Answered step by step
Verified Expert Solution
Question
1 Approved Answer
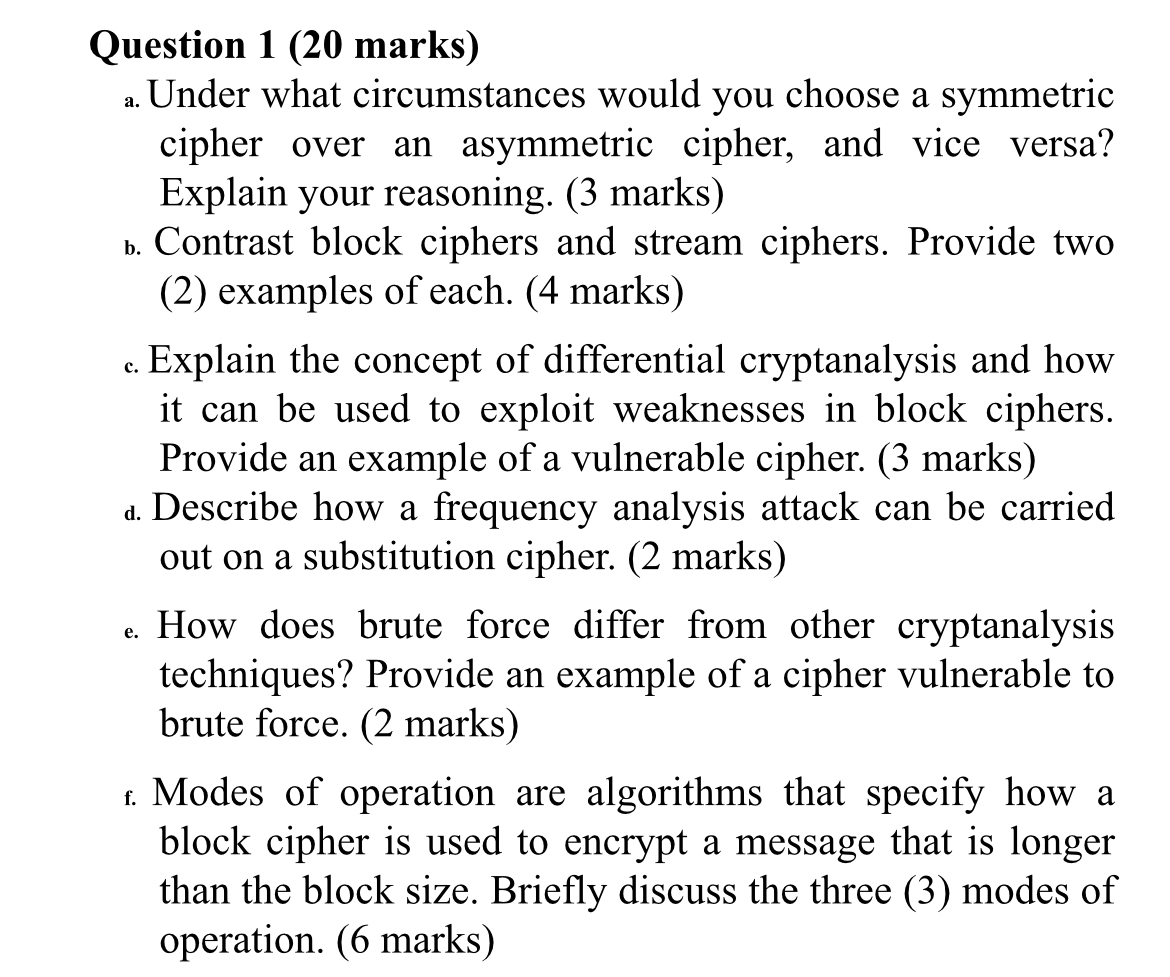
Question 1 ( 2 0 marks ) a . Under what circumstances would you choose a symmetric cipher over an asymmetric cipher, and vice versa?
Question marks
a Under what circumstances would you choose a symmetric cipher over an asymmetric cipher, and vice versa? Explain your reasoning. marks
b Contrast block ciphers and stream ciphers. Provide two examples of each. marks
c Explain the concept of differential cryptanalysis and how it can be used to exploit weaknesses in block ciphers. Provide an example of a vulnerable cipher. marks
d Describe how a frequency analysis attack can be carried out on a substitution cipher. marks
e How does brute force differ from other cryptanalysis techniques? Provide an example of a cipher vulnerable to brute force. marks
f Modes of operation are algorithms that specify how a block cipher is used to encrypt a message that is longer than the block size. Briefly discuss the three modes of operation. marks
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


