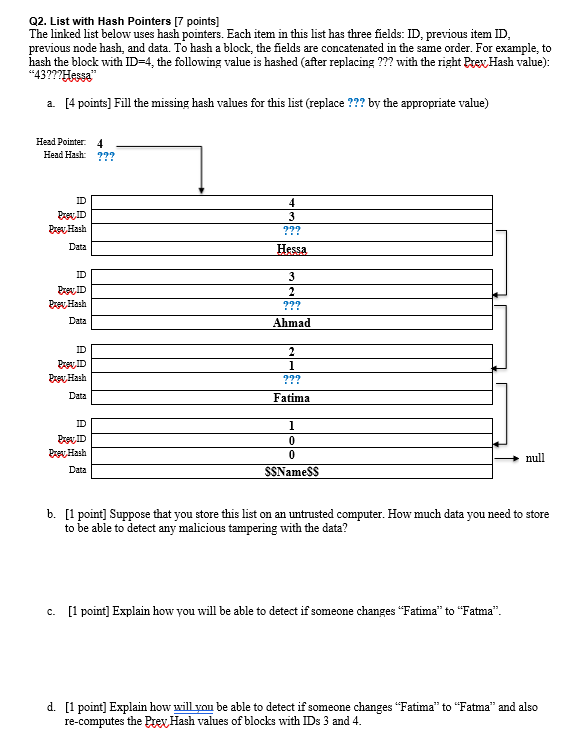
Q2. List with Hash Pointers [7 points) The linked list below uses hash pointers. Each item in this list has three fields: ID, previous item ID, previous node hash, and data. To hash a block, the fields are concatenated in the same order. For example, to hash the block with ID=4, the following value is hashed (after replacing ??? with the right Prev Hash value): *43???Hessa" a. [4 points) Fill the missing hash values for this list (replace ??? by the appropriate value) Head Pointer Head Hash 4 ??? PRID Prev Hash Data 3 ??? Hessa 3 ID Rre ID Prou Hash Data ??? Ahmad PRID Prev Hash ??? Data Fatima ID Prev Hash Data SSNamess b. [1 point] Suppose that you store this list on an untrusted computer. How much data you need to store to be able to detect any malicious tampering with the data? c. [1 point] Explain how you will be able to detect if someone changes "Fatima" to "Fatma". d. [1 point] Explain how will you be able to detect if someone changes "Fatima" to "Fatma" and also re-computes the Prev Hash values of blocks with IDs 3 and 4. Q2. List with Hash Pointers [7 points) The linked list below uses hash pointers. Each item in this list has three fields: ID, previous item ID, previous node hash, and data. To hash a block, the fields are concatenated in the same order. For example, to hash the block with ID=4, the following value is hashed (after replacing ??? with the right Prev Hash value): *43???Hessa" a. [4 points) Fill the missing hash values for this list (replace ??? by the appropriate value) Head Pointer Head Hash 4 ??? PRID Prev Hash Data 3 ??? Hessa 3 ID Rre ID Prou Hash Data ??? Ahmad PRID Prev Hash ??? Data Fatima ID Prev Hash Data SSNamess b. [1 point] Suppose that you store this list on an untrusted computer. How much data you need to store to be able to detect any malicious tampering with the data? c. [1 point] Explain how you will be able to detect if someone changes "Fatima" to "Fatma". d. [1 point] Explain how will you be able to detect if someone changes "Fatima" to "Fatma" and also re-computes the Prev Hash values of blocks with IDs 3 and 4







