Answered step by step
Verified Expert Solution
Question
1 Approved Answer
please send screen shots and other information Case Project 2-2: Install and Use Wireshark Wireshark is a free, open source network protocol analyzer that can

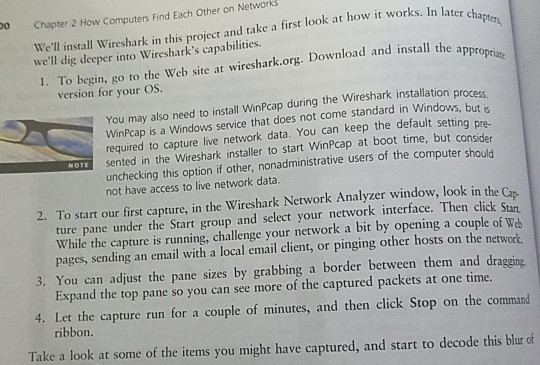


please send screen shots and other information
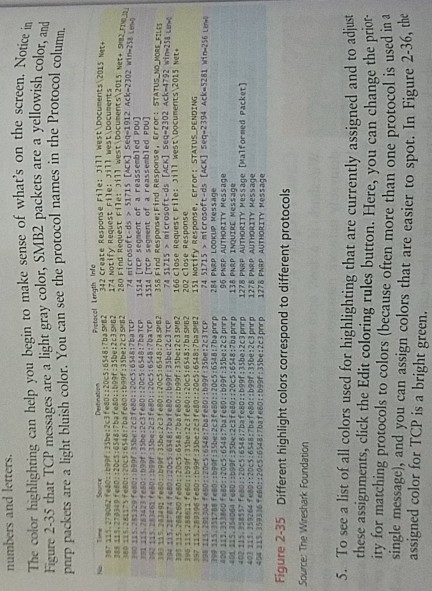
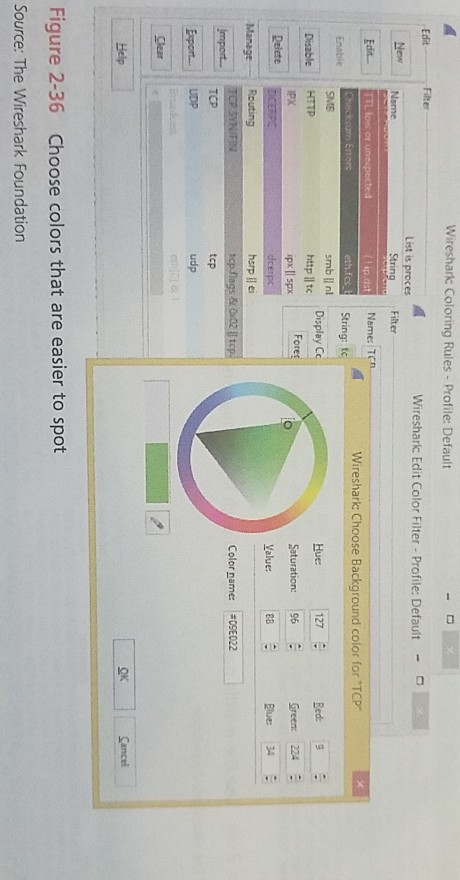
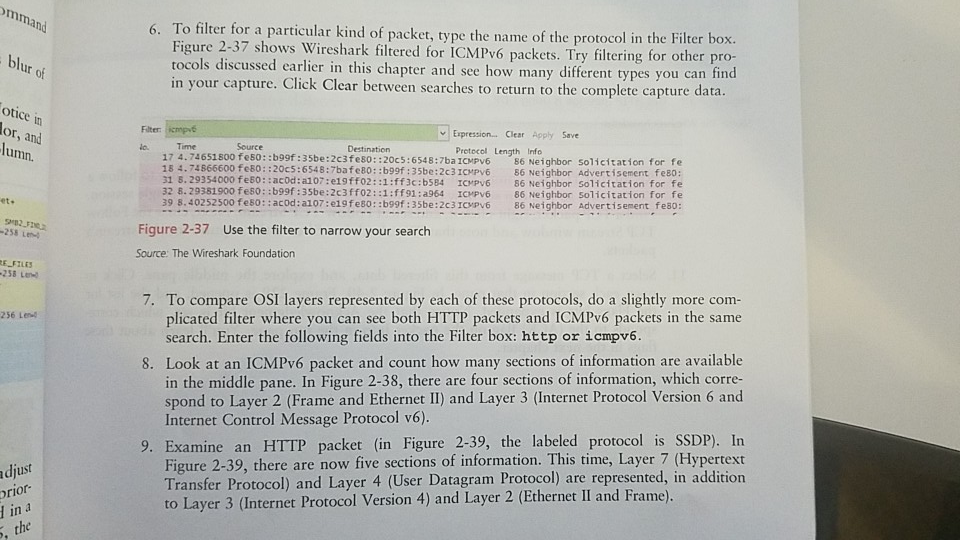
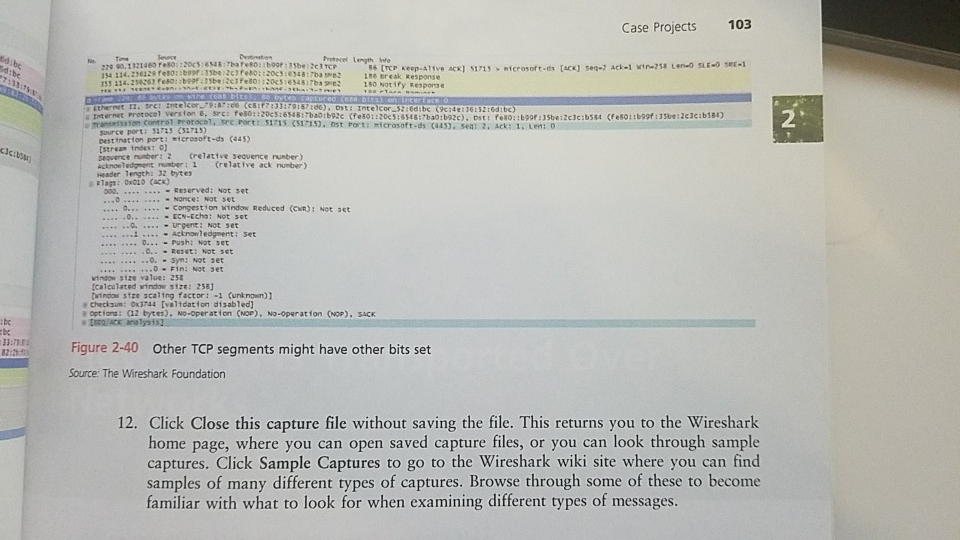
Case Project 2-2: Install and Use Wireshark Wireshark is a free, open source network protocol analyzer that can help demystify network messages and help make the OSI model a little more tangi- E PROECTS ble. Using Wireshark for the first time can be an epiphany experience for you. You can study the OSI layers, all of the information that is added to every message, and all of the messages that have to go back and forth just to bring up a Web page or even just to connect to the network. It all becomes much more real when you see how many packets Wir- eshark collects during even a short capture. Chapter 2 How Computers Find Each Other on Networks We'll install Wireshark in this project and take a first look at how it works. In later 1. To begin, go to the Web site at wireshark.org. Download and install the appro 0 cha Pter, dig deeper into Wireshark's capabilities. version for your OS You may also need to install WinPcap during the Wireshark installation process WinPcap is a Windows service that does not come standard in Windows, but required to capture live network data. You can keep the default settin g pre- WOTE sented in the Wireshark installer to start WinPcap at boot time, but consider unchecking this option if other, nonadministrative users of the computer should not have access to live network data. 2. To start our first capture, in the Wireshark Network Analyzer window, look in the Cap ture pane under the Start group and select your network interface. Then click Stat While the capture is running, challenge your network a bit by opening a couple of We pages, sending an email with a local email client, or pinging other hosts on the network 3. You can adjust the pane sizes by grabbing a border between them and dragging Expand the top pane so you can see more of the captured packets at one time. 4. Let the capture run for a couple of minutes, and then click Stop on the command ribbon Take a look at some of the items