Question
Question 1 Q.1.1 Using suitable examples, discuss how you would use the three information security (12) layers to secure a student information database for
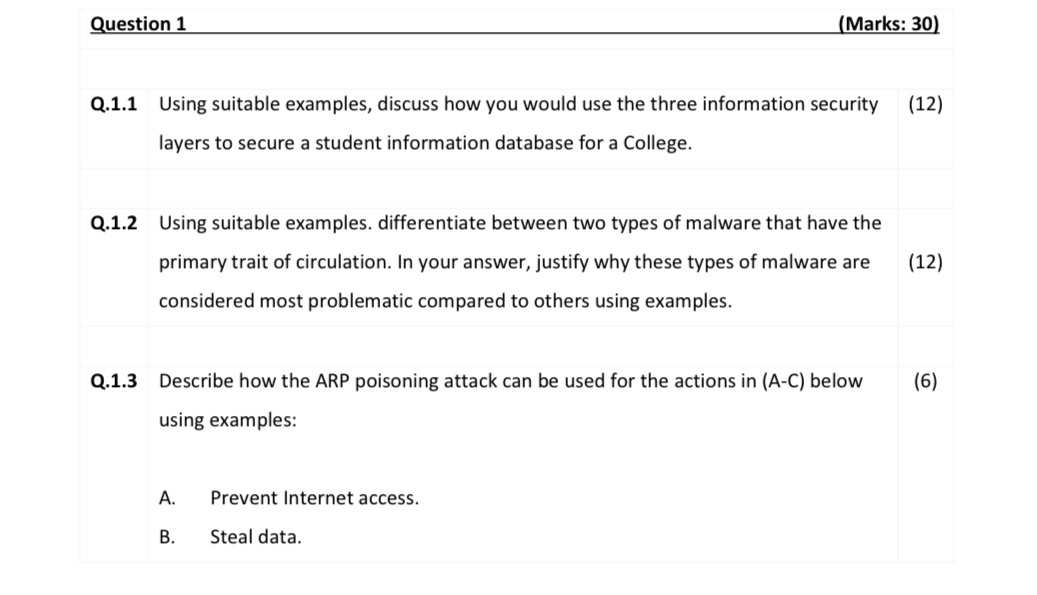
Question 1 Q.1.1 Using suitable examples, discuss how you would use the three information security (12) layers to secure a student information database for a College. Q.1.2 Using suitable examples. differentiate between two types of malware that have the primary trait of circulation. In your answer, justify why these types of malware are considered most problematic compared to others using examples. (Marks: 30) Q.1.3 Describe how the ARP poisoning attack can be used for the actions in (A-C) below using examples: A. B. Prevent Internet access. Steal data. (12) (6)
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get StartedRecommended Textbook for
Cost Accounting Foundations and Evolutions
Authors: Michael R. Kinney, Cecily A. Raiborn
8th Edition
9781439044612, 1439044619, 978-1111626822
Students also viewed these Computer Network questions
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
View Answer in SolutionInn App



