Answered step by step
Verified Expert Solution
Question
1 Approved Answer
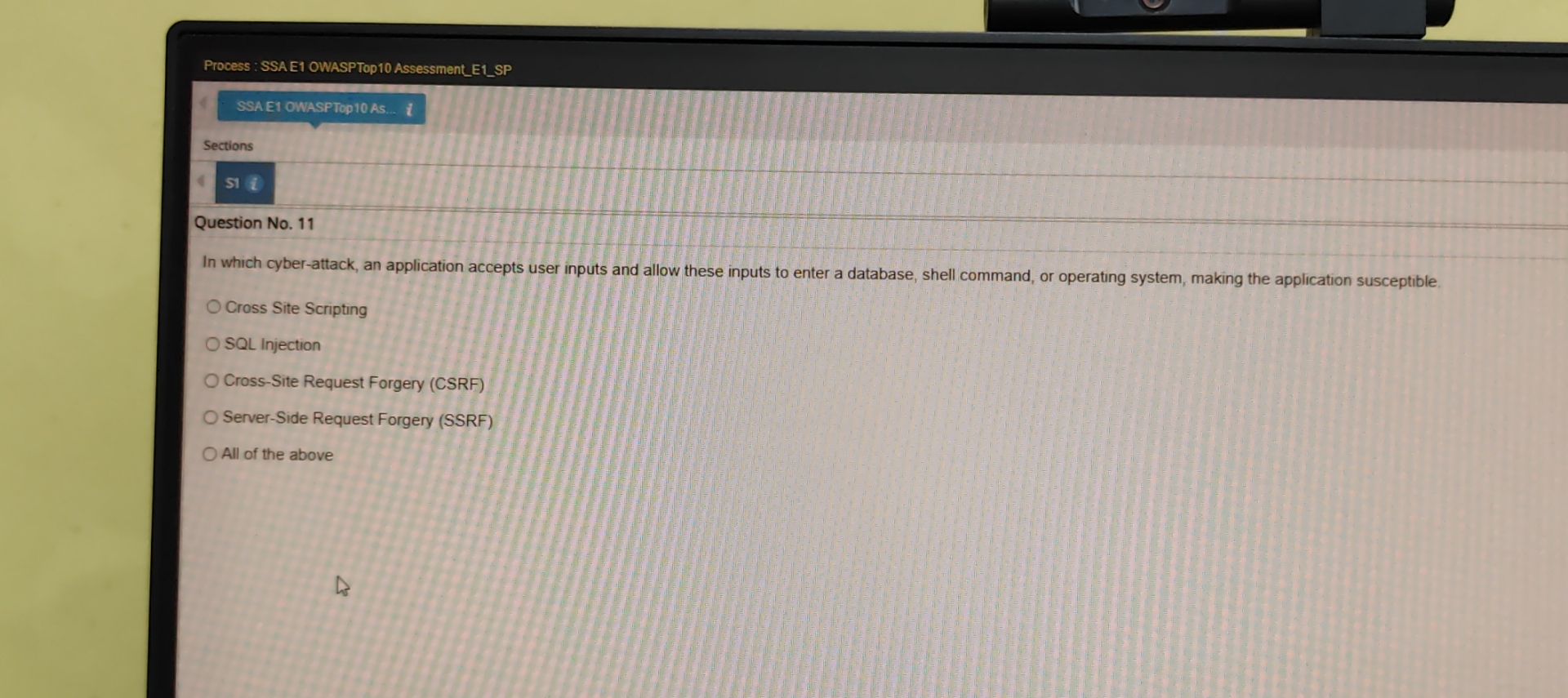
Process : SSAE 1 OWASPTop 1 0 Assessment _ E 1 _ SP Sections si i Question No . 1 1 In which cyber -
Process : SSAE OWASPTop AssessmentESP
Sections
si
Question No
In which cyberattack, an application accepts user inputs and allow these inputs to enter a database, shell command, or operating system, making the application susceptible.
Cross Site Scripting
SQL Injection
CrossSite Request Forgery CSRF
ServerSide Request Forgery SSRF
All of the above
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


