Provide the terminal command used. Answer questions from 5-8 and provide screenshot of the code in nmap or kali and your answer and justify it by giving reason.
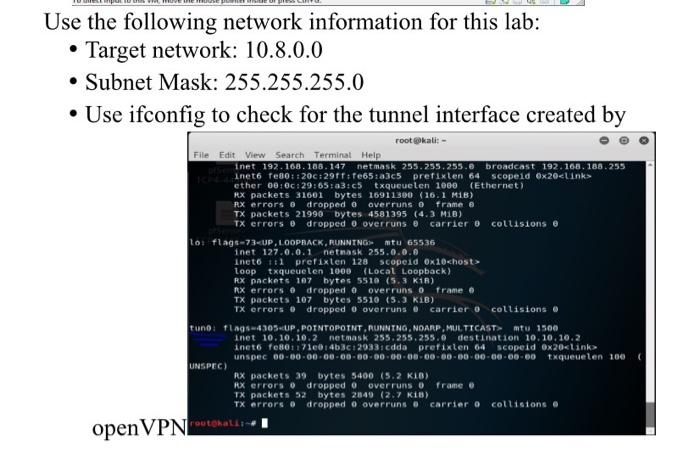
The Target server address is 10.8.0.0
and subnet mask is 255.255.255.0
network address is 10.8.0.0
subnet mask 255.255.255.0
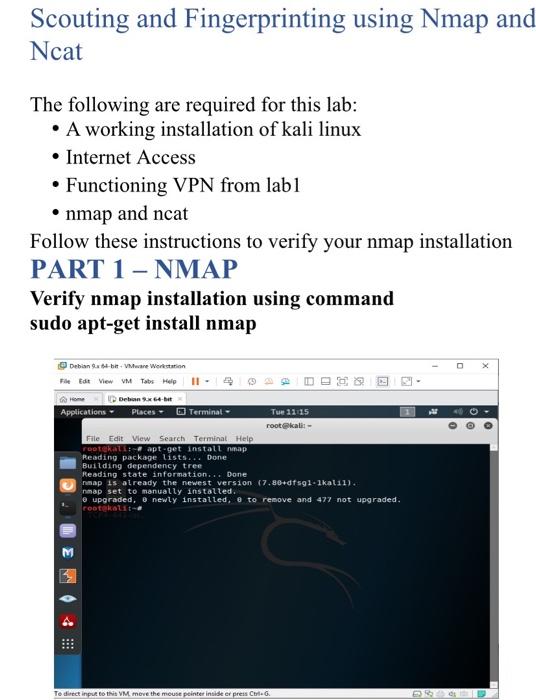
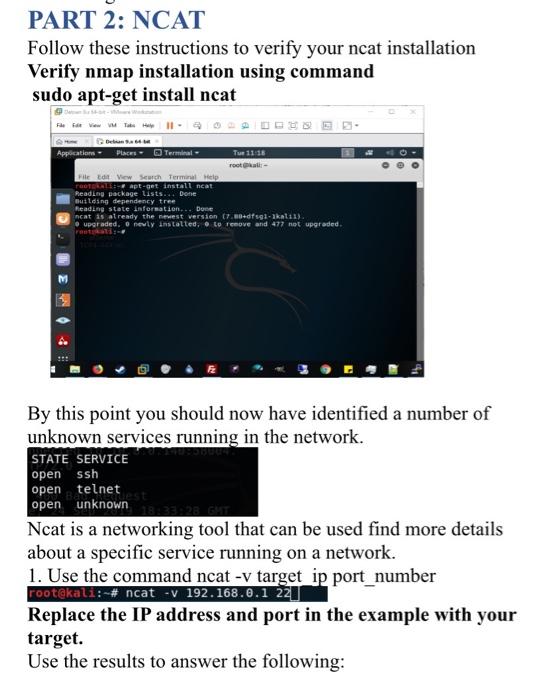
PART 2: NCAT Follow these instructions to verify your ncat installation Verify nmap installation using command sudo apt-get install ncat Application Places Terminal Tue 11:16 File Edit View Such Termural Help GOTERALES apt-get install ncat Reading package lists. Done Building dependency tree Reading state information... Done ncat is already the newest version 07.10+dfsg-akalin). upgraded.newly instalted, to remove and 477 not upgraded ret . A. By this point you should now have identified a number of unknown services running in the network. STATE SERVICE open ssh open telnet open unknown Ncat is a networking tool that can be used find more details about a specific service running on a network. 1. Use the command ncat -v target ip port_number rootekali: # ncat -v 192.168.0.1 22 Replace the IP address and port in the example with your target. Use the results to answer the following: 5. Describe another way to get the HTML from the webserver. 6. What command would you use to banner grab SMTP? 7. How would you banner grab the following protocols: TFTP DNS POP SNMP NTP iSCSI 8. What is the IP address of the host that displays your group number? Scouting and Fingerprinting using Nmap and Ncat The following are required for this lab: A working installation of kali linux Internet Access Functioning VPN from labl nmap and ncat Follow these instructions to verify your nmap installation PART 1 - NMAP Verify nmap installation using command sudo apt-get install nmap O Debian 6-hr- VMware Workstation File Edit View VM Tabs Help 11 Debian. Applications - Places Terminal Tue 11:15 rootkali:- File Edit View Search Terminal Help rootkali-apt-get install nmap Reading package lists... Done Building dependency tree Reading state information... Done map is already the newest version (7.88+dfsgl-lkal11). map set to manually installed. e upgraded, newly installed, e to remove and 477 not upgraded. root kalite 4 ::: Te direct input to this VM move the mouse pointer insider press Cirile Use the following network information for this lab: Target network: 10.8.0.0 Subnet Mask: 255.255.255.0 Use ifconfig to check for the tunnel interface created by root@kali:- File Edit View Search Terminal Help inet 192.168.188.147 netmask 255.255.255.2 broadcast 192.168.188.255 inet6 fe80::200:29 7:7e65:a3c5 prefixten 64 scopeid 6x20cLinks ether 68: 0029:65:a3:05 txqueuelen 1968 (Ethernet) RX packets 31601 bytes 16911390 (16.1 MB) Rx errors @dropped @ overruns o frame @ TX packets 21990 bytes 4581395 (4.3 MB) Tx errors o dropped 0 overruns o carrier o collisions to flagc-73-UP, LOOPBACK, RUNNING mtu 65536 1 PHI 12 0, 0,1 netmask 255.0.0.0 Ineto 1:1 prefixlen 128 scopeid Ox10
