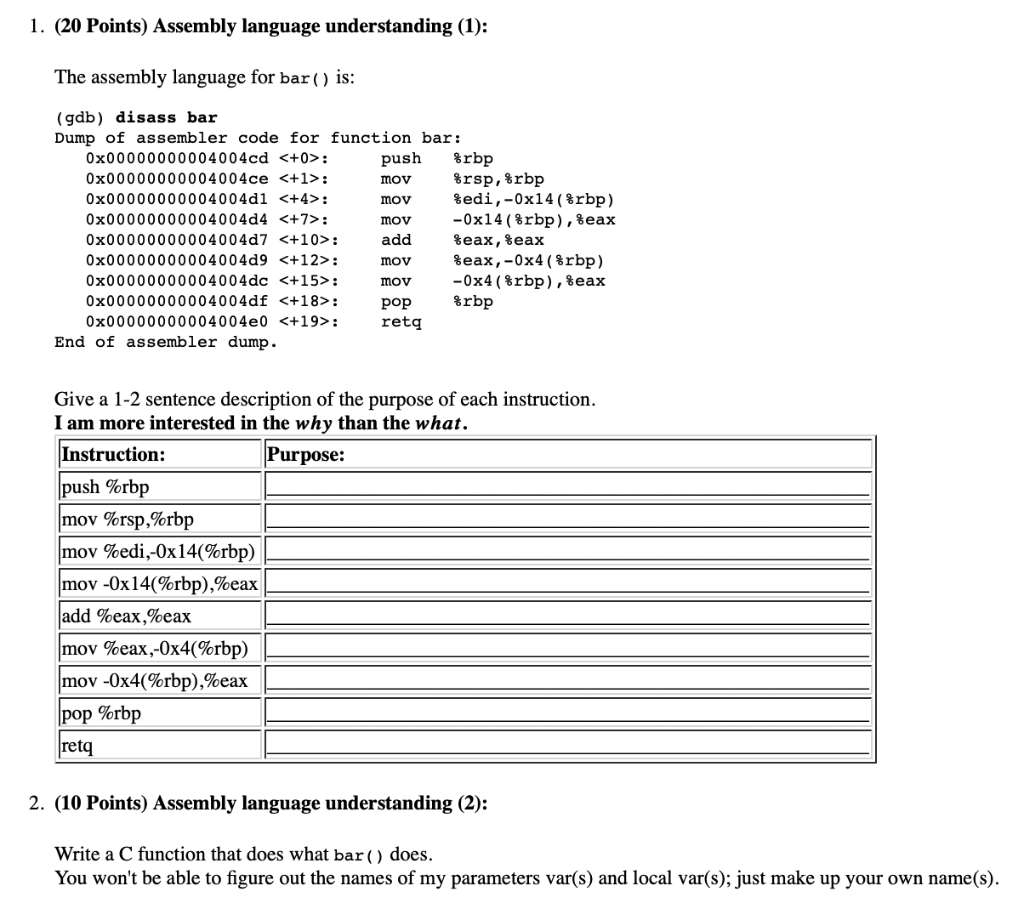
Question: Programming in C (20 Points) Assembly language understanding (1): The assembly language for bar() is: (gdb) disass bar Dump of assembler code for function bar:
Programming in C
- (20 Points) Assembly language understanding (1):
The assembly language for bar() is:
(gdb) disass bar
Dump of assembler code for function bar:
0x00000000004004cd : push %rbp
0x00000000004004ce : mov %rsp,%rbp
0x00000000004004d1 : mov %edi,-0x14(%rbp)
0x00000000004004d4 : mov -0x14(%rbp),%eax
0x00000000004004d7 : add %eax,%eax
0x00000000004004d9 : mov %eax,-0x4(%rbp)
0x00000000004004dc : mov -0x4(%rbp),%eax
0x00000000004004df : pop %rbp
0x00000000004004e0 : retq
End of assembler dump.
