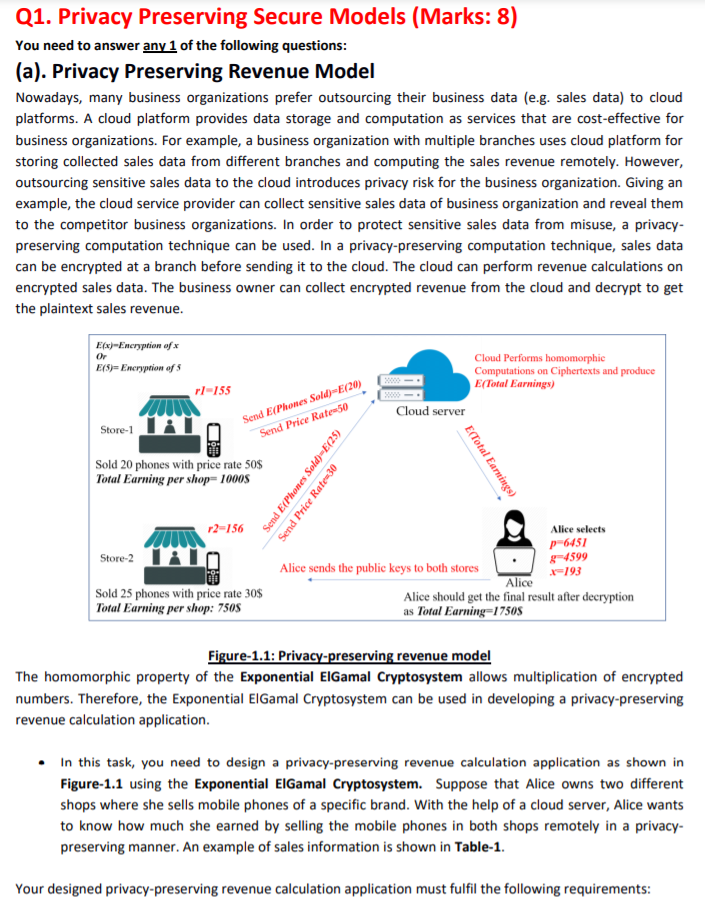
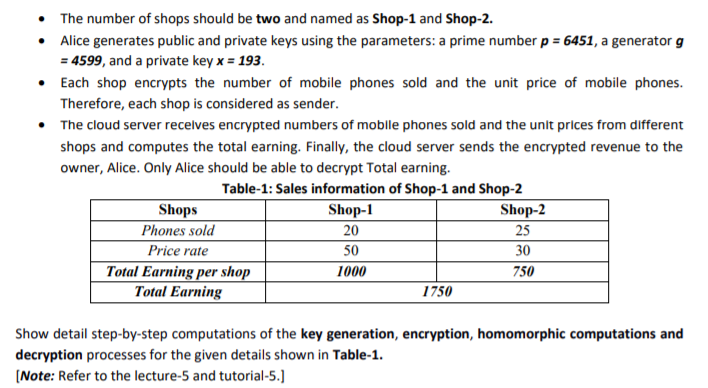
Q1. Privacy Preserving Secure Models (Marks: 8) You need to answer any 1 of the following questions: (a). Privacy Preserving Revenue Model Nowadays, many business organizations prefer outsourcing their business data (e.g. sales data) to cloud platforms. A cloud platform provides data storage and computation as services that are cost-effective for business organizations. For example, a business organization with multiple branches uses cloud platform for storing collected sales data from different branches and computing the sales revenue remotely. However, outsourcing sensitive sales data to the cloud introduces privacy risk for the business organization. Giving an example, the cloud service provider can collect sensitive sales data of business organization and reveal them to the competitor business organizations. In order to protect sensitive sales data from misuse, a privacy- preserving computation technique can be used. In a privacy-preserving computation technique, sales data can be encrypted at a branch before sending it to the cloud. The cloud can perform revenue calculations on encrypted sales data. The business owner can collect encrypted revenue from the cloud and decrypt to get the plaintext sales revenue. Ex-Eneryption of x Or E(5)= Encryption of Cloud Performs homomorphic Computations on Ciphertexts and produce E(Total Earnings) r1-155 Cloud server Store-1 Send E(Phones Sold)=E(20) Send Price Rate-50 Sold 20 phones with price rate 50$ Total Earning per shop-1000$ Send E(Phones Sold)=E(25) Send Price Rate-30 E(Total Earnings 2-156 Store-2 Alice selects p-6451 Alice sends the public keys to both stores Alice Alice should get the final result after decryption as Total Earning=17505 84599 --193 Sold 25 phones with price rate 30$ Total Earning per shop: 7508 Figure-1.1: Privacy-preserving revenue model The homomorphic property of the Exponential ElGamal Cryptosystem allows multiplication of encrypted numbers. Therefore, the exponential ElGamal Cryptosystem can be used in developing a privacy-preserving revenue calculation application. In this task, you need to design a privacy-preserving revenue calculation application as shown in Figure-1.1 using the Exponential ElGamal Cryptosystem. Suppose that Alice owns two different shops where she sells mobile phones of a specific brand. With the help of a cloud server, Alice wants to know how much she earned by selling the mobile phones in both shops remotely in a privacy- preserving manner. An example of sales information is shown in Table-1. Your designed privacy-preserving revenue calculation application must fulfil the following requirements: The number of shops should be two and named as Shop-1 and Shop-2. Alice generates public and private keys using the parameters: a prime number p = 6451, a generator g = 4599, and a private key x = 193. Each shop encrypts the number of mobile phones sold and the unit price of mobile phones. Therefore, each shop is considered as sender. The cloud server receives encrypted numbers of mobile phones sold and the unit prices from different shops and computes the total earning. Finally, the cloud server sends the encrypted revenue to the owner, Alice. Only Alice should be able to decrypt Total earning. Table-1: Sales information of Shop-1 and Shop-2 Shops Shop-1 Shop-2 Phones sold 20 25 Price rate 50 30 Total Earning per shop 1000 750 Total Earning 1750 Show detail step-by-step computations of the key generation, encryption, homomorphic computations and decryption processes for the given details shown in Table-1. [Note: