Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Question 4 Considering digital envelopes, message authentication and digital signatures, answer parts ( a ) , ( b ) and ( c ) . The
Question
Considering digital envelopes, message authentication and digital signatures, answer parts a
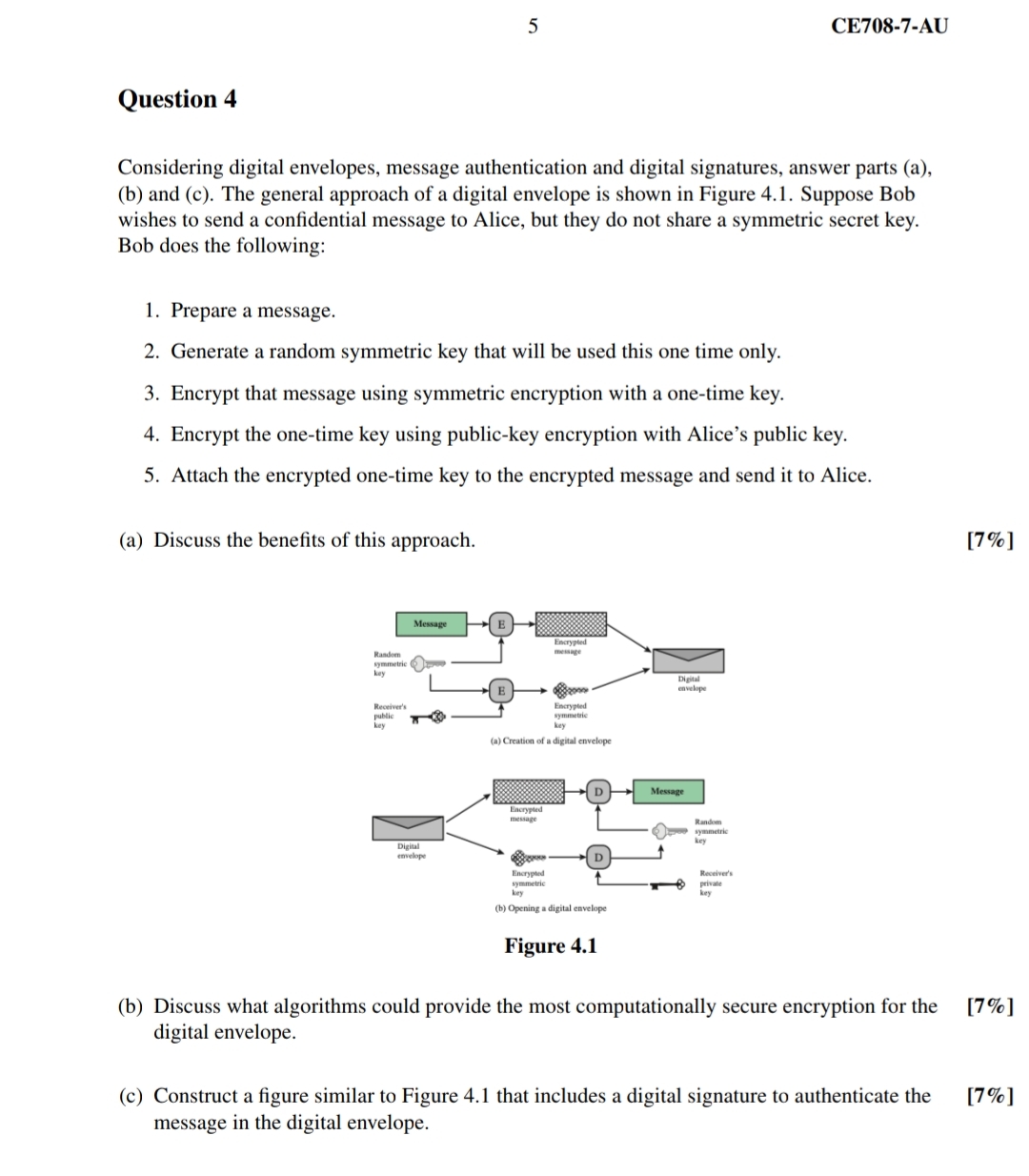
b and c The general approach of a digital envelope is shown in Figure Suppose Bob
wishes to send a confidential message to Alice, but they do not share a symmetric secret key.
Bob does the following:
Prepare a message.
Generate a random symmetric key that will be used this one time only.
Encrypt that message using symmetric encryption with a onetime key.
Encrypt the onetime key using publickey encryption with Alice's public key.
Attach the encrypted onetime key to the encrypted message and send it to Alice.
a Discuss the benefits of this approach.
b Discuss what algorithms could provide the most computationally secure encryption for the
digital envelope.
c Construct a figure similar to Figure that includes a digital signature to authenticate the
message in the digital envelope.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