Give a 1-2 sentence description of the purpose of each instruction. I am more interested in the why than the what.
| Instruction: | Purpose: |
| push %rbp | ___________________________________________________________ |
| mov %rsp,%rbp | ___________________________________________________________ |
| mov %edi,-0x14(%rbp) | ___________________________________________________________ |
| mov -0x14(%rbp),%eax | ___________________________________________________________ |
| add %eax,%eax | ___________________________________________________________ |
| mov %eax,-0x4(%rbp) | ___________________________________________________________ |
| mov -0x4(%rbp),%eax | ___________________________________________________________ |
| pop %rbp | ___________________________________________________________ |
| retq | ___________________________________________________________ |
- (10 Points) Assembly language understanding (2):
Write a C function that does what bar() does. You won't be able to figure out the names of my parameters var(s) and local var(s); just make up your own name(s).
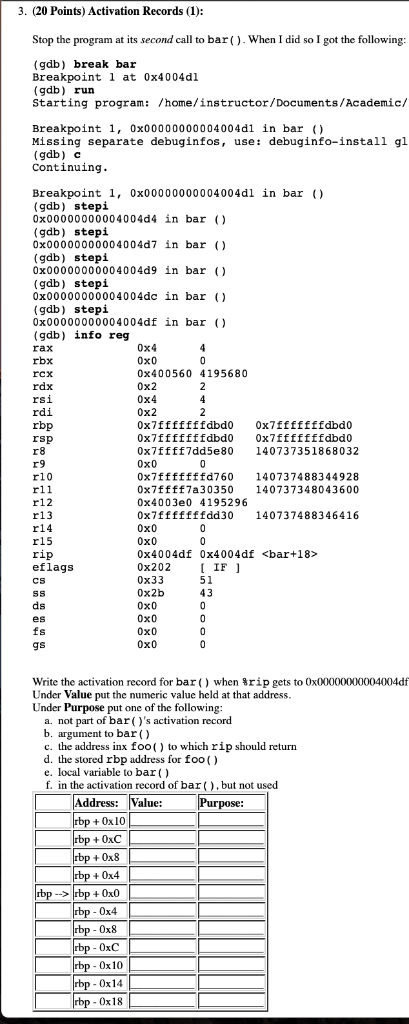
- (20 Points) Activation Records (1):
Stop the program at its second call to bar(). When I did so I got the following:
(gdb) break bar
Breakpoint 1 at 0x4004d1
(gdb) run
Breakpoint 1, 0x00000000004004d1 in bar ()
Missing separate debuginfos, use: debuginfo-install glibc-2.17-222.el7.x86_64
(gdb) c
Continuing.
Breakpoint 1, 0x00000000004004d1 in bar ()
(gdb) stepi
0x00000000004004d4 in bar ()
(gdb) stepi
0x00000000004004d7 in bar ()
(gdb) stepi
0x00000000004004d9 in bar ()
(gdb) stepi
0x00000000004004dc in bar ()
(gdb) stepi
0x00000000004004df in bar ()
