Please type answer. Thanks
A Penetration Tester evaluates the security of an information infrastructure by intentionally, and safely, exploiting vulnerabilities.
Take on the role of Penetration Tester for GOOGLE
Use the Penetration Testing Plan Template to create a 3- to 4-page Penetration Testing Plan for GOOGLE
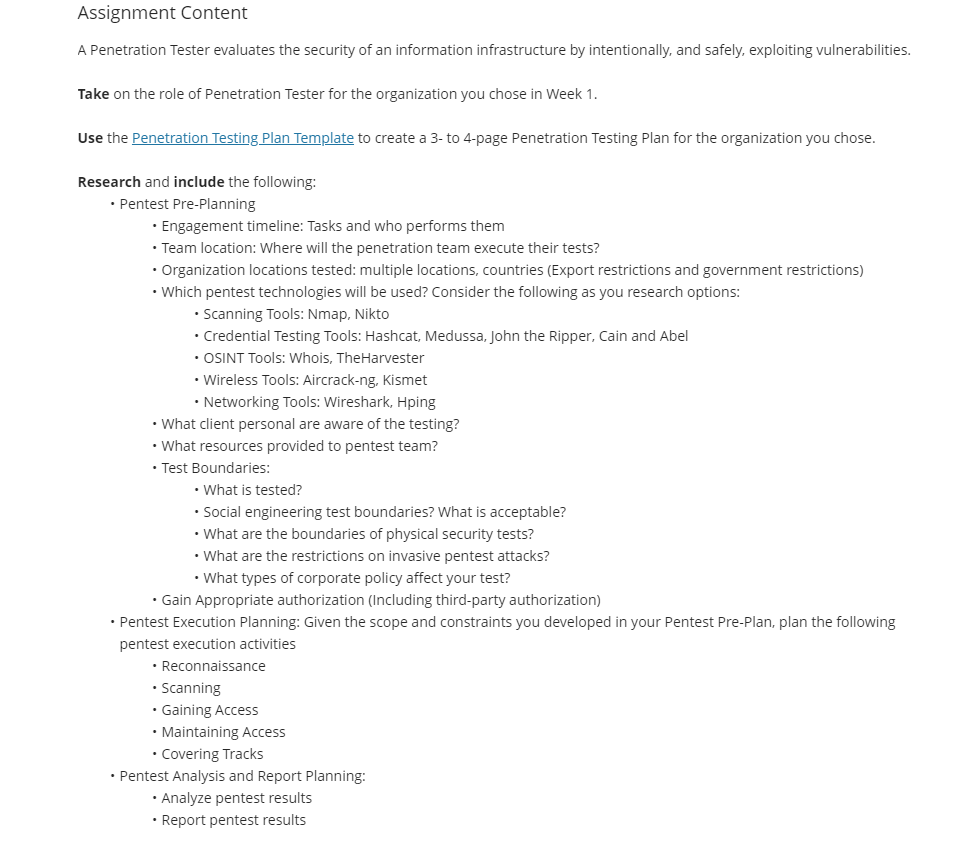 Here's the template
Here's the template
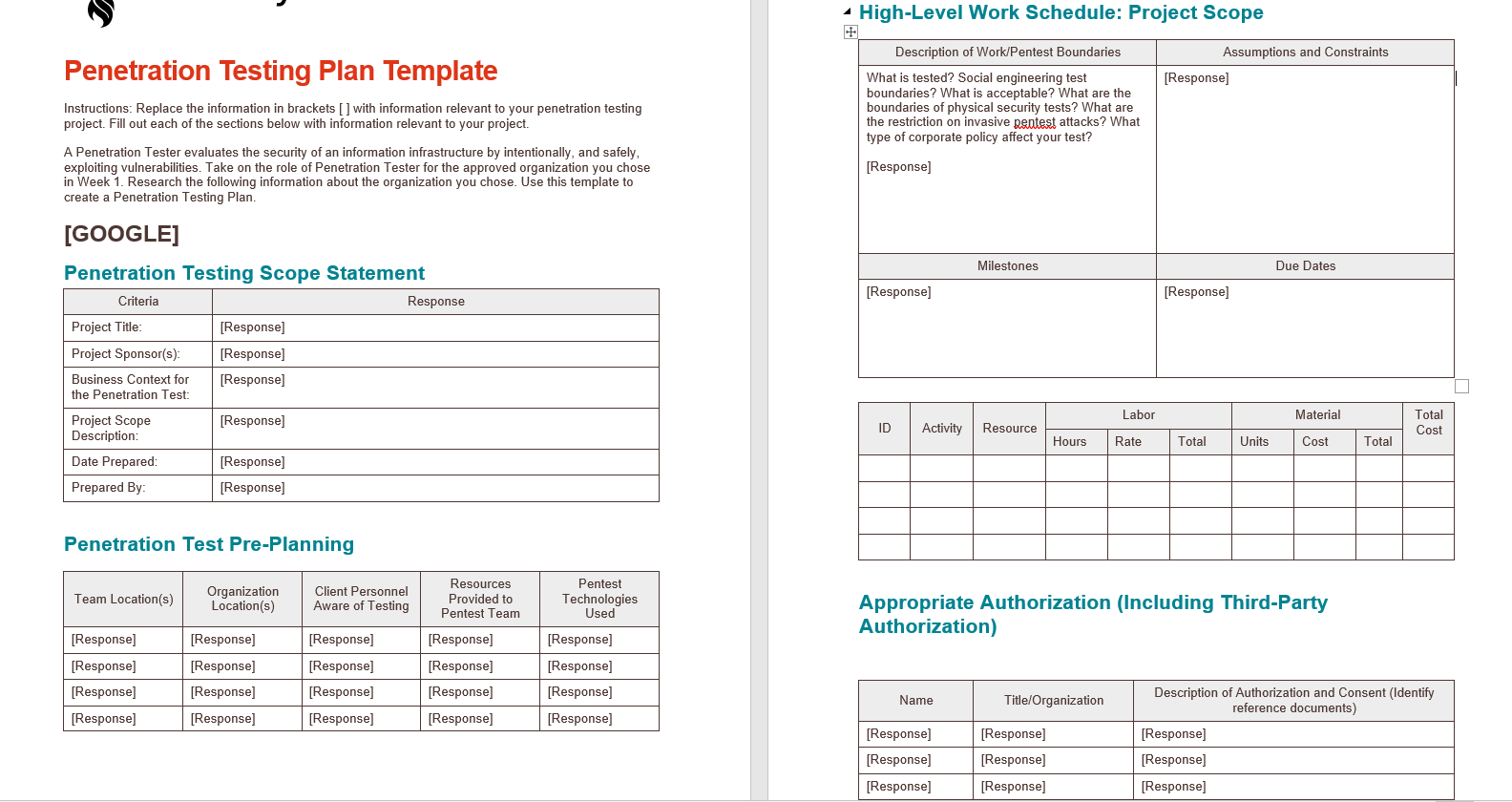
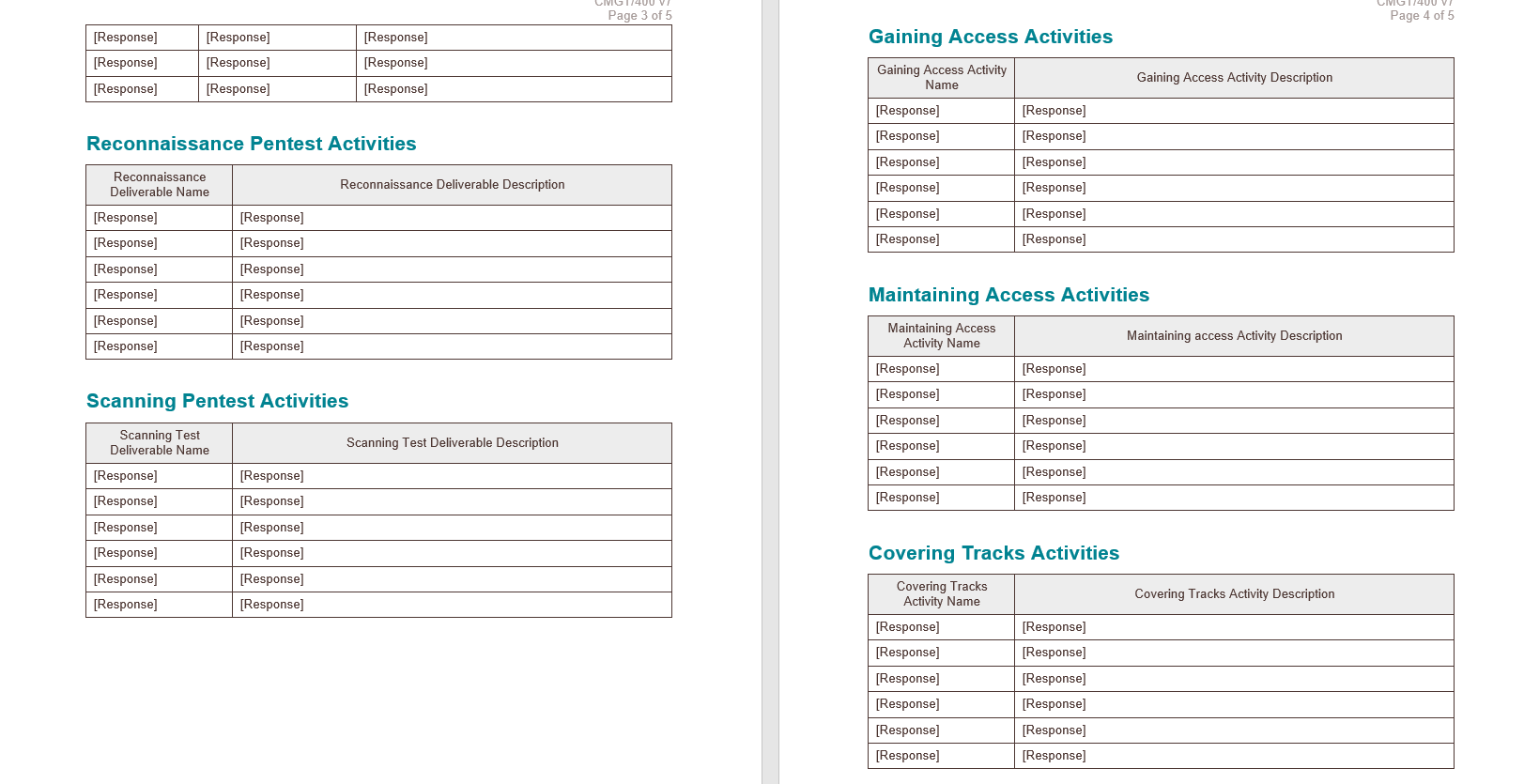
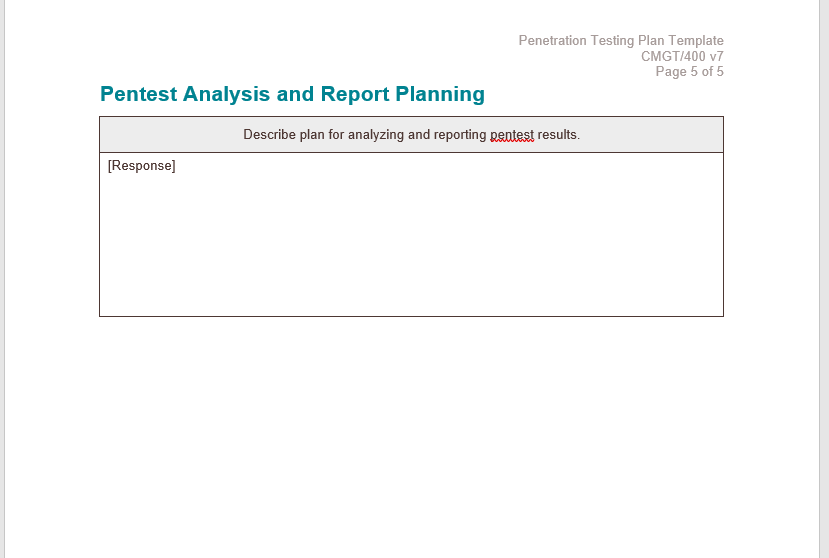
Assignment Content A Penetration Tester evaluates the security of an information infrastructure by intentionally, and safely, exploiting vulnerabilities. Take on the role of Penetration Tester for the organization you chose in Week 1. Use the Penetration Testing Plan Template to create a 3- to 4-page Penetration Testing Plan for the organization you chose. Research and include the following: Pentest Pre-Planning Engagement timeline: Tasks and who performs them Team location: Where will the penetration team execute their tests? Organization locations tested: multiple locations, countries (Export restrictions and government restrictions) Which pentest technologies will be used? Consider the following as you research options: Scanning Tools: Nmap, Nikto . Credential Testing Tools: Hashcat, Medussa, John the Ripper, Cain and Abel . OSINT Tools: Whois, The Harvester Wireless Tools: Aircrack-ng, Kismet Networking Tools: Wireshark, Hping What client personal are aware of the testing? What resources provided to pentest team? Test Boundaries: What is tested? Social engineering test boundaries? What is acceptable? What are the boundaries of physical security tests? . What are the restrictions on invasive pentest attacks? What types of corporate policy affect your test? . Gain Appropriate authorization (Including third-party authorization) Pentest Execution Planning: Given the scope and constraints you developed in your Pentest Pre-Plan, plan the following pentest execution activities Reconnaissance Scanning . Gaining Access Maintaining Access . Covering Tracks Pentest Analysis and Report Planning: Analyze pentest