Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Please help with this first question (in the first picture ).. Attached in the second, third, and fourth pictures are an example code that I've
Please help with this first question (in the first picture ).. Attached in the second, third, and fourth pictures are an example code that I've learned, id like you to follow it exactly for these questions and use it as a guide. Please only follow the code I've attached with no outside material.

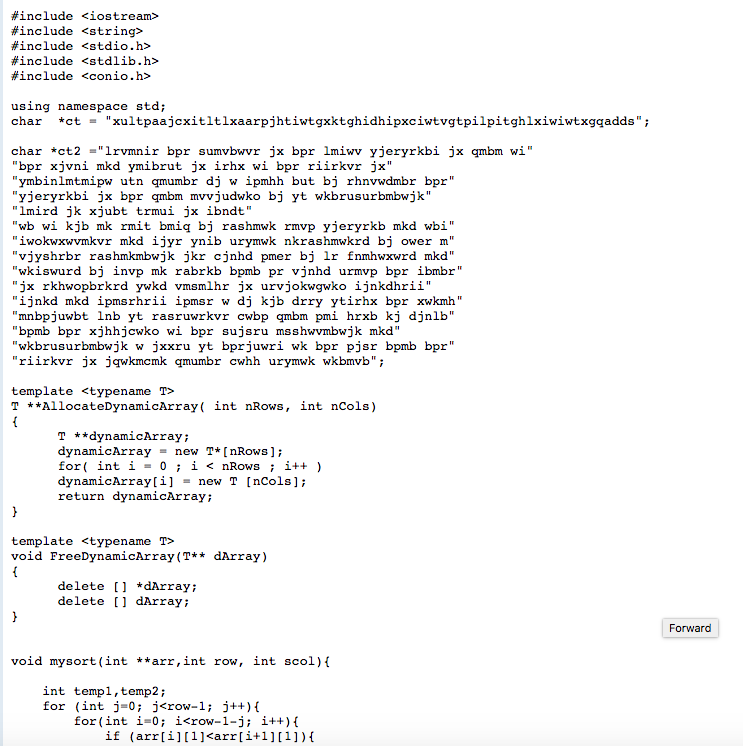
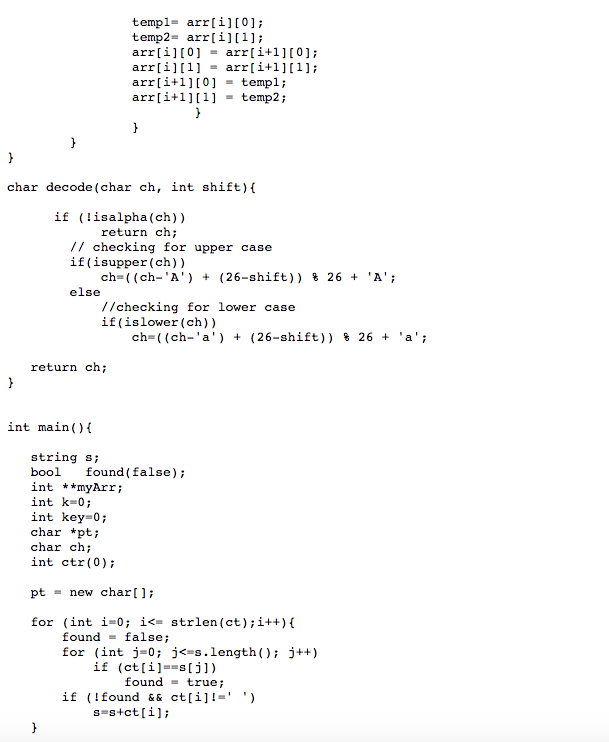
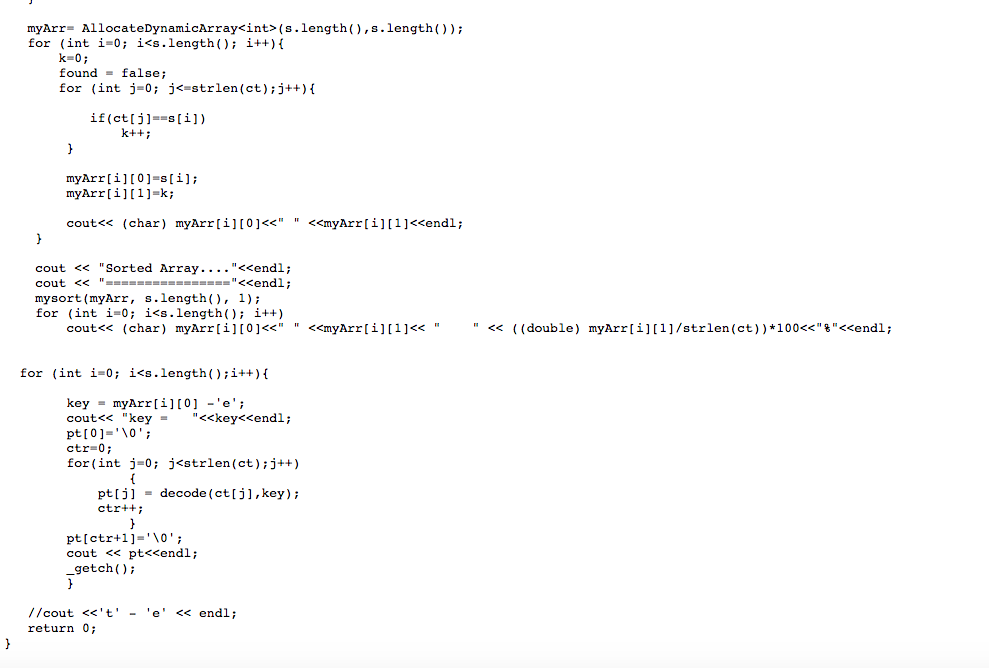
Question 1 In cryptography, a Caesar cipher, also known as Caesar's cipher, the shift cipher, Caesar's code or Caesar shift, is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with a left shift of 3, D would be replaced by A, E would become B, and so on. The method is named after Julius Caesar, who used it in his private correspondence. The encryption step performed by a Caesar cipher is often incorporated as part of more complex schemes, such as the Vigenre cipher, and still has modern application. As with all single alphabet substitution ciphers, the Caesar cipher is easily broken and in modern practice offers essentially no communication security. Generally speaking, it is a great exercise to understand crypto, and for our purposes, it deals with various concepts for learning a new programming language. The Caesar Cipher, the Multiplication Cipher and the Linear Cipher have one property in common. They all fall in the category of Monoalphabetic Ciphers: "Same plain letters are encoded to