Answered step by step
Verified Expert Solution
Question
1 Approved Answer
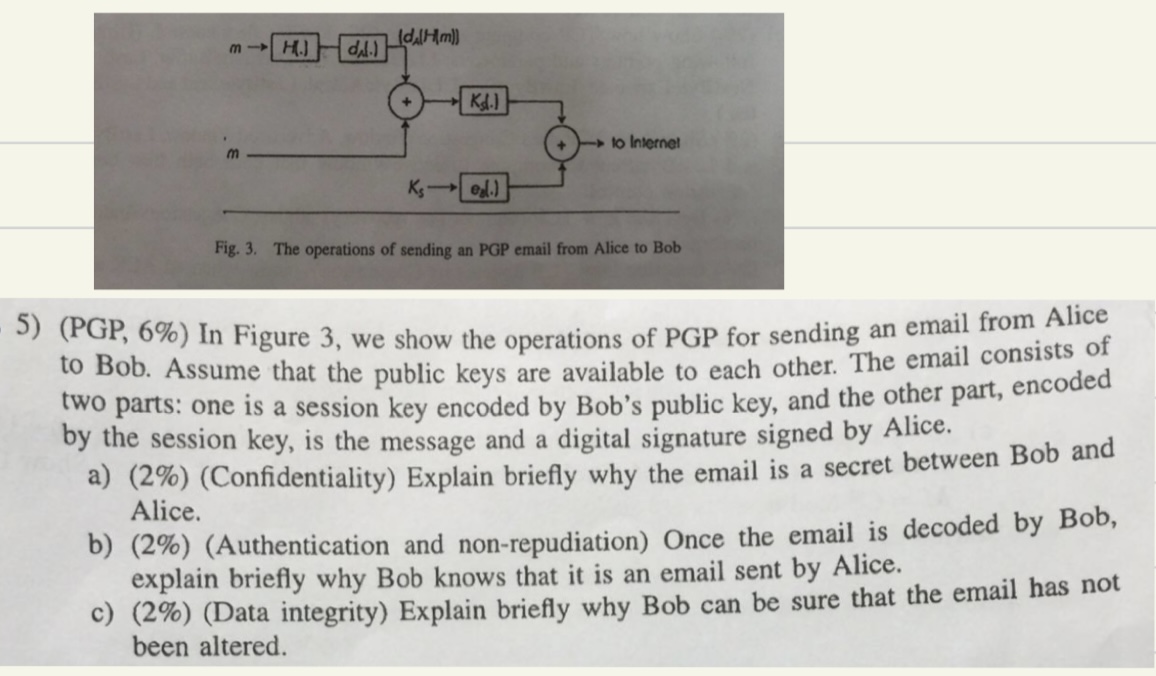
( PGP , 6 % ) In Figure 3 , we show the operations of PGP for sending an email from Alice to Bob. Assume
PGP In Figure we show the operations of PGP for sending an email from Alice
to Bob. Assume that the public keys are available to each other. The email consists of
two parts: one is a session key encoded by Bob's public key, and the other part, encoded
by the session key, is the message and a digital signature signed by Alice.
aConfidentiality Explain briefly why the email is a secret between Bob and
Alice.
bAuthentication and nonrepudiation Once the email is decoded by Bob,
explain briefly why Bob knows that it is an email sent by Alice.
cData integrity Explain briefly why Bob can be sure that the email has not
been altered.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