results Report pentest results - High-Level Work Schedule: Project Scope Description of Work/Pentest Boundaries Assumptions and Constraints Penetration Testing Plan Template [Response] Instructions: Replace the information in brackets [ ] with information relevant to your penetration testing project. Fill out each of the sections below with information relevant to your project. What is tested? Social engineering test boundaries? What is acceptable? What are the boundaries of physical security tests? What are the restriction on invasive Rentest attacks? What type of corporate policy affect your test? [Response] A Penetration Tester evaluates the security of an information infrastructure by intentionally, and safely, exploiting vulnerabilities. Take on the role of Penetration Tester for the approved organization you chose in Week 1. Research the following information about the organization you chose. Use this template to create a Penetration Testing Plan. Milestones Due Dates [Response) [Response) [GOOGLE] Penetration Testing Scope Statement Criteria Response Project Title: [Response] Project Sponsor(s): [Response) Business Context for [Response] the Penetration Test: Project Scope [Response] Description: Date Prepared: [Response] Prepared By: [Response] ID Activity Resource Labor Rate Material Cost Total Cost Hours Total Units Total Penetration Test Pre-Planning Team Location(s) Organization Location(s) Client Personnel Aware of Testing Resources Provided to Pentest Team Pentest Technologies Used Appropriate Authorization (Including Third-Party Authorization) [Response) [Response] [Response] [Response] [Response] [Response] [Response) [Response] [Response] [Response) [Response] [Response] [Response] [Response] [Response] [Response] [Response) [Response) [Response] [Response] Name Title/Organization Description of Authorization and Consent (Identify reference documents) [Response] [Response] [Response) [Response] [Response] [Response] [Response] [Response] [Response] LIVIG 1/400 V LIVG1/400 V Page 3 of 5 Page 4 of 5 Gaining Access Activities [Response) [Response] [Response] [Response) [Response) [Response] [Response] [Response) [Response] Gaining