Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Question 22 You want to allow only machines in your local network to access your intranet server. Briefly explain how you may design firewall
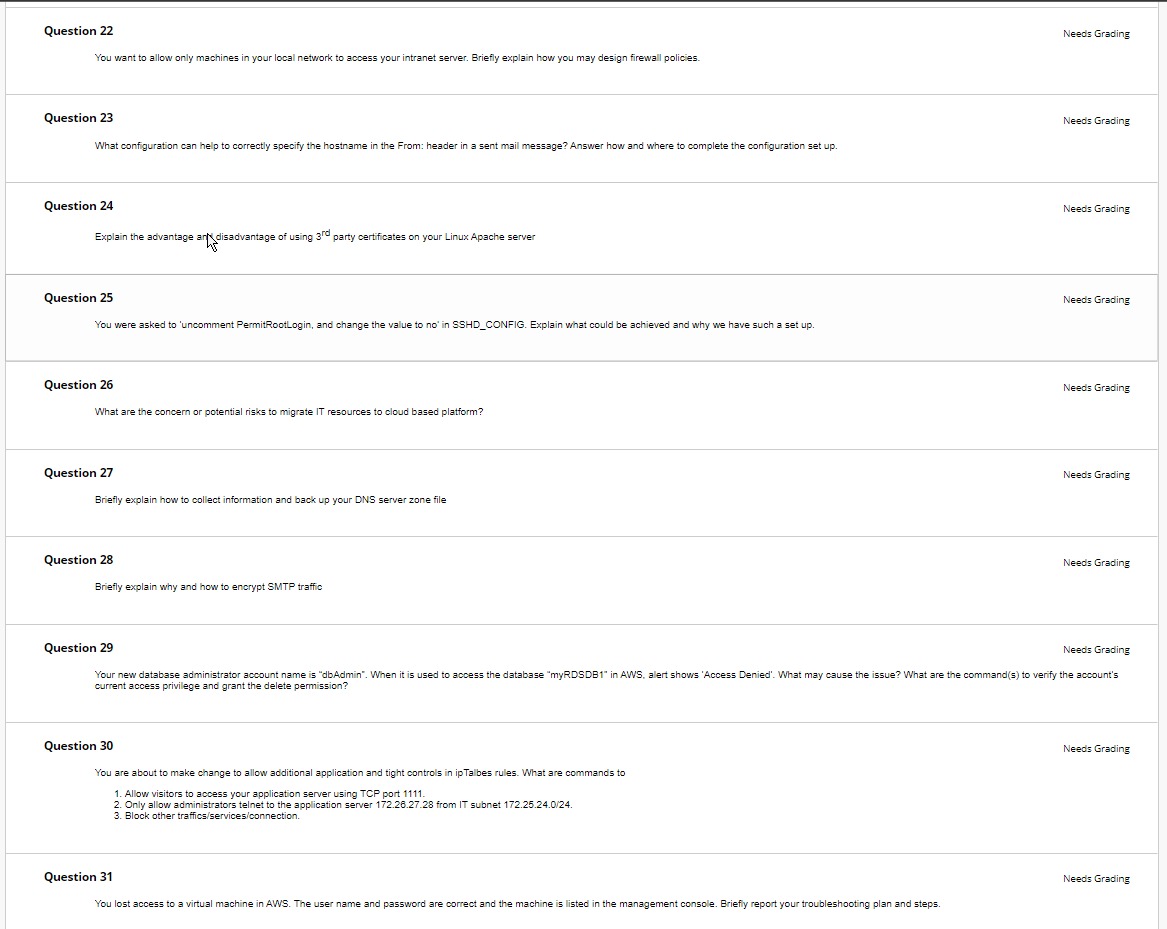
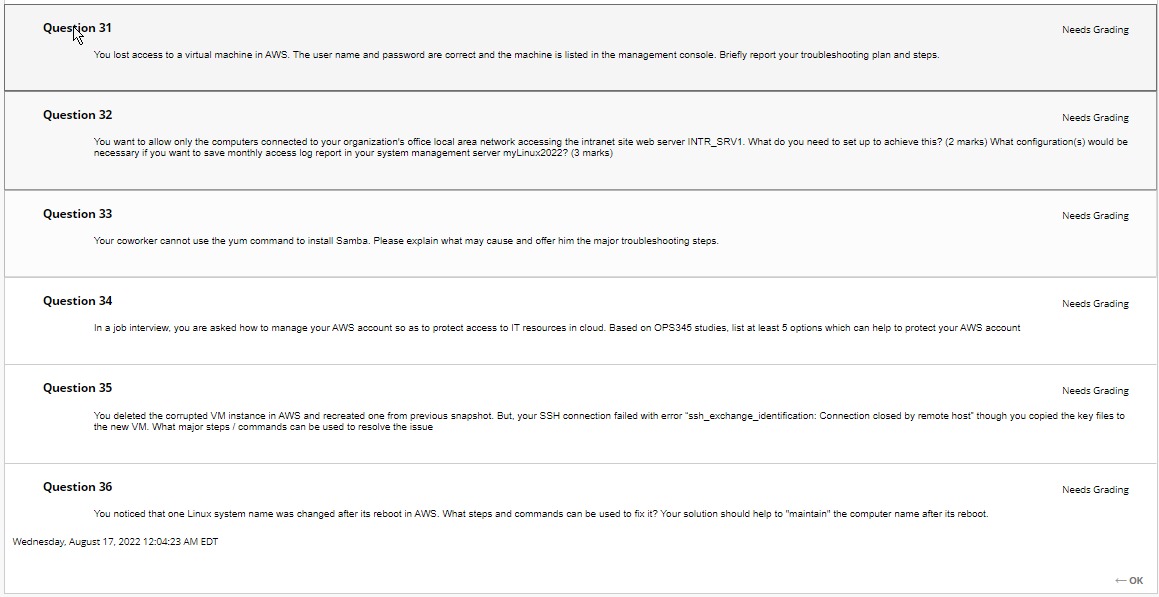
Question 22 You want to allow only machines in your local network to access your intranet server. Briefly explain how you may design firewall policies. Needs Grading Question 23 Needs Grading What configuration can help to correctly specify the hostname in the From: header in a sent mail message? Answer how and where to complete the configuration set up. Question 24 Explain the advantage ar disadvantage of using 3rd party certificates on your Linux Apache server Needs Grading Question 25 Needs Grading You were asked to 'uncomment PermitRootLogin, and change the value to no' in SSHD_CONFIG. Explain what could be achieved and why we have such a set up. Question 26 What are the concern or potential risks to migrate IT resources to cloud based platform? Question 27 Briefly explain how to collect information and back up your DNS server zone file Question 28 Briefly explain why and how to encrypt SMTP traffic Needs Grading Needs Grading Needs Grading Question 29 Needs Grading Your new database administrator account name is "dbAdmin". When it is used to access the database "myRDSDB1" in AWS, alert shows 'Access Denied'. What may cause the issue? What are the command(s) to verify the account's current access privilege and grant the delete permission? Question 30 You are about to make change to allow additional application and tight controls in ip Talbes rules. What are commands to 1. Allow visitors to access your application server using TCP port 1111. 2. Only allow administrators telnet to the application server 172.26.27.28 from IT subnet 172.25.24.0/24. 