Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Question 0 1 ) : Recall the functional details of DES. Will the security of DES algorithm be compromised if the Pbox is removed from
Question : Recall the functional details of DES. Will the security of DES algorithm be compromised if the Pbox is removed from the DES algorithm? Why or why not?
Question : How does the Cipher Block Chaining overcome the drawback of Electronic Code Book ECB Also, explain how recovers from errors in transmission.
Question a: Write an algorithm for encryption using RSA.
b Differentiate between signature based IDS and Anomaly based IDs. Which one is better than the other in term of false alarm rate?
Question a: Differentiate Encrypt first then Sign vs Sign first and then Encrypt. Is the order really matter???
bSIK
PlainText
Encrypt the plaintext into CipherText by using the SIK and Knapsack Algorithm.
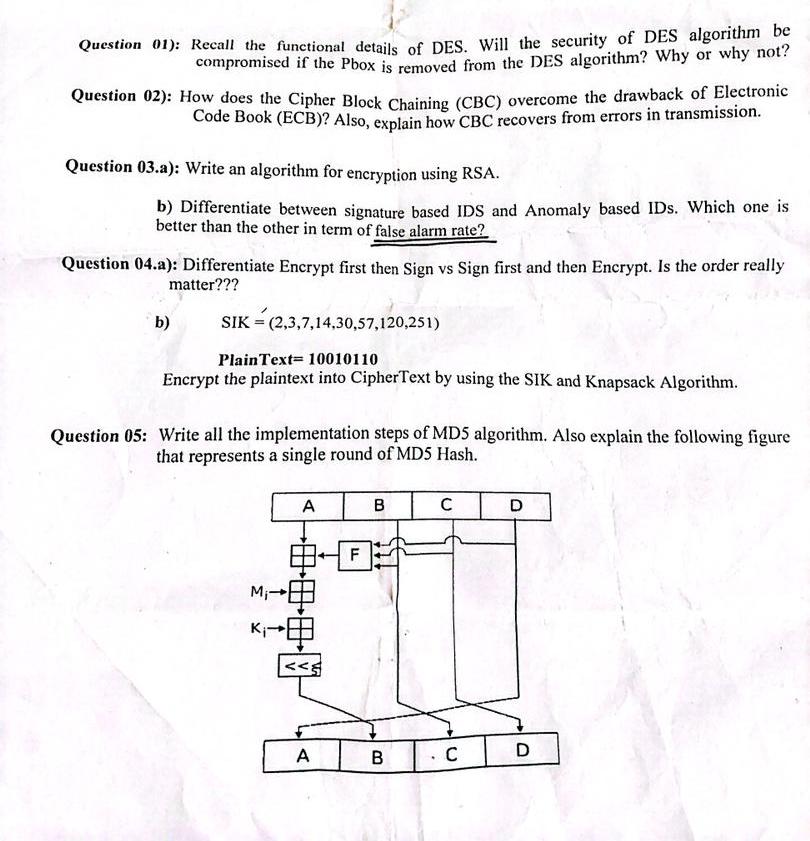
Question : Write all the implementation steps of MD algorithm. Also explain the following figure that represents a single round of MD Hash.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