Access Activity Description Reconnaissance Pentest Activities Gaining Access Activity Name [Response] [Response] [Response) [Response] [Response) [Response] Reconnaissance Deliverable Name [Response] [Response] [Response] [Response] [Response) [Response) Reconnaissance Deliverable Description [Response) [Response] [Response) [Response] [Response] [Response] [Response] [Response] [Response) [Response] [Response] [Response] Maintaining Access Activities Maintaining access Activity Description Scanning Pentest Activities Maintaining Access Activity Name [Response] [Response] [Response] [Response] [Response) [Response] Scanning Test Deliverable Name [Response] [Response) [Response) [Response] [Response) [Response] Scanning Test Deliverable Description [Response] [Response] [Response] [Response) [Response] [Response] [Response] [Response) [Response) [Response] [Response] Covering Tracks Activities Covering Tracks Activity Description [Response] Covering Tracks Activity Name [Response] [Response] [Response] [Response) [Response] [Response] [Response] [Response] [Response) [Response] [Response) [Response) Penetration Testing Plan Template CMGT/400 v7 Page 5 of 5 Pentest Analysis and Report Planning Describe plan for analyzing and reporting Rentest results. [Response] Assignment Content A Penetration Tester evaluates the security of an information infrastructure by intentionally, and safely, exploiting vulnerabilities. Take on the role of Penetration Tester for the organization you chose in Week 1. Use the Penetration Testing Plan Template to create a 3- to 4-page Penetration Testing Plan for the organization you chose. Research and include the following: Pentest Pre-Planning Engagement timeline: Tasks and who performs them Team location: Where will the penetration team execute their tests? Organization locations tested: multiple locations, countries (Export restrictions and government restrictions) Which pentest technologies will be used? Consider the following as you research options: Scanning Tools: Nmap, Nikto . Credential Testing Tools: Hashcat, Medussa, John the Ripper, Cain and Abel . OSINT Tools: Whois, The Harvester Wireless Tools: Aircrack-ng, Kismet Networking Tools: Wireshark, Hping What client personal are aware of the testing? What resources provided to pentest team? Test Boundaries: What is tested? Social engineering test boundaries? What is acceptable? What are the boundaries of physical security tests? . What are the restrictions on invasive pentest attacks? What types of corporate policy affect your test? . Gain Appropriate authorization (Including third-party authorization) Pentest Execution Planning: Given the scope and constraints you developed in your Pentest Pre-Plan, plan the following pentest execution activities Reconnaissance Scanning . Gaining Access Maintaining Access . Covering Tracks Pentest Analysis and Report Planning: Analyze pentest results Report pentest results - High-Level Work Schedule: Project Scope Description of Work/Pentest Boundaries Assumptions and Constraints Penetration Testing Plan Template [Response] Instructions: Replace the information in brackets [ ] with information relevant to your penetration testing project. Fill out each of the sections below with information relevant to your project. What is tested? Social engineering test boundaries? What is acceptable? What are the boundaries of physical security tests? What are the restriction on invasive Rentest attacks? What type of corporate policy affect your test? [Response] A Penetration Tester evaluates the security of an information infrastructure by intentionally, and safely, exploiting vulnerabilities. Take on the role of Penetration Tester for the approved organization you chose in Week 1. Research the following information about the organization you chose. Use this template to create a Penetration Testing Plan. Milestones Due Dates [Response) [Response) [GOOGLE] Penetration Testing Scope Statement Criteria Response Project Title: [Response] Project Sponsor(s): [Response) Business Context for [Response] the Penetration Test: Project Scope [Response] Description: Date Prepared: [Response] Prepared By: [Response] ID Activity Resource Labor Rate Material Cost Total Cost Hours Total Units Total Penetration