3. Block other traffics/services/connection. Needs Grading Question 31 Needs Grading You lost access to a virtual machine in AWS. The user name and password are correct and the machine is listed in the management console. Briefly report your troubleshooting plan and steps. Question 31 Needs Grading You lost access to a virtual machine in AWS. The user name and password are correct and the machine is listed in the management console. Briefly report your troubleshooting plan and steps. Question 32 Needs Grading You want to allow only the computers connected to your organization's office local area network accessing the intranet site web server INTR_SRV1. What do you need to set up to achieve this? (2 marks) What configuration(s) would be necessary if you want to save monthly access log report in your system management server myLinux2022? (3 marks) Question 33 Your coworker cannot use the yum command to install Samba. Please explain what may cause and offer him the major troubleshooting steps. Needs Grading Question 34 Needs Grading In a job interview, you are asked how to manage your AWS account so as to protect access to IT resources in cloud. Based on OPS345 studies, list at least 5 options which can help to protect your AWS account Question 35 Needs Grading You deleted the corrupted VM instance in AWS and recreated one from previous snapshot. But, your SSH connection failed with error "ssh_exchange_identification: Connection closed by remote host" though you copied the key files to the new VM. What major steps / commands can be used to resolve the issue Question 36 Needs Grading You noticed that one Linux system name was changed after its reboot in AWS. What steps and commands can be used to fix it? Your solution should help to "maintain" the computer name after its reboot. Wednesday, August 17, 2022 12:04:23 AM EDT -OK
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


