Answered step by step
Verified Expert Solution
Question
1 Approved Answer
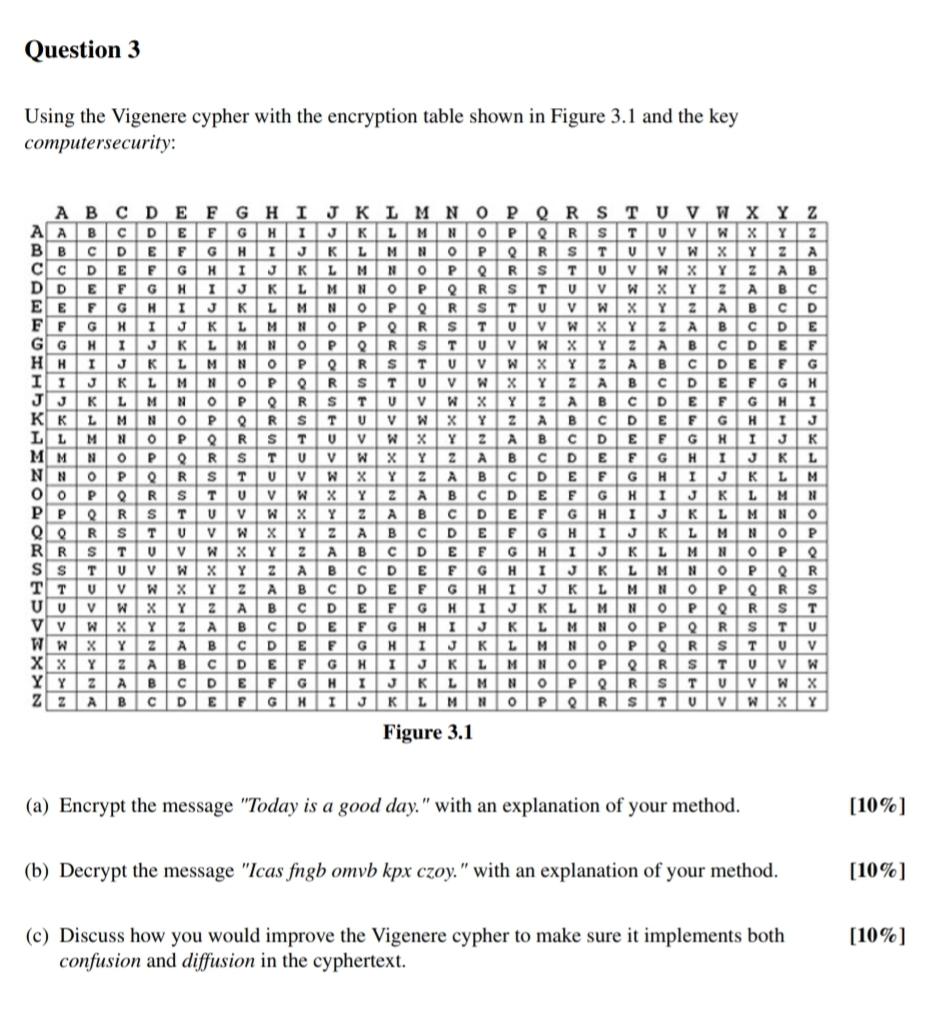
Question 3 Using the Vigenere cypher with the encryption table shown in Figure 3 . 1 and the keycomputersecurity:A BC DE FG H IAAB C
Question Using the Vigenere cypher with the encryption table shown in Figure and the keycomputersecurity:A BC DE FG H IAAB C DBBCC c DD D EEE FF FGGHI HKKIIJJ KGMMHLLMNNOoPPPRR sSIs TTTX x YZQR SY Y FKAMPWWX YVWBGHTMNPRVL MYABCF GHI JGHKLE FGH IRTYABH IJKI JK LPoP oRK LMK L MNLMNOPW XY VW X YAW X Y AzQRsQRsTRSTUSTUv WVWXY ZA BABJ KL M NO PORS T UV W X Y ZJKLM NOPQRSTUVW X YLM N OPQR S TQRs TQRsTR s TUSTUvwTUV WA BCMcDNCDDGMHNBR SSTWC DYEEGRJTWYADGJKPRSVXYABDGKPVW x YYA BcDBCD ECDEFHY K ABABCDEFG HE FGHFGHI JFigure IL MGL MNNPAH IJ K LJK LEFGMNVx Y AB DERWABCHRVSX YABCDGHJMPx Y z ARSBCDECDEF GDEHKGI J KPRLMMNoPSULOPI JK LJKL MKL M NPCa Encrypt the message "Today is a good day." with an explanation of your method.b Decrypt the message "Icas fngb omvb kpx czoy." with an explanation of your method.Hc Discuss how you would improve the Vigenere cypher to make sure it implements bothconfusion and diffusion in the cyphertext.JoPRTMNoP
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