Test Pre-Planning Team Location(s) Organization Location(s) Client Personnel Aware of Testing Resources Provided to Pentest Team Pentest Technologies Used Appropriate Authorization (Including Third-Party Authorization) [Response) [Response] [Response] [Response] [Response] [Response] [Response) [Response] [Response] [Response) [Response] [Response] [Response] [Response] [Response] [Response] [Response) [Response) [Response] [Response] Name Title/Organization Description of Authorization and Consent (Identify reference documents) [Response] [Response] [Response) [Response] [Response] [Response] [Response] [Response] [Response] LIVIG 1/400 V LIVG1/400 V Page 3 of 5 Page 4 of 5 Gaining Access Activities [Response) [Response] [Response] [Response) [Response) [Response] [Response] [Response) [Response] Gaining Access Activity Description Reconnaissance Pentest Activities Gaining Access Activity Name [Response] [Response] [Response) [Response] [Response) [Response] Reconnaissance Deliverable Name [Response] [Response] [Response] [Response] [Response) [Response) Reconnaissance Deliverable Description [Response) [Response] [Response) [Response] [Response] [Response] [Response] [Response] [Response) [Response] [Response] [Response] Maintaining Access Activities Maintaining access Activity Description Scanning Pentest Activities Maintaining Access Activity Name [Response] [Response] [Response] [Response] [Response) [Response] Scanning Test Deliverable Name [Response] [Response) [Response) [Response] [Response) [Response] Scanning Test Deliverable Description [Response] [Response] [Response] [Response) [Response] [Response] [Response] [Response) [Response) [Response] [Response] Covering Tracks Activities Covering Tracks Activity Description [Response] Covering Tracks Activity Name [Response] [Response] [Response] [Response) [Response] [Response] [Response] [Response] [Response) [Response] [Response) [Response) Penetration Testing Plan Template CMGT/400 v7 Page 5 of 5 Pentest Analysis and Report Planning Describe plan for analyzing and reporting Rentest results. [Response]
 Here's the template
Here's the template