(gdb) info reg
rax 0x4 4
rbx 0x0 0
rcx 0x400560 4195680
rdx 0x2 2
rsi 0x4 4
rdi 0x2 2
rbp 0x7fffffffdbd0 0x7fffffffdbd0
rsp 0x7fffffffdbd0 0x7fffffffdbd0
r8 0x7ffff7dd5e80 140737351868032
r9 0x0 0
r10 0x7fffffffd760 140737488344928
r11 0x7ffff7a30350 140737348043600
r12 0x4003e0 4195296
r13 0x7fffffffdd30 140737488346416
r14 0x0 0
r15 0x0 0
rip 0x4004df 0x4004df
eflags 0x202 [ IF ]
cs 0x33 51
ss 0x2b 43
ds 0x0 0
es 0x0 0
fs 0x0 0
gs 0x0 0
Write the activation record for bar() when %rip gets to 0x00000000004004df. Under Value put the numeric value held at that address. Under Purpose put one of the following:
- not part of bar()'s activation record
- argument to bar()
- the address inx foo() to which rip should return
- the stored rbp address for foo()
- local variable to bar()
- in the activation record of bar(), but not used
| Address: | Value: | Purpose: | |
| rbp + 0x10 | ___________ | ___________ | |
| rbp + 0xC | ___________ | ___________ | |
| rbp + 0x8 | ___________ | ___________ | |
| rbp + 0x4 | ___________ | ___________ | |
| rbp --> | rbp + 0x0 | ___________ | ___________ |
| rbp - 0x4 | ___________ | ___________ | |
| rbp - 0x8 | ___________ | ___________ | |
| rbp - 0xC | ___________ | ___________ | |
| rbp - 0x10 | ___________ | ___________ | |
| rbp - 0x14 | ___________ | ___________ | |
| rbp - 0x18 | ___________ | ___________ |
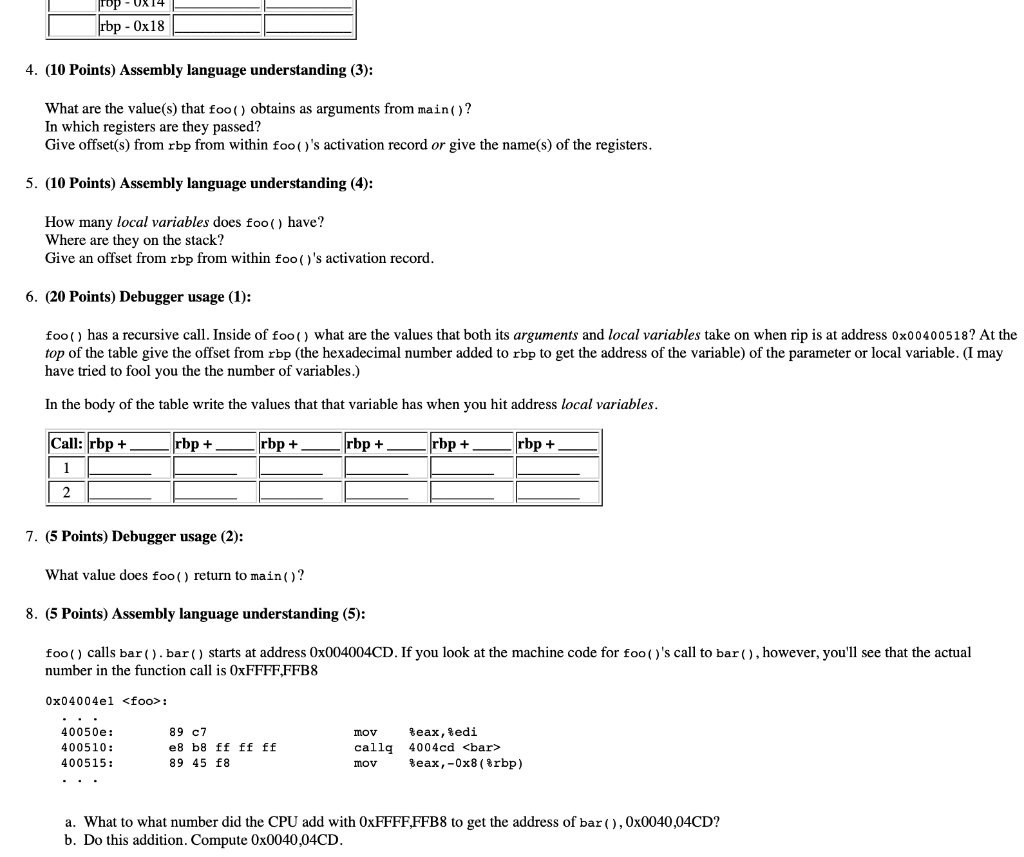
- (10 Points) Assembly language understanding (3):
What are the value(s) that foo() obtains as arguments from main()? In which registers are they passed? Give offset(s) from rbp from within foo()'s activation record or give the name(s) of the registers.
