Question
Please help identify THREE SECURITY VULNERABILITIES of the below authentication protocol!!!! Thanks List and explain 3 security vulnerabilities of the below authentication protocol Protocol Specification
Please help identify THREE SECURITY VULNERABILITIES of the below authentication protocol!!!!
Thanks
List and explain 3 security vulnerabilities of the below authentication protocol
Protocol Specification In order to have the functionalities described above, you need to implement the following protocol upon TCP between the client and server: 1. The client sends a RSHELL_REQ message that includes the clients ID and the shell command to the server.
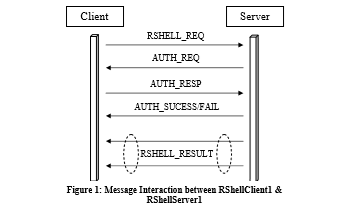
2. The server responds with an AUTH_REQ message the client asking the client to provide the password.
3. The client sends an AUTH_RESP message to the server responding with the SHA1 hash of its password.
4. The server verifies the received SHA1 hash with the SHA1 hash of the password in the
5. If the client receives AUTH_FAIL message from the server, it should print out an error message Authentication failed and exit gracefully. If the client receives AUTH_SUCESS message, it should print out the shell command result received from RSHELL_RESULT message(s). Here the server may send one or multiple RSHELL_RESULT messages depending on the volume of the result. The client should be able to handle multiple RSHELL_RESULT messages. Note, the client and server could repeat the above steps. The sever should authenticate the client for the first shell command request and remember the authentication status of the client ID for 60 seconds. In other words, the server should not ask the client for authentication if it has been successfully authenticated within past 60 seconds. Message Format Figure 2 illustrates the format of all the messages of the protocol. Each message starts with the 1-byte type field, then the 2-byte payload length field that contains the number of bytes of the payload that is right after. The payload is of variable length depending on the message type. The ID field is of fixed length of 16 bytes. It contains a string of maximum length 15 bytes that denotes the user ID (e.g., Alice). The ID string is null terminated.
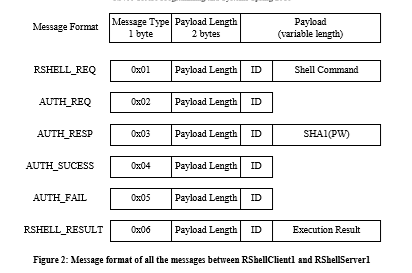
For message RSHELL_REQ, the Shell Command is simply the shell command the client is trying to execute at the remote host (e.g., pwd). It is null terminated string. For message AUTH_RESP, the SHA1(PW) is the 20 byte (160 bits) SHA1 hash of the IDs password. Note the SHA1(PW) hash is random binary value, you should treat it as raw byte stream. For message RSHELL_RESULT, the Execution Result is simply the execution result of the shell command at the remote host. Normally it should be printable ascii string. But it could contain unprintable char (e.g., if you trying to display a binary file). You want to make sure to print every byte in the Execution Result even if there is null in the middle.
Client Server RSHELL _REQ AUTH REQ AUTH RESP AUTH SUCESS FAIL RSHELL RESULT Figure 1: Message Interaction between RShelClientl & erverl Client Server RSHELL _REQ AUTH REQ AUTH RESP AUTH SUCESS FAIL RSHELL RESULT Figure 1: Message Interaction between RShelClientl & erverlStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