loop txqueuelen 1000 (Local Loopback) RX packets 107 bytes 5510 (5.3 K1R) RX errors o dropped overruns o frame TX packets 107 bytes 5510 (5.3 KIB) TX errors o dropped overruns carrier o collisions Tuno flags4305 unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 UNSPEC) RX packets 39 bytes 5400 (5.2 KIB) RX errors o dropped overruns o frame TX packets 52 bytes 2849 (2.7 KB) TX errors o dropped overruns e carrier o collisions ALL openVPN PART 2: NCAT Follow these instructions to verify your ncat installation Verify nmap installation using command sudo apt-get install ncat Application Places Terminal Tue 11:16 File Edit View Such Termural Help GOTERALES apt-get install ncat Reading package lists. Done Building dependency tree Reading state information... Done ncat is already the newest version 07.10+dfsg-akalin). upgraded.newly instalted, to remove and 477 not upgraded ret . A. By this point you should now have identified a number of unknown services running in the network. STATE SERVICE open ssh open telnet open unknown Ncat is a networking tool that can be used find more details about a specific service running on a network. 1. Use the command ncat -v target ip port_number rootekali: # ncat -v 192.168.0.1 22 Replace the IP address and port in the example with your target. Use the results to answer the following: 5. Describe another way to get the HTML from the webserver. 6. What command would you use to banner grab SMTP? 7. How would you banner grab the following protocols: TFTP DNS POP SNMP NTP iSCSI 8. What is the IP address of the host that displays your group number? Scouting and Fingerprinting using Nmap and Ncat The following are required for this lab: A working installation of kali linux Internet Access Functioning VPN from labl nmap and ncat Follow these instructions to verify your nmap installation PART 1 - NMAP Verify nmap installation using command sudo apt-get install nmap O Debian 6-hr- VMware Workstation File Edit View VM Tabs Help 11 Debian. Applications - Places Terminal Tue 11:15 rootkali:- File Edit View Search Terminal Help rootkali-apt-get install nmap Reading package lists... Done Building dependency tree Reading state information... Done map is already the newest version (7.88+dfsgl-lkal11). map set to manually installed. e upgraded, newly installed, e to remove and 477 not upgraded. root kalite 4 ::: Te direct input to this VM move the mouse pointer insider press Cirile Use the following network information for this lab: Target network: 10.8.0.0 Subnet Mask: 255.255.255.0 Use ifconfig to check for the tunnel interface created by root@kali:- File Edit View Search Terminal Help inet 192.168.188.147 netmask 255.255.255.2 broadcast 192.168.188.255 inet6 fe80::200:29 7:7e65:a3c5 prefixten 64 scopeid 6x20cLinks ether 68: 0029:65:a3:05 txqueuelen 1968 (Ethernet) RX packets 31601 bytes 16911390 (16.1 MB) Rx errors @dropped @ overruns o frame @ TX packets 21990 bytes 4581395 (4.3 MB) Tx errors o dropped 0 overruns o carrier o collisions to flagc-73-UP, LOOPBACK, RUNNING mtu 65536 1 PHI 12 0, 0,1 netmask 255.0.0.0 Ineto 1:1 prefixlen 128 scopeid Ox10 loop txqueuelen 1000 (Local Loopback) RX packets 107 bytes 5510 (5.3 K1R) RX errors o dropped overruns o frame TX packets 107 bytes 5510 (5.3 KIB) TX errors o dropped overruns carrier o collisions Tuno flags4305 unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 UNSPEC) RX packets 39 bytes 5400 (5.2 KIB) RX errors o dropped overruns o frame TX packets 52 bytes 2849 (2.7 KB) TX errors o dropped overruns e carrier o collisions ALL openVPN