- (10 Points) Assembly language understanding (4):
How many local variables does foo() have? Where are they on the stack? Give an offset from rbp from within foo()'s activation record.
- (20 Points) Debugger usage (1):
foo() has a recursive call. Inside of foo() what are the values that both its arguments and local variables take on when rip is at address 0x00400518? At the top of the table give the offset from rbp (the hexadecimal number added to rbp to get the address of the variable) of the parameter or local variable. (I may have tried to fool you the the number of variables.)
In the body of the table write the values that that variable has when you hit address local variables.
| Call: | rbp + _____ | rbp + _____ | rbp + _____ | rbp + _____ | rbp + _____ | rbp + _____ |
| 1 | ________ | ________ | ________ | ________ | ________ | ________ |
| 2 | ________ | ________ | ________ | ________ | ________ | ________ |
- (5 Points) Debugger usage (2):
What value does foo() return to main()?
- (5 Points) Assembly language understanding (5):
foo() calls bar(). bar() starts at address 0x004004CD. If you look at the machine code for foo()'s call to bar(), however, you'll see that the actual number in the function call is 0xFFFF,FFB8
0x04004e1 :
. . .
40050e:89 c7 mov %eax,%edi
400510:e8 b8 ff ff ff callq 4004cd
400515:89 45 f8 mov %eax,-0x8(%rbp)
. . .
- What to what number did the CPU add with 0xFFFF,FFB8 to get the address of bar(), 0x0040,04CD?
- Do this addition. Compute 0x0040,04CD.
1. (20 Points) Assembly language understanding (1): The assembly language for bar () is (gdb) disass bar Dump of assembler code for function bar: 0x00000000004004cd : 0x00000000004004ce : 0x00000000004004d1 : 0x00000000004004d4 : 0x00000000004004d7 0x00000000004004d9: 0x00000000004004dc 0x00000000004004df : 0x00000000004004e0 : push mov mov mov add mov mov pop retq %rbp %rsp, %rbp %edi ,-0x14(%rbp) -0x14 ( %rbp) , %eax %eax, %eax %eax,-0x4(%rbp) -0x4 ( %rbp) , %eax % rbp End of assembler dump. Give a 1-2 sentence description of the purpose of each instruction I am more interested in the why than the what. Instruction: push %rbp mov %rsp,%rbp mov %edi,-0x14(%rbp) mov-0x14(%rbp),%eax add %eax,%eax mov %eax,0x4(%rbp) mov-0x4(%rbp),%eax pop %rbp re Purpose: 2. (10 Points) Assembly language understanding (2): Write a C function that does what bar() does. You won't be able to figure out the names of my parameters var(s) and local var(s); just make up your own name(s) 3. (20 Points) Activation Records (1): Stop the program at its second call to bar). When I did so I got the following (gdb) break bar Breakpoint 1 at 0x4004d1 (gdb) rurn Starting program: /home/instructor/Documents/Academic/ Breakpoint 1, 0x00000000004004d1 in bar ) Missing separate debuginfos, use: debuginfo-install gl (gdb) c Continuing Breakpoint 1, 0x00000000004004dl in bar ) (gdb) stepi 0x00000000004004d4 in bar () (gdb) stepi 0x00000000004004d7 in bar () (gdb) stepi 0x00000000004004d9 in bar () (gdb) stepi 0x00000000004004dc in bar ) (gdb) stepi 0x00000000004004df in bar ) (gdb) info reg rax rbx rcx rdx rsi rdi rbp rsp r8 r9 r10 0x4 0x0 0x400560 4195680 0x2 0x4 0x2 0x7fffffffdbd0 0x7fffffffdbd0 0x7fffffffdbd0 0x7fffffffdbd0 0x7ffff7dd5e80 140737351868032 0x0 0x7fffffffd760 140737488344928 0x7ffff7a30350 140737348043600 0x4003e0 4195296 0x7fffffffdd30 140737488346416 0x0 0x0 0x4004df 0x4004df
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


