Please use C programming and comment on how to run the program. Also please show a snipit of results, but please do not post snipit of actual program to run.
Instructions nay seem long, but it is just to explain what is required.
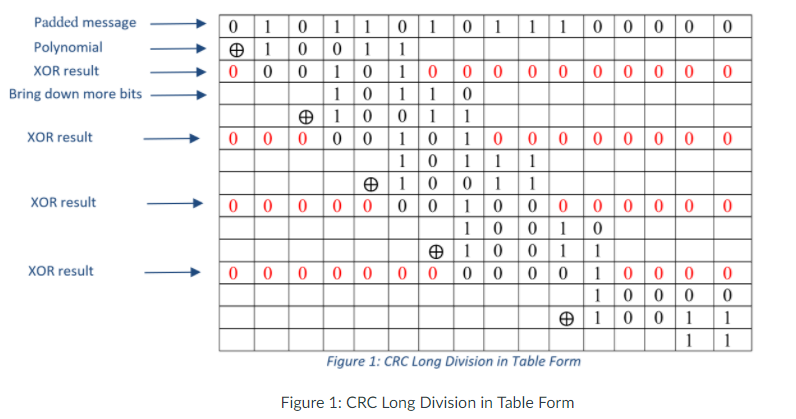

Programming Assignment 2: Cyclic Redundancy Check (CRC) The pdf version of this description is here 1. Introduction In this programming assignment, you will implement Cyclic Redundancy Check (CRC). CRC is one of the popular methods of the integrity check. It has been used in network transmission. The details of CRC was addressed in L17: Integrity Check and Secure Hash. You can refer to slides N07-8 of "17-Integrity Check and Secure Hash.pptx" and "17b-CRC Example.pptx" In the assignment you will implement both CRC calculation and CRC verification. As shown in the example in "17b-CRC Example.pptx", CRC calculation is a long division, where the input message in binary form (with padding) is dividend and a polynomial in binary form is the divisor. In the process of long division, XOR instead of regular subtraction is used. The polynomial is usually a fixed value. In this assignment, you will use the following polynomial. Polynomial: 1100 1101 1010 1 As shown in the example in "17b-CRC Example.pptx", we must pad the input message with a serials of zeros. The number of the padding zeros depends on the length of polynomial. Number of padding zeros-length of polynomial -1 Programming Assignment 2: Cyclic Redundancy Check (CRC) The pdf version of this description is here 1. Introduction In this programming assignment, you will implement Cyclic Redundancy Check (CRC). CRC is one of the popular methods of the integrity check. It has been used in network transmission. The details of CRC was addressed in L17: Integrity Check and Secure Hash. You can refer to slides N07-8 of "17-Integrity Check and Secure Hash.pptx" and "17b-CRC Example.pptx" In the assignment you will implement both CRC calculation and CRC verification. As shown in the example in "17b-CRC Example.pptx", CRC calculation is a long division, where the input message in binary form (with padding) is dividend and a polynomial in binary form is the divisor. In the process of long division, XOR instead of regular subtraction is used. The polynomial is usually a fixed value. In this assignment, you will use the following polynomial. Polynomial: 1100 1101 1010 1 As shown in the example in "17b-CRC Example.pptx", we must pad the input message with a serials of zeros. The number of the padding zeros depends on the length of polynomial. Number of padding zeros-length of polynomial -1












