Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Pleasehelp me out with this problem. This Program should be ablto to run in LC3! This homework will test your understanding of Routines that we
Pleasehelp me out with this problem. This Program should be ablto to run in LC3!

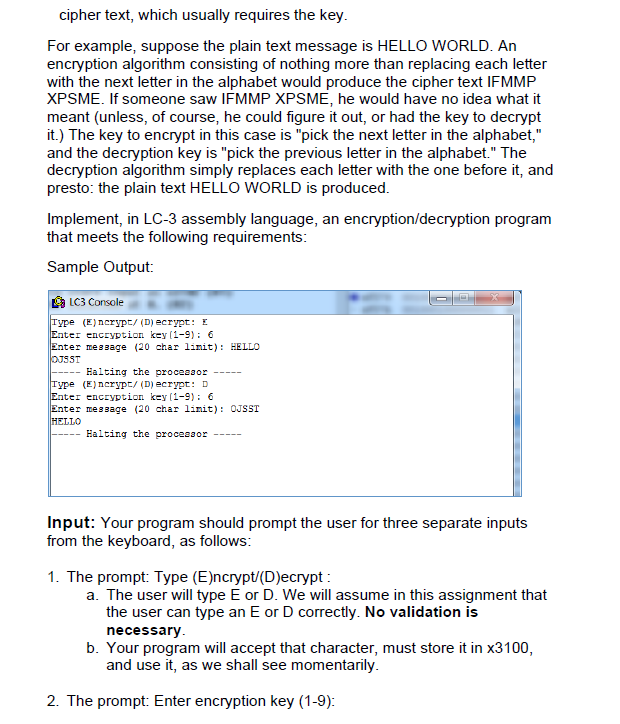


This homework will test your understanding of Routines that we covered in lecture from Chapter 8, 9 & 10 of your textbook. Submit your homework on Canvas before the due date and time. Answers to the problems must be submitted as a single zip file with the name, uwnetidhw6.zip or uwnetid1uwnetid2hw6.zip containing Crypt.asm and Mult.asm (if attempting extra credit, don't include other file extensions). No late work or email submissions will be accepted Instructions Write down the steps and draw a flowchart (if it helps) before you start with the Simulator and editor. You don't need to submit these but will help greatly in completing the work . Start your program at x3000 so that it will be easier for me to grade it. .Each program must include a header comment that has your name and a brief description of the program Make sure to comment logic of your assembly program. You will be graded on comments Background: Cryptography, from the Greek word kryptos, meaning "hidden", deals with the science of hiding a message from eyes you do not want to understand the contents of the message. The desire to do this has existed ever since humankind was first able to write. There are many ways to keep something secret. One way is to physically hide the document. Another way is to encrypt the text you wish to remain secret. Some people use this to keep others from understanding the contents of the files in their computer. Encrypting a file requires an input message, called the "plain text," and an encryption algorithm. An encryption algorithm transforms "plain text" into "cipher text." Just like a door needs a key to lock and unlock it, an encryption algorithm often requires a key to encrypt and decrypt a message. Just like a homeowner can selectively give the key to the front door to only those he wants to allow unaccompanied access, the author of a message can selectively give thee encryption key to only those he wants to be able to read the message. Iin order for someone to read the encrypted message, he has to decrypt the This homework will test your understanding of Routines that we covered in lecture from Chapter 8, 9 & 10 of your textbook. Submit your homework on Canvas before the due date and time. Answers to the problems must be submitted as a single zip file with the name, uwnetidhw6.zip or uwnetid1uwnetid2hw6.zip containing Crypt.asm and Mult.asm (if attempting extra credit, don't include other file extensions). No late work or email submissions will be accepted Instructions Write down the steps and draw a flowchart (if it helps) before you start with the Simulator and editor. You don't need to submit these but will help greatly in completing the work . Start your program at x3000 so that it will be easier for me to grade it. .Each program must include a header comment that has your name and a brief description of the program Make sure to comment logic of your assembly program. You will be graded on comments Background: Cryptography, from the Greek word kryptos, meaning "hidden", deals with the science of hiding a message from eyes you do not want to understand the contents of the message. The desire to do this has existed ever since humankind was first able to write. There are many ways to keep something secret. One way is to physically hide the document. Another way is to encrypt the text you wish to remain secret. Some people use this to keep others from understanding the contents of the files in their computer. Encrypting a file requires an input message, called the "plain text," and an encryption algorithm. An encryption algorithm transforms "plain text" into "cipher text." Just like a door needs a key to lock and unlock it, an encryption algorithm often requires a key to encrypt and decrypt a message. Just like a homeowner can selectively give the key to the front door to only those he wants to allow unaccompanied access, the author of a message can selectively give thee encryption key to only those he wants to be able to read the message. Iin order for someone to read the encrypted message, he has to decrypt the
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