the same cipher letter." I.e. in the Caesar Cipher each "a" turned into "d", each "b" turned into "e", etc. The following holds true for each of the above Ciphers: Although letters are changed the underlying letter frequencies are not! If the plain letter "a" occurs 10 times its cipher letter will do so 10 times. Therefore, ANY Monoalphabetic Cipher can be broken with the aid of letter frequency analysis. To compute the relative frequencies of each letter in a cipher text simply count the occurrences of the letter in the text. Afterwards compare the letter frequencies with those of the English language (assuming that the cipher text stems from an English plain text). Remember that: a) The most frequent letter of the English language is "e" (with about 12%) followed by tio,an,sr which is very helpful to break the cipher text. b) The longer the cipher text the better do the counted letter frequencies converge to the actual English plain letter frequencies. http://en.wikipedia.org/wiki/Caesar cipher The Problem We received the following ciphertext which was encoded with a shift cipher: xultpaajcxititixaarpjhtiwtexktghidhipxciwtvgtpilpitghlxiwiwtxeqadds 1. Perform an attack against the cipher based on a letter frequency count: How many letters do you have to identify through a frequency count to recover the key? What is the cleartext? 2. Who wrote this message? - Hint: Please print the occurrences of each letter and then the different plaintext outputs based on different keys. Try to do it with the frequencies - it will work in this case. #include
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