Refer to the lecture-5 and tutorial-5.] Q1. Privacy Preserving Secure Models (Marks: 8) You need to answer any 1 of the following questions: (a). Privacy Preserving Revenue Model Nowadays, many business organizations prefer outsourcing their business data (e.g. sales data) to cloud platforms. A cloud platform provides data storage and computation as services that are cost-effective for business organizations. For example, a business organization with multiple branches uses cloud platform for storing collected sales data from different branches and computing the sales revenue remotely. However, outsourcing sensitive sales data to the cloud introduces privacy risk for the business organization. Giving an example, the cloud service provider can collect sensitive sales data of business organization and reveal them to the competitor business organizations. In order to protect sensitive sales data from misuse, a privacy- preserving computation technique can be used. In a privacy-preserving computation technique, sales data can be encrypted at a branch before sending it to the cloud. The cloud can perform revenue calculations on encrypted sales data. The business owner can collect encrypted revenue from the cloud and decrypt to get the plaintext sales revenue. Ex-Eneryption of x Or E(5)= Encryption of Cloud Performs homomorphic Computations on Ciphertexts and produce E(Total Earnings) r1-155 Cloud server Store-1 Send E(Phones Sold)=E(20) Send Price Rate-50 Sold 20 phones with price rate 50$ Total Earning per shop-1000$ Send E(Phones Sold)=E(25) Send Price Rate-30 E(Total Earnings 2-156 Store-2 Alice selects p-6451 Alice sends the public keys to both stores Alice Alice should get the final result after decryption as Total Earning=17505 84599 --193 Sold 25 phones with price rate 30$ Total Earning per shop: 7508 Figure-1.1: Privacy-preserving revenue model The homomorphic property of the Exponential ElGamal Cryptosystem allows multiplication of encrypted numbers. Therefore, the exponential ElGamal Cryptosystem can be used in developing a privacy-preserving revenue calculation application. In this task, you need to design a privacy-preserving revenue calculation application as shown in Figure-1.1 using the Exponential ElGamal Cryptosystem. Suppose that Alice owns two different shops where she sells mobile phones of a specific brand. With the help of a cloud server, Alice wants to know how much she earned by selling the mobile phones in both shops remotely in a privacy- preserving manner. An example of sales information is shown in Table-1. Your designed privacy-preserving revenue calculation application must fulfil the following requirements: The number of shops should be two and named as Shop-1 and Shop-2. Alice generates public and private keys using the parameters: a prime number p = 6451, a generator g = 4599, and a private key x = 193. Each shop encrypts the number of mobile phones sold and the unit price of mobile phones. Therefore, each shop is considered as sender. The cloud server receives encrypted numbers of mobile phones sold and the unit prices from different shops and computes the total earning. Finally, the cloud server sends the encrypted revenue to the owner, Alice. Only Alice should be able to decrypt Total earning. Table-1: Sales information of Shop-1 and Shop-2 Shops Shop-1 Shop-2 Phones sold 20 25 Price rate 50 30 Total Earning per shop 1000 750 Total Earning 1750 Show detail step-by-step computations of the key generation, encryption, homomorphic computations and decryption processes for the given details shown in Table-1. [Note: Refer to the lecture-5 and tutorial-5.]