you might have captured, and start to decode this blur of numbers and letters The color highlighting can help you begin to make sense of what's on the screen Figure 2-35 that TCP messages are a light gray color, SMB2 packets are a yellowish color pnrp packets are a light bluish color. You can see the protocol names in the Protocol c umn. Prctocel Lerngth Infe 342 create Response File: 3i1 westDocuments 12015 Net feso::b09f:33be:2c39 02 174 Notify Request File: J111 west\pocum 280 Find Request File: 3111 west 74 microsoft-ds > 51715 [ACK]Seq-1912 Ack-2302 wir-2511M nts)2015 Net+ 982F :35be:2c3fe8o::20c3:6548:7ba TCP 5:6548:7baTCP 1514 [TCP segnent of a reassenbled Pou) 115 283462 80:bof:35be:2c3 feeD::20c5:6543:7baTC 1514 [TCP Segment of a reass 358 Find Response:Find Respose, Error: STA microsoft-ds [ACK] Seq-2302 Ack"4792 win-254L 74 51715 202 Close 151 > :120c5:6348:7bafeld: 268250 fes0: :205:6548:7bafe80::b99f:3sbe:2c3 3 52 166 Close Request File: 111 west\pocuments 2015 Net. Response Notify 74 51715> nicrosoft-ds [ACK] Seq-2394 Ack-5281 Win-256 Le feS0::b9of:3Sbe:2c3fet::20C5 : 6545: 7bag E2 Response. Error: STATUS-PENDING 20c5 6548 768febD: 284 PNRP LOOKUP Message 113 15.254064 fest 96 PNRF AUTHORITY Message f:3sbe:2cafel0::20c5:6548:7baprep 135 phAP INQUIRE Message 401 211.359264 fes::20c5:6548:7bafes0: 404 115. 359116 ft ::b99f:35be:2C3pmrp 0: :20c5:6543; 7bate80: :b99f:35be:2c3pnrP 1275 PHRP AUTHORITY Hessage 1278 PNRP AUTHORITY Message Figure 2-35 Different highlight colors correspond to different protocols Source: The Wireshark Foundation 5. To see a list of all colors used for highlighting that are currently assigned and to adjust these assignments, click the Edit coloring rules button. Here, you can change t ity for matching protocols to colors (because often more than one protocol is us single message), and you can assign colors that are easier to spot. In Figure 2 assigned color for TCP is a bright green. he priot Wireshark Coloring Rules - Profile: Default Edid Wireshark Edit Color Filter Profile: Default List is proces String Name: T ITLlon o Wireshark Choose Background color for TCP SME Display C 127 http |l tc pxII spx Hue Saturation: 196 Yalue Disable HTTP Fores Green 224 PX hsrp l ei Colorame: #09E022 - mpor TCP tcp CK Figure 2-36 Choose colors that are easier to spot Source: The Wireshark Foundation mmand 6. To filter for a particular kind of packet, type the name of the