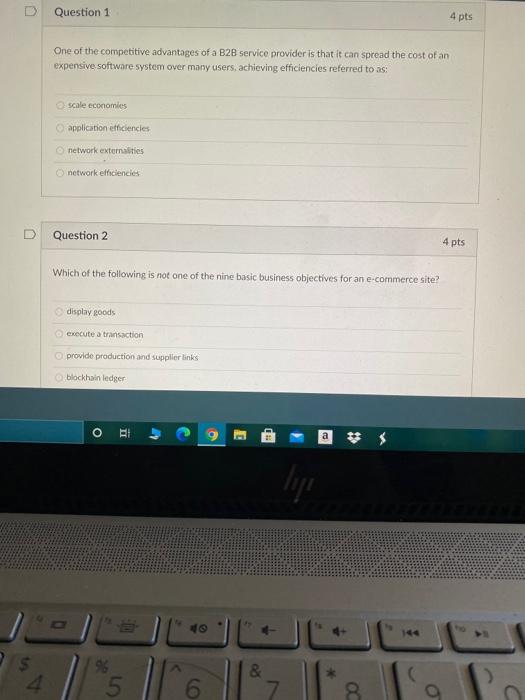
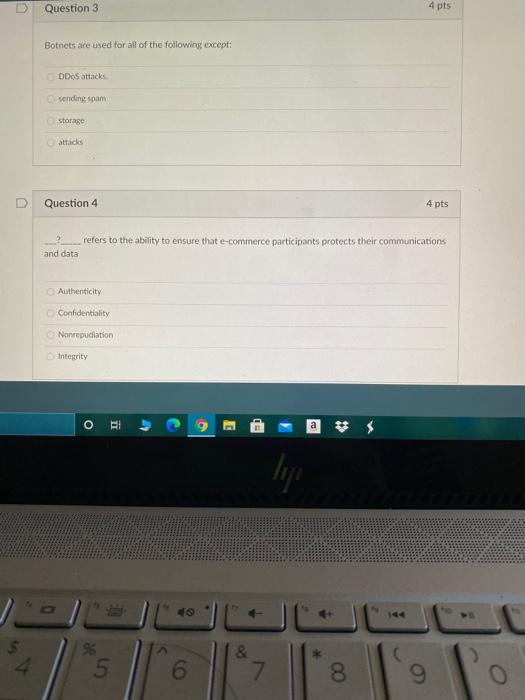
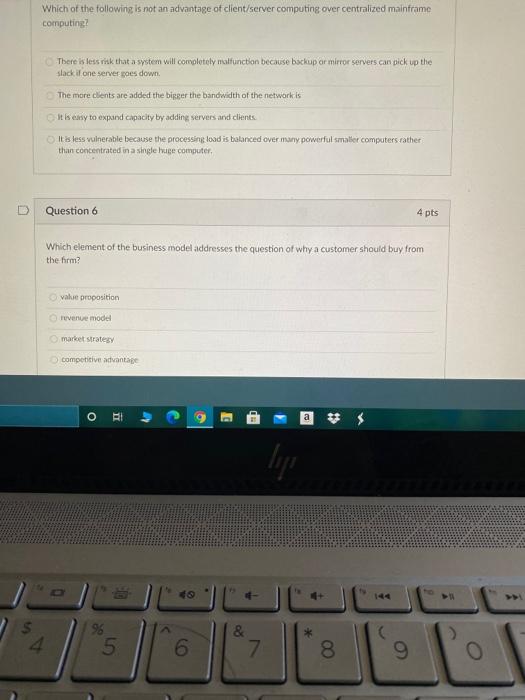
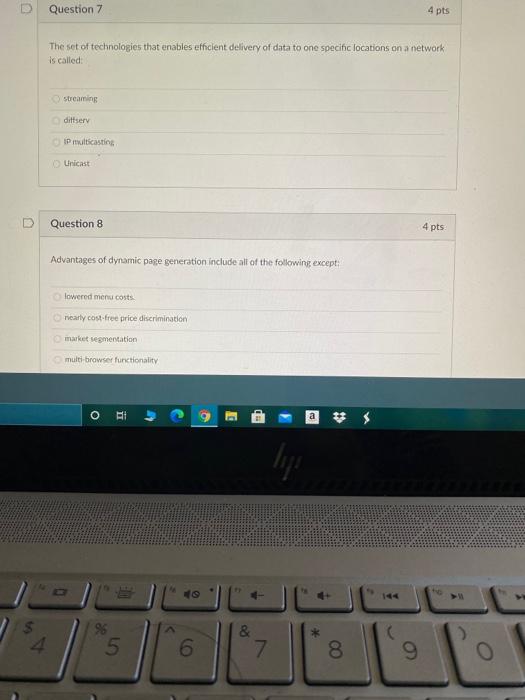
@ Question 1 4 pts One of the competitive advantages of a B2B service provider is that it can spread the cost of an expensive software system over many users, achieving efficiencies referred to as: scale economies application efficiencies network externalities network efficiencies Question 2 4 pts Which of the following is not one of the nine basic business objectives for an e-commerce site? display goods execute a transaction provide production and supplier links blockhain ledger BI lije a $ 4. % & 5 6. 8. Question 3 4 pts Botnets are used for all of the following except: DDoS attacks sending spam storage attacks Question 4 4 pts refers to the ability to ensure that e-commerce participants protects their communications and data Authenticity Confidentiality Nonrepudiation Integrity O 9 E lip % 4 5 6 & 7 8 9. Which of the following is not an advantage of client/server computing over centralized mainframe computing? There is less in that a system will completely malfunction because backup or mirror servers can pick up the slack i one server goes down. The more clients are added the bigger the bandwidth of the network is It is easy to expand capacity by adding servers and clients It is less vulnerable because the processing load is balanced over many powerful smaller computers rather than concentrated in a single huge computer, Question 6 4 pts Which element of the business model addresses the question of why a customer should buy from the form? value proposition revenue model market strategy competitive advantage O Y du a lip 0 & 4. 96 5 6 7. 8 9 Question 7 4 pts The set of technologies that enables efficient delivery of data to one specific locations on a network is called streaming dittserv multicasting Unicast Question 8 4 pts Advantages of dynamic page generation include all of the following except: lowered menu costs ricarly cost-free price discrimination market segmentation multi-browser functionality o . a * 5 6 & 7 8 9 O Question 4 pts The existence of a large number of competitors in any one market segment may indicate: a market that has already been tried without success the market 6 saturated an untapped market niche no one has differentiated itself within that market. D Question 10 4 pts Which of the following systems is required to understand the marketing effectiveness of your e- commerce site? site tracking and reporting system shopping Cart product database Inventory management system O BI $ 5 6 & 7 8 9 USSI Cerce building a team with the right skill sets and closely managing the development process having an accurate understanding of your business environment and an achievable business plan developing a clear understanding of business objectives and knowing how to choose the right technology to achieve those objectives identifying the key components of your business plan and selecting the right software. Iardware, and infrastructure for your site Question 12 4 pts Which of the following is not a true statement about the online brokerage market? Online stockbrokers charge commissions that are considerably less than traditional brokers Significant consolidation is now occurring in the industry Traditional brokerageshwe been unable to mount an effective challenge to the pure online brokerages First movers initially dominated the market. o a lipi $ 5 6 7 8 All of the following are simple steps for optimizing Web page content that can reduce response tines except using more ethicient graphics avoiding unnecessary links to other pages on the site segmenting computer servers to perform dedicated functions reducing unnecessary HTML Comments D Question 14 4 pts The process of sending packets along different minimum delay communication paths as they become available is called pachet switching routing the File Transfer Protocol the Transmission Control Protocol O lige 5 8 4 96 5 6 L 7 8 9 R. T T Y U Question 15 4 pts Recency refers to the percentage of existing customers who continue to buy on a regular basis time elapsed since the last action taken by a customer percentage of customers who do not retuite during the next year after an initial purchase percentage of customers who return to the site within a year to make additional purchases Question 16 4 pts When talking about the physical elements of the Internet the term redundancy refers to Multiple clients the use of tired Nigh-speed switching computers to connect the backbone to regional and local networks multicle ISP delays in messages caused by the uneven now of information through the network None of them AY 3 lip % * 4. 