Q5. Application of Public-Key Cryptography (Marks: 4+4 = 8) Figure-5: Partial list of first 10000 Prime Numbers Say, Alice wants to design a smart door
Q5. Application of Public-Key Cryptography (Marks: 4+4 = 8) 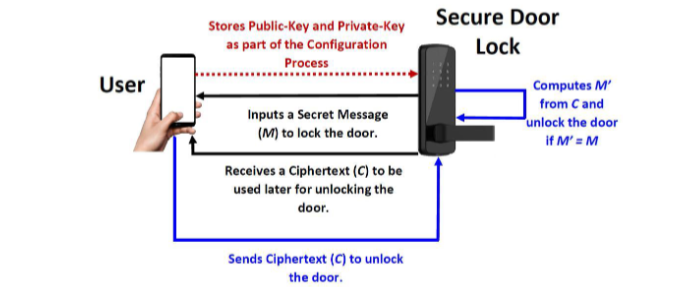 Figure-5: Partial list of first 10000 Prime Numbers Say, Alice wants to design a smart door lock for you using Public-Key Cryptography Algorithm. The smart door lock requires initialization of a pair of keys (public-key and private-key) with a Public-Key Cryptography Algorithm. Parameters of both public and private keys need to be saved in the smart door lock at the time of configuration. The algorithm is designed in a way that would allow you to save the key parameters at the time of configuration which can be changed later by you. At the time of locking the door, you need to enter a secret message (M) which will be saved in the smart door lock unless the door is opened. The smart door lock would generate a ciphertext (C) and send it to your mobile phone as an SMS. The smart door lock requires you to enter C at the time of opening the door. The smart door lock would decrypt C and generate a plaintext M. If the generated M matches with the stored M, then the door will be unlocked. An overview of the process in shown in Figure-5. Assume that public and private keys will be generated using either RSA or ElGamal Public-Key Cryptography Algorithm. Also assume that you would use your student number as the secret message M. For example, if your student number is S123456, the secret message is: M = 123456. Answer the following questions: a) Consider that the smart door lock is using RSA Public-Key Cryptography Algorithm. With proper description, show detailed steps of key generation, generation of ciphertext C (i.e., encryption process), and generation of the plaintext M (i.e., decryption process). Use parameters: p = 8377 and q = 6673. i. Choose a small public key parameter (e = 937) and show detailed steps to compute your public-key and private-key? ii. How would the smart door lock encrypt message M =
Figure-5: Partial list of first 10000 Prime Numbers Say, Alice wants to design a smart door lock for you using Public-Key Cryptography Algorithm. The smart door lock requires initialization of a pair of keys (public-key and private-key) with a Public-Key Cryptography Algorithm. Parameters of both public and private keys need to be saved in the smart door lock at the time of configuration. The algorithm is designed in a way that would allow you to save the key parameters at the time of configuration which can be changed later by you. At the time of locking the door, you need to enter a secret message (M) which will be saved in the smart door lock unless the door is opened. The smart door lock would generate a ciphertext (C) and send it to your mobile phone as an SMS. The smart door lock requires you to enter C at the time of opening the door. The smart door lock would decrypt C and generate a plaintext M. If the generated M matches with the stored M, then the door will be unlocked. An overview of the process in shown in Figure-5. Assume that public and private keys will be generated using either RSA or ElGamal Public-Key Cryptography Algorithm. Also assume that you would use your student number as the secret message M. For example, if your student number is S123456, the secret message is: M = 123456. Answer the following questions: a) Consider that the smart door lock is using RSA Public-Key Cryptography Algorithm. With proper description, show detailed steps of key generation, generation of ciphertext C (i.e., encryption process), and generation of the plaintext M (i.e., decryption process). Use parameters: p = 8377 and q = 6673. i. Choose a small public key parameter (e = 937) and show detailed steps to compute your public-key and private-key? ii. How would the smart door lock encrypt message M =
Must show step by step working out
Stores Public-Key and Private-Key as part of the Configuration Process Secure Door Lock User Inputs a Secret Message (M) to lock the door. Computes M' from Cand unlock the door if M'EM Receives a Ciphertext (C) to be used later for unlocking the door. Sends Ciphertext (C) to unlock the doorStep by Step Solution
There are 3 Steps involved in it
Step: 1

See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


