Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Problem 1 : On leaking, or hiding, the message length Consider encryption scheme Gen, Enc, Dec ) that is EAV - secure w . r
Problem : On leaking, or hiding, the message length
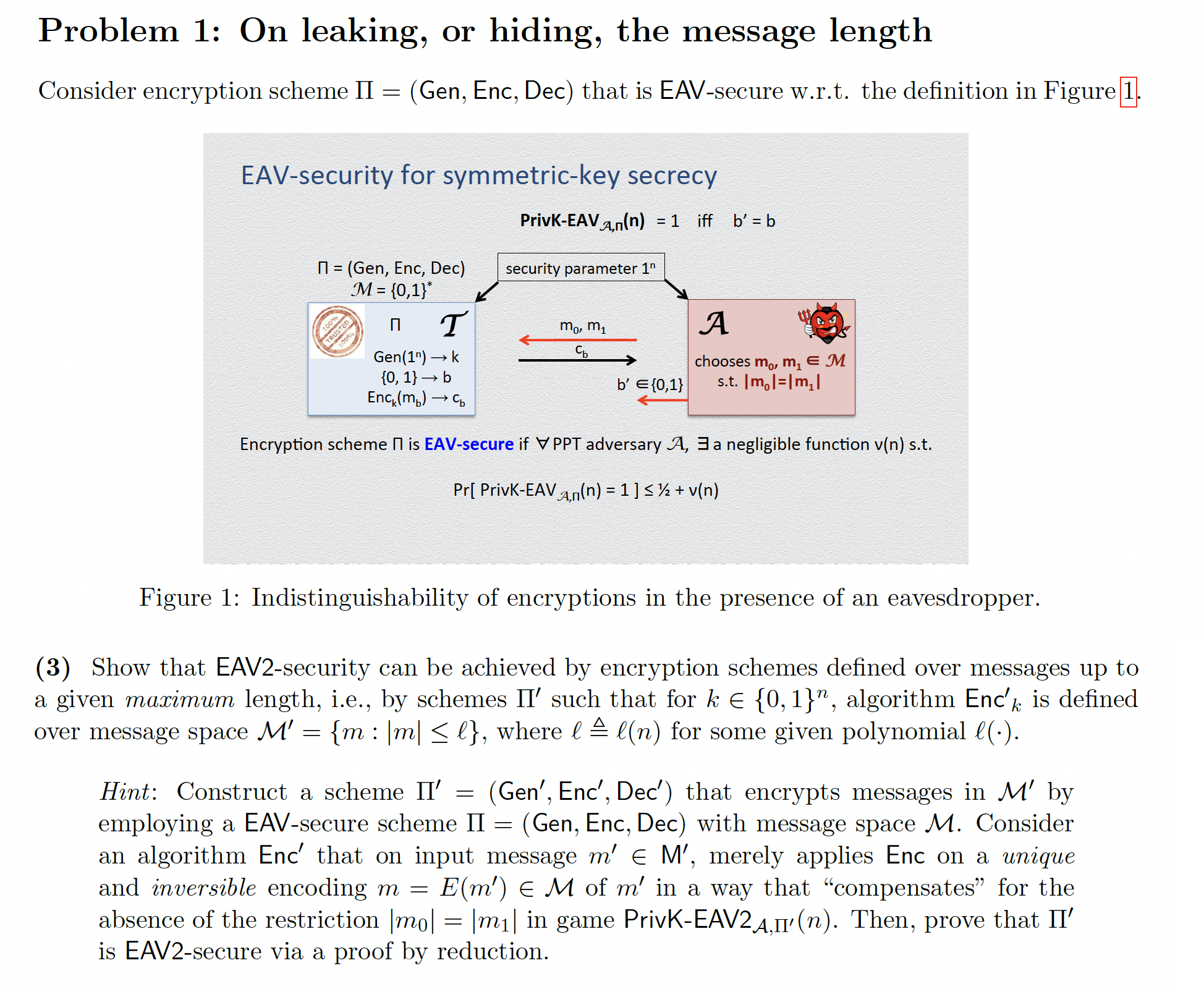
Consider encryption scheme Gen, Enc, Dec that is EAVsecure wrt the definition in Figure
Figure : Indistinguishability of encryptions in the presence of an eavesdropper.
Show that EAVsecurity can be achieved by encryption schemes defined over messages up to
a given maximum length, ie by schemes such that for kin algorithm Enc is defined
over message space : where for some given polynomial
Hint: Construct a scheme that encrypts messages in by
employing a EAVsecure scheme Gen, Enc, Dec with message space Consider
an algorithm Enc that on input message merely applies Enc on a unique
and inversible encoding of in a way that "compensates" for the
absence of the restriction in game Then, prove that
is EAVsecure via a proof by reduction.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


