Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Problem 3. Saadat has just intercepted the following ciphertext. He knows that it was encrypted using simple substitution and that the corresponding plaintext contains


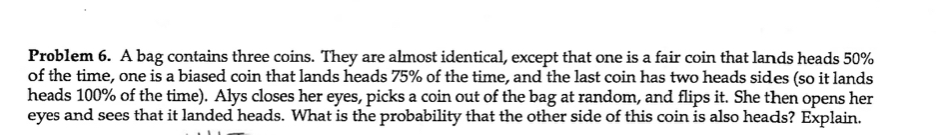
Problem 3. Saadat has just intercepted the following ciphertext. He knows that it was encrypted using simple substitution and that the corresponding plaintext contains the word METER. Help Saadat figure out how many pattern matches for METER occur in this ciphertext. 3. EHUHGHBHGDZAHAIMJGHGOOU Problem 4. Elsa has access to computational software with an in-built function chisq_cdf such that chisq_cdf(a, k), for a positive integer k and a non-negative real number a, returns the value of the integral f(x) dx, where fk is the chi-square distribution with k degrees of freedom. For example, in Sage, the function chisq_cdf would be defined as follows: def chisq_cdf(a, k): return RealDistribution ("chisquared", k).cum distribution function(a) Explain how Elsa would use this function to calculate 14(x) dx. You don't have to (and won't be able to) say what the value of this integral is; just write down how Elsa would compute this integral using chisq_cdf and explain briefly. A B D E 2 3 4 81 F GHI 3 KL M 56789 10 11 % O P 12 13 14 15 Q R S T U 16 17 18 19 V W X Y 2 20 21 22 23 24 25 Problem 1. Nam-joo has just intercepted a long piece of Vignre ciphertext. She knows it is the encryption of English plaintext, and based on an analysis of indices of coincidence, she thinks that the period is most likely 5. When she rewrites the ciphertext into a rectangle of width 5, she finds that the the most frequent letter in the first column is A. Given just this information, give an example of a word that might be the keyword that was used for encryption. Explain briefly. Problem 2. Logan has just intercepted a long piece of ciphertext. They know that it is an encryption of English plaintext, but they do not know which cipher was used to encrypt it. They find that the ciphertext has an index of coincidence of 1.1. How many out of the following 5 ciphers were probably not used to produce this ciphertext? Explain briefly. Affine cipher Hill cipher Playfair cipher Rectangular transposition Vignre cipher Problem 6. A bag contains three coins. They are almost identical, except that one is a fair coin that lands heads 50% of the time, one is a biased coin that lands heads 75% of the time, and the last coin has two heads sides (so it lands heads 100% of the time). Alys closes her eyes, picks a coin out of the bag at random, and flips it. She then opens her eyes and sees that it landed heads. What is the probability that the other side of this coin is also heads? Explain.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