5 6 7 8 9 R. T Question 17 4 pts The richness made possible by e-commerce technologies does which of the following? It enables worldwide customer service and marketing communications It allows video, audio and text to be integrated into a single marketing message and consuming experience It aliow.consumers to become co-producers of the goods and services being sold It reduces the cost of delivering marketing messages and receiving feedback from users D Question 18 4 pts Which of the following is used to process certificates and private public key information? FTPS TES data capture tools HTTP O EI w E ly 4. 5 0) & 7 00 9 R. R T T Question 19 4 pts All the following statements about symmetric key encryption are true except: The bigger the key size the more secure a symmetric encryption is the US Government standard today is AES for symmetric key encryption in symmetric key encryption, both the sender and the receiver use the same key to encrypt and decrypt a message: symmetric key encryption is a key element in digital envelopes. the Data Encryption Standard is a symmetric key encryption system OO symmetric key encryption is computationally slower than asymmetric key encryption AES is an algorithm that has symmetric key encryption Question 20 4 pts The Transport Layer of TCP/IP is responsible for which of the following? providing communication with the application by acknowledging and sequencing the packets to and from the application addressing, packaging, and routing messages providing a variety of applications with the ability to access the services of the lower layers placing packets on and receiving them from the network medium D Question 21 4 pts Which of the following types of online market segmentation and targeting involves tracking the actions users take on a Web Site? o contextual technical behavioral psychographic $ 3 g E G 40 @ Question 1 4 pts One of the competitive advantages of a B2B service provider is that it can spread the cost of an expensive software system over many users, achieving efficiencies referred to as: scale economies application efficiencies network externalities network efficiencies Question 2 4 pts Which of the following is not one of the nine basic business objectives for an e-commerce site? display goods execute a transaction provide production and supplier links blockhain ledger BI lije a $ 4. % & 5 6. 8. Question 3 4 pts Botnets are used for all of the following except: DDoS attacks sending spam storage attacks Question 4 4 pts refers to the ability to ensure that e-commerce participants protects their communications and data Authenticity Confidentiality Nonrepudiation Integrity O 9 E lip % 4 5 6 & 7 8 9. Which of the following is not an advantage of client/server computing over centralized mainframe computing? There is less in that a system will completely malfunction because backup or mirror servers can pick up the slack i one server goes down. The more clients are added the bigger the bandwidth of the network is It is easy to expand capacity by adding servers and clients It is less vulnerable because the processing load is balanced over many powerful smaller computers rather than concentrated in a single huge computer, Question 6 4 pts Which element of the business model addresses the question of why a customer should buy from the form? value proposition revenue model market strategy competitive advantage O Y du a lip 0 & 4. 96 5 6 7. 