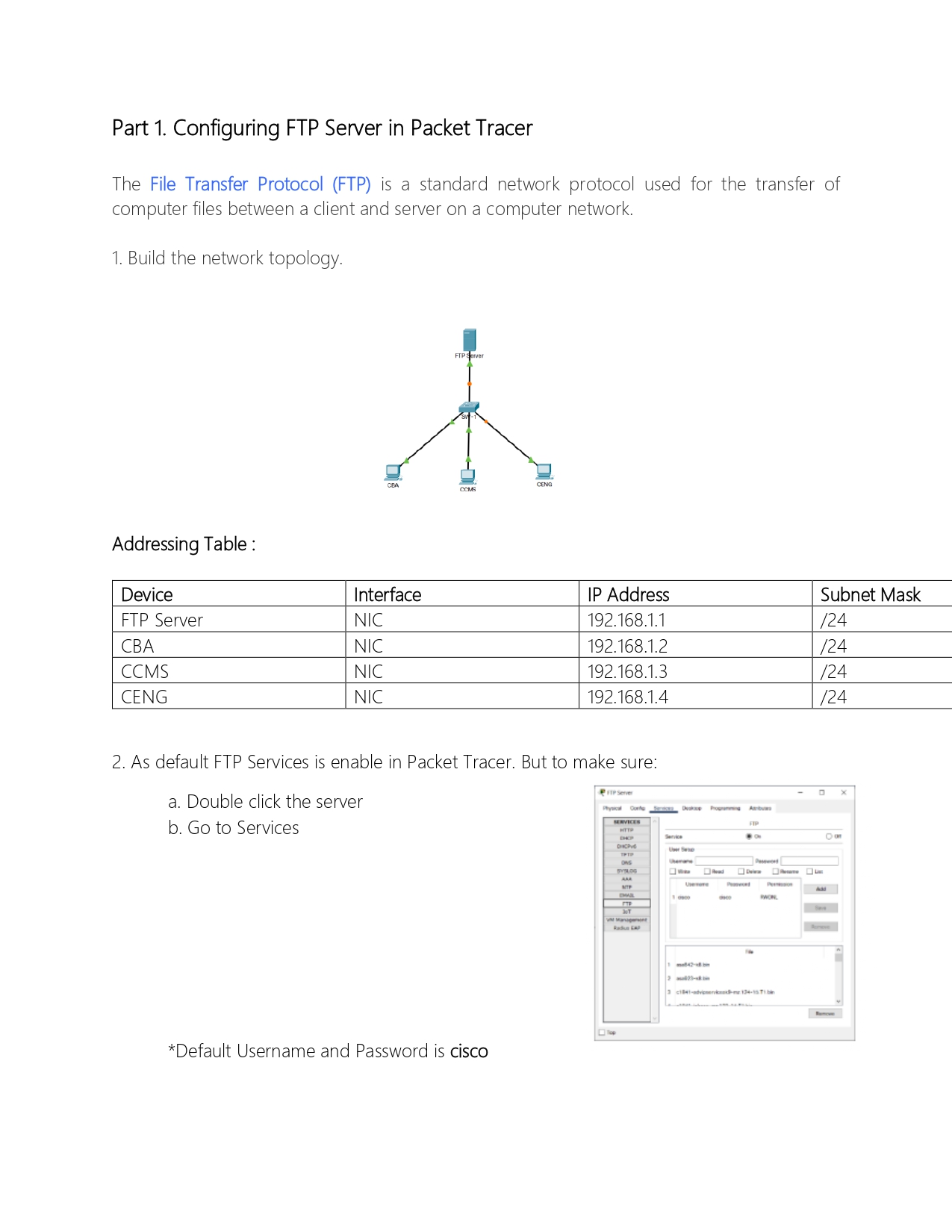


Part 1. Configuring FTP Server in Packet Tracer The File Transfer Protocol (FTP) is a standard network protocol used for the transfer of computer files between a client and server on a computer network. 1. Build the network topology. Addressing Table: Device FTP Server CBA CCMS CENG CBA FTP Server CENG CCMS Interface IP Address Subnet Mask NIC 192.168.1.1 /24 NIC 192.168.1.2 /24 NIC 192.168.1.3 /24 NIC 192.168.1.4 /24 2. As default FTP Services is enable in Packet Tracer. But to make sure: a. Double click the server b. Go to Services PFTP Server . Physical De Abus SERVICES HTTP FIP Service DHCPv6 User Sexp ONS SYSLOG Top *Default Username and Password is cisco EMA 3 T Radus CMP Read Preced P Ad WON 25- in 3 c1841-advipered-me 134-15T1 3. Create a file in the PC (CBA, CCMS and CENG). To do this: a. In the PC, open Text Editor b. Create a file. c. Save your file as CBA.txt for CBA, CCMS.txt for CCMS and CENG.txt for CENG. 4. Upload the files from the 3 PC to the FTP server. a. ftp b. put *To check other FTP commands supported by the FTP client running on the Laptop(or PC), you can use a question mark (?) on the command prompt. 5. Once file upload is successful, go to FTP Server-Services-FTP and check your file. Part 2. Configuring Port Security Step 1: Configure Port Security a) Access the command line for Switch and enable port security on ports where CBA, CCMS and CENG connected. S1(config)# interface range f0/1-2 S1(config-if-range)# switchport port-security b) Set the maximum so that only one device can access the ports. S1(config-if-range)# switchport port-security maximum 1 c) Secure the ports so that the MAC address of a device is dynamically learned and added to the running configuration. S1(config-if-range)# switchport port-security mac-address sticky d) Set the violation mode so that the ports are not disabled when a violation occurs, but a notification of the security violation is generated and packets from the unknown source are dropped. S1(config-if-range)# switchport port-security violation restrict e) Disable all the remaining unused ports. Use the range keyword to apply this configuration to all the ports simultaneously. S1(config-if-range)# interface range f0/3-24, 90/1 - 2 S1(config-if-range)# shutdown Step 2: Verify Port Security a) Verify that port security is enabled and the MAC address of PC from CBA, CENG and CETD were added to the running configuration. S1# show run begin interface b) Use port-security show commands to display configuration information S1# show port-security S1# show port-security address c) Attach Rogue Laptop to any unused switch port and notice that the link lights are red d) Enable the port and verify that Rogue Laptop can ping all the PC. After verification, shutdown the port connected to Rogue laptop. e) Disconnect CBA pc and connect Rogue Laptop to the same port as CBA originally connected. Verify that Rogue Laptop is unable to ping other PC. f) Display the port security violations for the port to which Rogue Laptop is connected. S1# show port-security interface f0/2 How many violations have occurred? g) Disconnect Rouge Laptop and reconnect CBA pc. Verify CBA can ping CETD and CCMS Why is CBA able to ping other PC, but the Rogue laptop is not?
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


