Answered step by step
Verified Expert Solution
Question
1 Approved Answer
please answer all questions. Tutorial 05 (1) Use Caesar Cipher and apply brute force to decrypt the following ciphertext. Clearly show all workings in your
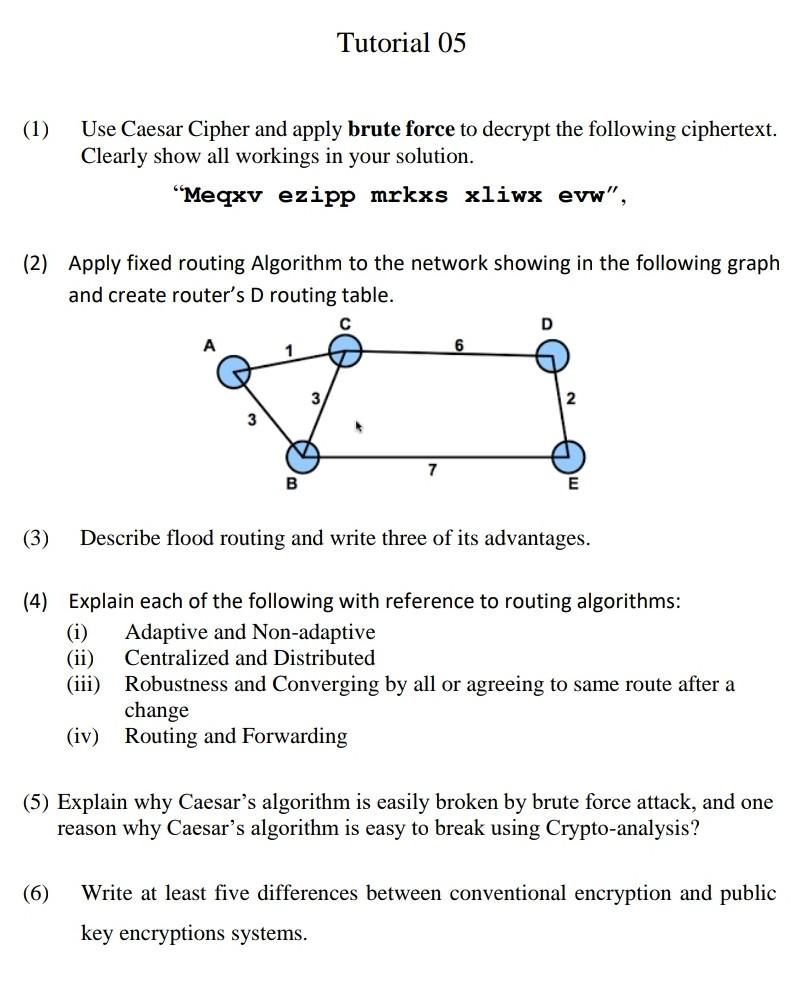
please answer all questions.
Tutorial 05 (1) Use Caesar Cipher and apply brute force to decrypt the following ciphertext. Clearly show all workings in your solution. Meqxv ezipp mrkxs xliwx evw", (2) Apply fixed routing Algorithm to the network showing in the following graph and create router's D routing table. D 6 3 3 VA B (3) Describe flood routing and write three of its advantages. (4) Explain each of the following with reference to routing algorithms: (i) Adaptive and Non-adaptive (ii) Centralized and Distributed (iii) Robustness and Converging by all or agreeing to same route after a change (iv) Routing and Forwarding (5) Explain why Caesar's algorithm is easily broken by brute force attack, and one reason why Caesar's algorithm is easy to break using Crypto-analysis? (6) Write at least five differences between conventional encryption and public key encryptions systemsStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