protocol in the Filter box. Figure 2-37 shows Wireshark filtered for ICMPv6 packets. Try filtering for other pro- tocols discussed earlier in this chapter and see how many different types you can find in your capture. Click Clear between searches to return to the complete capture data. bl lir otice in or, and lumn. Expression.. Clear Apply Save Protocol Length Info Filter lo. Source 17 4.74651800 fe50: :b99f:35be:2c3feso: :20c5:6548:7ba ICMPV6 86 Neighbor soliitation for fe 18 4.74866600 fe80::20c5:6548:7bafe80::b99f:35be:2c3ICPV6 86 Neighbor Advertisement feso: 31 5.29354000 feso::acod:a107:e19ff02::l:ff3c:b584 ICPv6 86 Neighbor solicitation for fe 32 8.29381900 fes0: :b99f :35be:2c3ffo2::1 :ff91:a964 ICHPv6 86 Neighbor solicitation for fe 39 8.40252500 feso::acod:al07:e19fes0::b99f:35be:2c3ICPV6 86 Neighbor Advertisement fe8o: et. Figure 2-37 Use the filter to narrow your search 258 Le Source: The Wireshark Foundation E FILES 7. To compare OSI layers represented by each of these protocols, do a slightly more com- plicated filter where you can see both HTTP packets and ICMPv6 packets in the same search. Enter the following fields into the Filter box: http or 256 Ler Look at an ICMPv6 packet and count how many sections of information are available in the middle pane. In Figure 2-38, there are four sections of information, which corre- spond to Layer 2 (Frame and Ethernet II) and Layer 3 (Internet Protocol Version 6 and Internet Control Message Protocol v6). 8. 9. Examine an HTTP packet (in Figure 2-39, the labeled protocol is SSDP). In Figure 2-39, there are now five sections of information. This time, Layer 7 (Hypertext Transfer Protocol) and Layer 4 (User Datagram Protocol) are represented, in addition to Layer 3 (Internet Protocol Version 4) and Layer 2 (Ethernet II and Frame). rior in a the 102 Chapter 2 How Computers Find Each Other on Networks Epression.. Chear Apply Save e191:a964 from 9c:se:36:52:d bc bao : b92c from 9e :4e:36:52:6d : bc Tane Source Protecel tength Infe o: :acod:a107:e SSDP 320 HTTP/1.1 Figure 2-38 Use the middle pane to dig into each layer's headers Source: The Wireshark Foundation VIErpresser. Clear Apply Save Source for feso: :20c5:6548:7bao:b92c from 9c:4e:36:52:6d:b0 t feso::acod:a107:e191: 320 NOTIFYHTTP/.1 Frane 102: 375 bytes on wire (3000 bits), 375 bytes captured (3000 bits) on interface o on 4, srci 192.168.1.1 (192.168.1.1), Dat: 239.255.255.250 (239.255.255.250) Fiqure 2-39 This HTTP message is using UDP a rthernet 11, src: Cisco-4:08:78 (00123:60:3e:08278), ost: r Internet Pretocol version 4. e user batagran sre: 192 168.1.1 (L92.168.1.1), 0st: 239. 