Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Problem 1. Let p be an odd prime. (6 points) (a) What are the possible values of x mod p so that x is
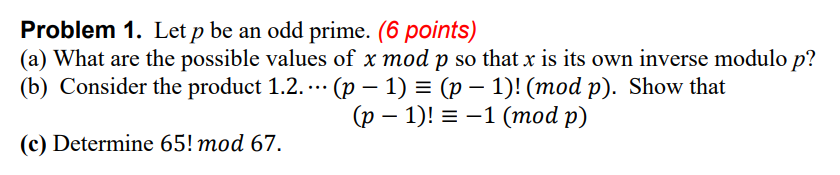
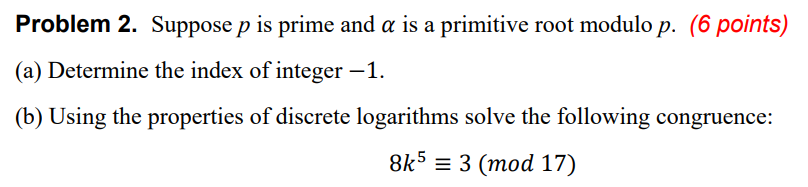

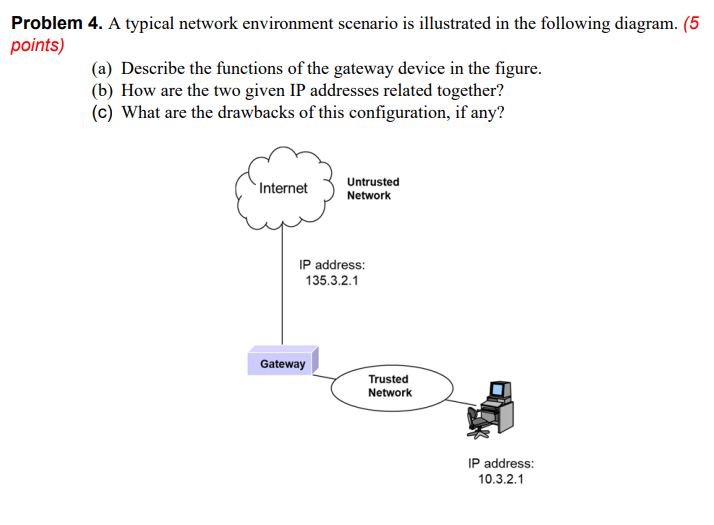
Problem 1. Let p be an odd prime. (6 points) (a) What are the possible values of x mod p so that x is its own inverse modulo p? (b) Consider the product 1.2.... (p 1) = (p 1)! (mod p). Show that (p 1)!= -1 (mod p) (c) Determine 65! mod 67. Problem 2. Suppose p is prime and a is a primitive root modulo p. (6 points) (a) Determine the index of integer -1. (b) Using the properties of discrete logarithms solve the following congruence: 8k5= 3 (mod 17) Problem 3. Indicate false (F) or true (T). (13 points) (a) IPSec encompasses three functional areas of authentication, confidentiality and privacy. (b) Transport mode provides protection to the entire IP packet. (c) IPSec is optional in IPv6. (d) Firewalls can hide the internal destination port numbers and IP addresses. (e) SHA-1 produces a hash value of 128 bits. (f) The PPTP, L2F, GRE, and L2TP are tunneling protocols. (g) An X.509v3 certificate is not an IETF standard. (h) IPSec is a transport-level security protocol. (i) When 3372 is divided by 37 the remainder is 9. (1) The integer value n - n is not necessarily divisible by 8 for every positive integer n. (k) An IPSec implementation may not need a database of Security Associations to be used. (1) The Digital Signature Standard (DSS) uses the digital signature algorithm (DSA). (m) The result of the addition operation (x + x + x) (x + x + 1) is 2x5 + 2x + x + 1. (n) -5 = 21 (mod 16). (o) A "zero polynomials" has no terms and has no solution. (p) IPSec uses IKE protocol to implement data confidentiality. (q) Deffie-Hellman scheme is mostly used for signing digital contracts. (r) A digital signature requires hashing and asymmetric encryption. (s) Using RSA, if an opponent can factor n into its two prime factors, enables him to figure out the private key. (t) Angie is the network administrator for a small e-commerce business. Her organization uses a dual firewall topology. She should install a Web server on the intranet segment that contains information that should be accessible to external users. (u) The multiplicative inverse of 59 mod 17 is 23. (v) A main application of digital signature is in signing the certificates issued by a CA. (w) 2n-1 + 32n-1 is divisible by 2 and 3 for every natural number n. (x) Alice and Bob can create a session key between themselves using their public-key schemes. (y) The AH protocol does whatever ESP does with additional functionality. (z) AES is a symmetrical encryption algorithm. Problem 4. A typical network environment scenario is illustrated in the following diagram. (5 points) (a) Describe the functions of the gateway device in the figure. (b) How are the two given IP addresses related together? (c) What are the drawbacks of this configuration, if any? Internet Untrusted Network IP address: 135.3.2.1 Gateway Trusted Network IP address: 10.3.2.1
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