8 9 Question 7 4 pts The set of technologies that enables efficient delivery of data to one specific locations on a network is called streaming dittserv multicasting Unicast Question 8 4 pts Advantages of dynamic page generation include all of the following except: lowered menu costs ricarly cost-free price discrimination market segmentation multi-browser functionality o . a * 5 6 & 7 8 9 O Question 4 pts The existence of a large number of competitors in any one market segment may indicate: a market that has already been tried without success the market 6 saturated an untapped market niche no one has differentiated itself within that market. D Question 10 4 pts Which of the following systems is required to understand the marketing effectiveness of your e- commerce site? site tracking and reporting system shopping Cart product database Inventory management system O BI $ 5 6 & 7 8 9 USSI Cerce building a team with the right skill sets and closely managing the development process having an accurate understanding of your business environment and an achievable business plan developing a clear understanding of business objectives and knowing how to choose the right technology to achieve those objectives identifying the key components of your business plan and selecting the right software. Iardware, and infrastructure for your site Question 12 4 pts Which of the following is not a true statement about the online brokerage market? Online stockbrokers charge commissions that are considerably less than traditional brokers Significant consolidation is now occurring in the industry Traditional brokerageshwe been unable to mount an effective challenge to the pure online brokerages First movers initially dominated the market. o a lipi $ 5 6 7 8 All of the following are simple steps for optimizing Web page content that can reduce response tines except using more ethicient graphics avoiding unnecessary links to other pages on the site segmenting computer servers to perform dedicated functions reducing unnecessary HTML Comments D Question 14 4 pts The process of sending packets along different minimum delay communication paths as they become available is called pachet switching routing the File Transfer Protocol the Transmission Control Protocol O lige 5 8 4 96 5 6 L 7 8 9 R. T T Y U Question 15 4 pts Recency refers to the percentage of existing customers who continue to buy on a regular basis time elapsed since the last action taken by a customer percentage of customers who do not retuite during the next year after an initial purchase percentage of customers who return to the site within a year to make additional purchases Question 16 4 pts When talking about the physical elements of the Internet the term redundancy refers to Multiple clients the use of tired Nigh-speed switching computers to connect the backbone to regional and local networks multicle ISP delays in messages caused by the uneven now of information through the network None of them AY 3 lip % * 4. 5 6 7 8 9 R. T Question 17 4 pts The richness made possible by e-commerce technologies does which of the following? It enables worldwide customer service and marketing communications It allows video, audio and text to be integrated into a single marketing message and consuming experience It aliow.consumers to become co-producers of the goods and services being sold It reduces the cost of delivering marketing messages and receiving feedback from users D Question 18 4 pts Which of the following is used to process certificates and private public key information? FTPS TES data capture tools HTTP O EI w E ly 4. 5 0) & 7 00 9 R. R T T Question 19 4 pts All the following statements about symmetric key encryption are true except: The bigger the key size the more secure a symmetric encryption is the US Government standard today is AES for symmetric key encryption in symmetric key encryption, both the sender and the receiver use the same key to encrypt and decrypt a message: symmetric key encryption is a key element in digital envelopes. the Data Encryption Standard is a symmetric key encryption system OO symmetric key encryption is computationally slower than asymmetric key encryption AES is an algorithm that has symmetric key encryption Question 20 4 pts The Transport Layer of TCP/IP is responsible for which of the following? providing communication with the application by acknowledging and sequencing the packets to and from the application addressing, packaging, and routing messages providing a variety of applications with the ability to access the services of the lower layers placing packets on and receiving them from the network medium D Question 21 4 pts Which of the following types of online market segmentation and targeting involves tracking the actions users take on a Web Site? o contextual technical behavioral psychographic $ 3 g E G 40