253.253. 250 (239.255.235,25o) rc port: ssdp (I 9002 tagran Protoco Figure 2-39 This HTTP message is using UDP Source: The Wireshark Foundation 10. Recail that rocP is a connection-oriented protocol. You can filter a capture to follow a stream so you can see how these messages go back and forth for a single session. Find a TCP packet, right-click it, and select Follow TCP Stream. Next, close the Follow TCP TCP Stream window and note that Wireshark has filtered the capture for this streams packets 11. Select a TCP message from this filtered data, and explore the middle pane. Click to open each section in that pane. In Figure 2-40, Frame 229 is opened, and the list for the Flags bits is expanded. Notice that the Acknowledgment bit is set, which corre- sponds to the (ACK) flag on the packet Info in the top pane. You'll learn about these flags in the next chapter. Case Projects 103 Fretecel Length Infe 70 90.1321460 Fe80:220c3:63487bafes0:boot :33be:2c3 TCP 1s6 Break kesponse 33:791870)Dt: Intelcor 52:6dtbc (9cidei1615216dibe e mammiss ton contrat ocO re Port: 171S 31715), 0st Port: microsoft-ds C443), sea: 2, Ack: 1. Len: o 2 souree port:32715 (32713) pest tnation port: eicrosoft-ds (443) tstream index: 0) seqvence number: 2 Crelative sequence number) cknowedgment number: i (relative ack number) Header Tength: 32 bytes 000. Reserved: Not set once: Not set ...Congest1on window Reduced (ChR): Not set 0.ECN-Echo: Not set ...0..-Push: Not set -Fin: Not set vindow size valua: 252 caloulated rtndow 126: 258 rmoor 3tzn scaling factor: .1 (urkr own) y checksum: Ox3744 [validat fon disabled] #optios: (12 bytes), wo-operation (OP), NO-Operation (OP), SCK :bc bc 13:7 Figure 2-40 Other TCP segments might have other bits set Source: The Wireshark Foundation 12. Click Close this capture file without saving the file. This returns you to the Wireshark home page, where you can open saved capture files, or you can look through sample captures. Click Sample Captures to go to the Wireshark wiki site where you can find samples of many different types of captures. Browse through some of these to become familiar with what to look for when examining different types of messagesStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


