Answered step by step
Verified Expert Solution
Question
1 Approved Answer
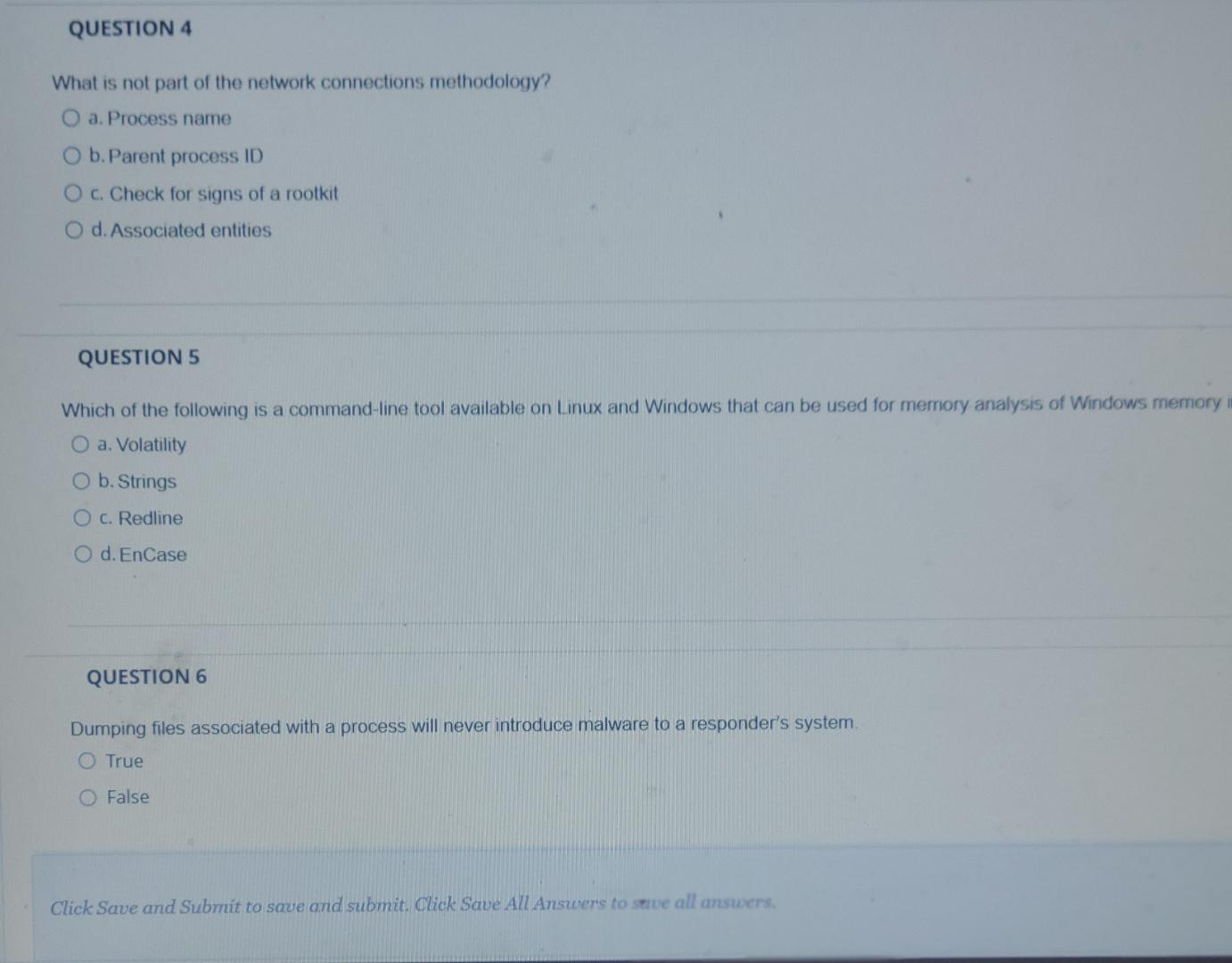
QUESTION 4 What is not part of the network connections methodology? a . Process name b . Parent process ID c . Check for signs
QUESTION
What is not part of the network connections methodology?
a Process name
b Parent process ID
c Check for signs of a rootkit
d Associated entities
QUESTION
Which of the following is a commandline tool available on Linux and Windows that can be used for memory analysis of Windows memory
a Volatility
b Strings
c Redline
d EnCase
QUESTION
Dumping files associated with a process will never introduce malware to a responder's system.
True
False
Click Save and Submit to save and submit. Click Save All Answers to swe all answers.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


