Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Question 9 In computer forensics, in order to show a file is original, once we get the artifact, we may use the hash function
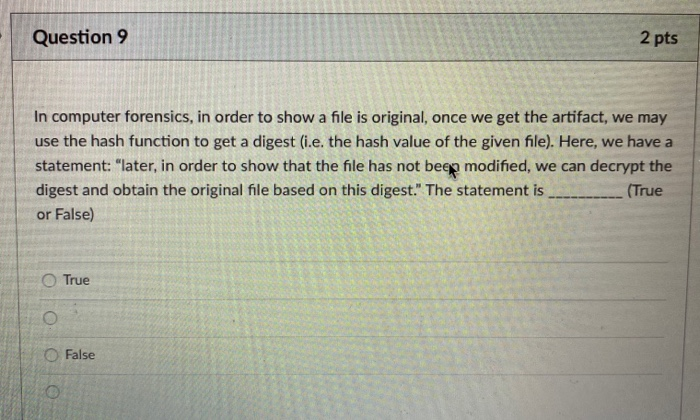
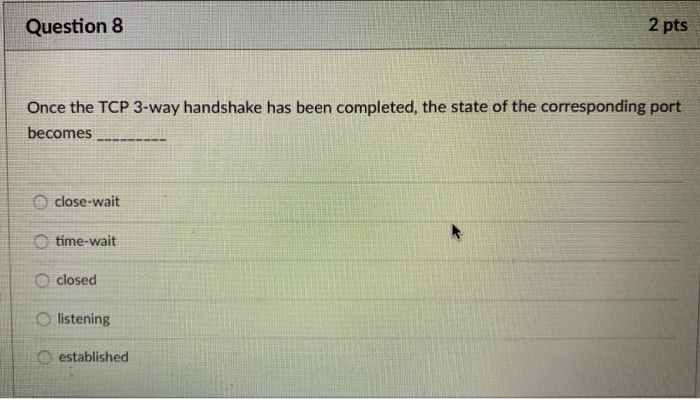
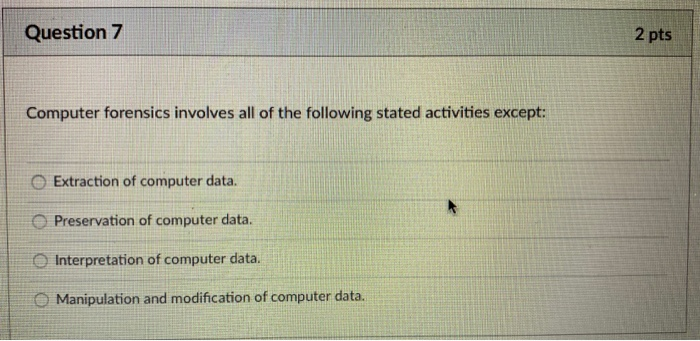
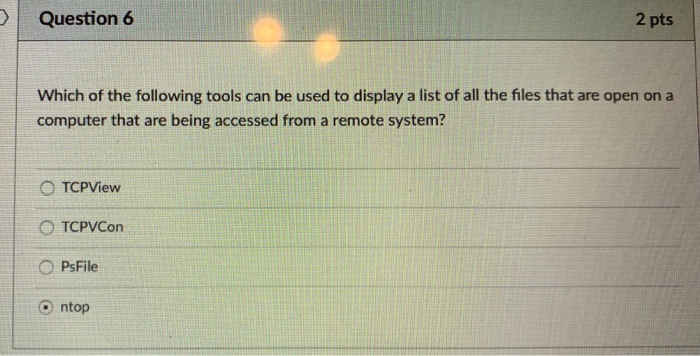
Question 9 In computer forensics, in order to show a file is original, once we get the artifact, we may use the hash function to get a digest (i.e. the hash value of the given file). Here, we have a statement: "later, in order to show that the file has not been modified, we can decrypt the digest and obtain the original file based on this digest." The statement is (True or False) 0 0 0 True 2 pts O False Question 8 Once the TCP 3-way handshake has been completed, the state of the corresponding port becomes close-wait time-wait closed Olistening 2 pts established Question 7 Computer forensics involves all of the following stated activities except: Extraction of computer data. Preservation of computer data. Interpretation of computer data. Manipulation and modification of computer data. 2 pts D Question 6 Which of the following tools can be used to display a list of all the files that are open on a computer that are being accessed from a remote system? OTCPView OTCPVCon OPsFile 2 pts ntop Question 9 In computer forensics, in order to show a file is original, once we get the artifact, we may use the hash function to get a digest (i.e. the hash value of the given file). Here, we have a statement: "later, in order to show that the file has not been modified, we can decrypt the digest and obtain the original file based on this digest." The statement is (True or False) 0 0 0 True 2 pts O False Question 8 Once the TCP 3-way handshake has been completed, the state of the corresponding port becomes close-wait time-wait closed Olistening 2 pts established Question 7 Computer forensics involves all of the following stated activities except: Extraction of computer data. Preservation of computer data. Interpretation of computer data. Manipulation and modification of computer data. 2 pts D Question 6 Which of the following tools can be used to display a list of all the files that are open on a computer that are being accessed from a remote system? OTCPView OTCPVCon OPsFile 2 pts ntop Question 9 In computer forensics, in order to show a file is original, once we get the artifact, we may use the hash function to get a digest (i.e. the hash value of the given file). Here, we have a statement: "later, in order to show that the file has not been modified, we can decrypt the digest and obtain the original file based on this digest." The statement is (True or False) 0 0 0 True 2 pts O False Question 8 Once the TCP 3-way handshake has been completed, the state of the corresponding port becomes close-wait time-wait closed Olistening 2 pts established Question 7 Computer forensics involves all of the following stated activities except: Extraction of computer data. Preservation of computer data. Interpretation of computer data. Manipulation and modification of computer data. 2 pts D Question 6 Which of the following tools can be used to display a list of all the files that are open on a computer that are being accessed from a remote system? OTCPView OTCPVCon OPsFile 2 pts ntop Question 9 In computer forensics, in order to show a file is original, once we get the artifact, we may use the hash function to get a digest (i.e. the hash value of the given file). Here, we have a statement: "later, in order to show that the file has not been modified, we can decrypt the digest and obtain the original file based on this digest." The statement is (True or False) 0 0 0 True 2 pts O False Question 8 Once the TCP 3-way handshake has been completed, the state of the corresponding port becomes close-wait time-wait closed Olistening 2 pts established Question 7 Computer forensics involves all of the following stated activities except: Extraction of computer data. Preservation of computer data. Interpretation of computer data. Manipulation and modification of computer data. 2 pts D Question 6 Which of the following tools can be used to display a list of all the files that are open on a computer that are being accessed from a remote system? OTCPView OTCPVCon OPsFile 2 pts ntop
Step by Step Solution
★★★★★
3.50 Rating (173 Votes )
There are 3 Steps involved in it
Step: 1
The detailed answer for the above question is provided below 6 The correct answer is c PsFile PsFile is a commandline utility that displays a list of files that are open on a computer that are being a...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


