Question
Q1 a) Give an example of malicious code execution , and illustrate the four different ways of defending against malicious code execution on that example.
Q1
a) Give an example of malicious code execution , and illustrate the four different ways of defending against malicious code execution on that example. b) Explain and illustrate the vulnerability life-cycle on a cyber- attack of your choice .
Q2 This question is about Attribute-based Access Control policies.
a) Given the attributes A and B, which can be True, False or Unknown, define a policy P such that all the following conditions are met: i) If B is True, then P evaluates to Permit, ii) if B is False and A is True, then P evaluates to Deny, iii) otherwise, P evaluates neither to Permit nor Deny.
b) Given the attributes A, B and C, which can be True, False or Unknown, define a policy P such that all the following conditions are met: i) if any attribute is True, then P evaluates to Permit, ii) otherwise, P evaluates to Deny.
Q3 A company is offering a new online payment system using a biometric authentication solution. A customer must first register using a mobile app, scanning their face and storing their payment details on a remote server. After registration, every time a customer wants to purchase a product online, the must open an application on their phone which will take a picture of their face, and matching it against the template stored at registration. The server storing the templates is a UNIX server, and the connection between the phone application and the server is secured using TLS. a) Identify and assess the risk of an Information Disclosure threat, and recommend an avoidance risk control against that threat.
b) Identify and assess the risk of a Tampering threat, and recommend a mitigation risk control against that threat.
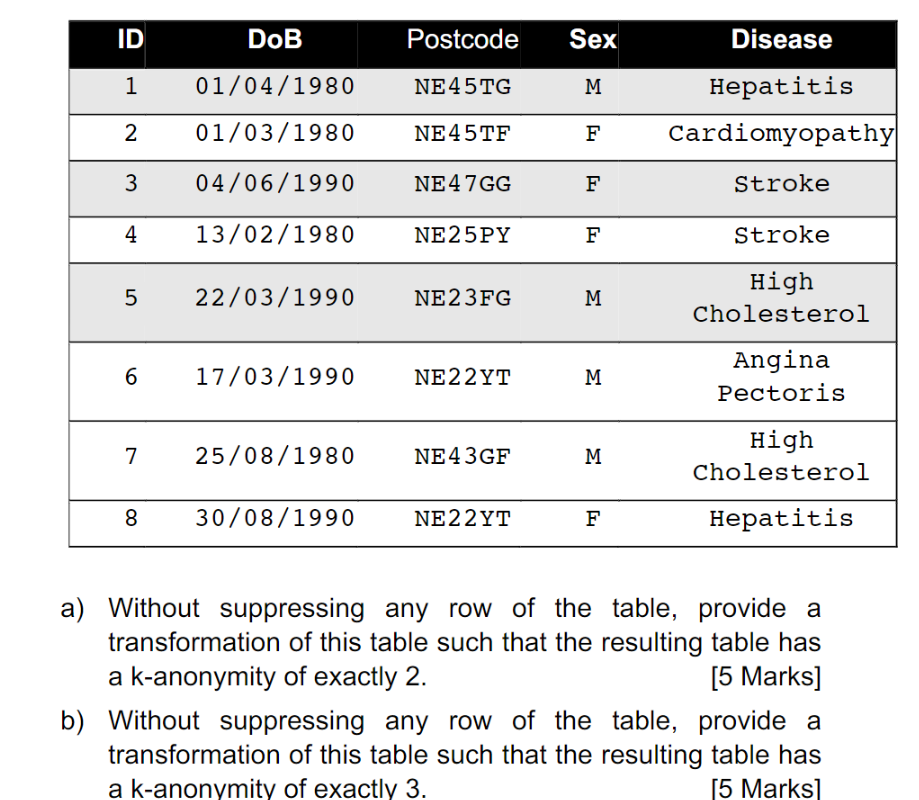
Q4
in the table

Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


