Answered step by step
Verified Expert Solution
Question
1 Approved Answer
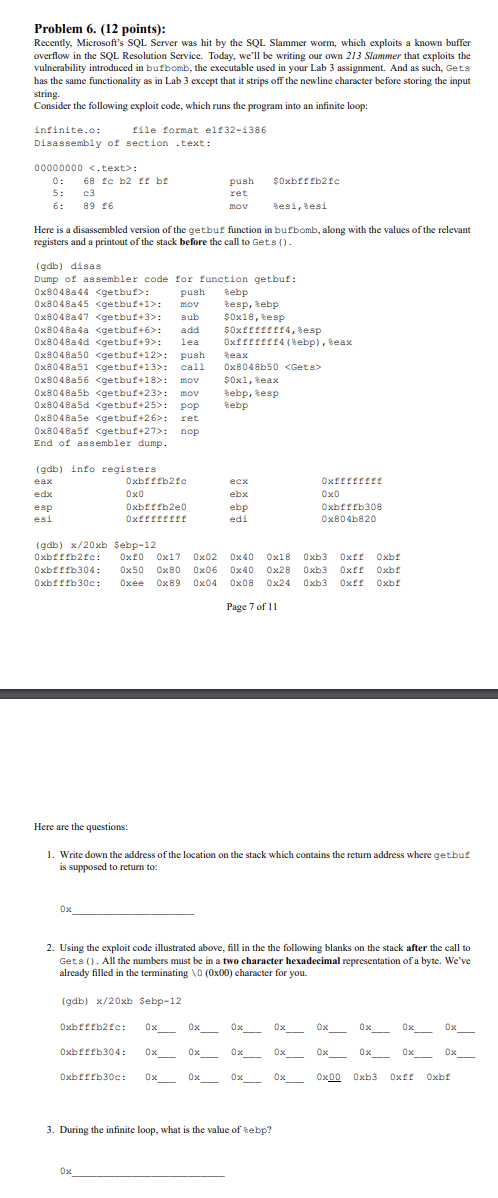
Problem 6 . ( 1 2 points ) : Recently, Microsoft's SQL Server was hit by the SQL Slammer worm, which exploits a known buffer
Problem points:
Recently, Microsoft's SQL Server was hit by the SQL Slammer worm, which exploits a known buffer
overflow in the SQL Resolution Service. Today, we'll be writing our own Slammer that exploits the
vulnerability introduced in bufbomb, the executable used in your Lab assignment. And as such, Gets
has the same functionality as in Lab except that it strips off the newline character before storing the input
string.
Consider the following exploit code, which runs the program into an infinite loop:
infinite.o: file format elf
Disassembly of section text:
text:
: fc b ff be push $xbfffbfc
: c ret
: mov sesi, besi
Here is a disassembled version of the getbuf function in bufbomb, along with the values of the relevant
registers and a printout of the stack before the call to Gets
gclb disas
Dump of assembler code for function getbuf:
:: esp ebp, esi Oxfffffff
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


