Answered step by step
Verified Expert Solution
Question
1 Approved Answer
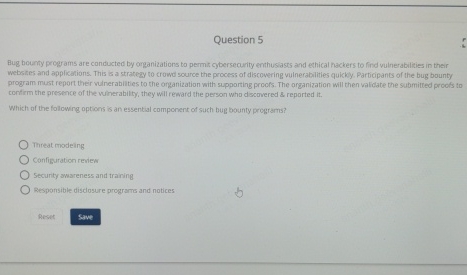
Question 5 Bug bounfy programs are conducted by onganizations to permi cytersenuity enthusla s and ethical nackers to find vulnerabilises in their websites and appications.
Question
Bug bounfy programs are conducted by onganizations to permi cytersenuity enthusla s and ethical nackers to find vulnerabilises in their websites and appications. This is a straregy to crowd source the process of discowering vulnerabilities quickly. Participants of the bug bounty orogram must report their vulnerabilies to the onganization with supporting procos. The organtzation will then whldate the sthmitted procfs to contirm the presence of the vuinerabilty, they will reward the person who doctvered & reparted it
Which of the following aptions is an essential component of such bug bounty programs?
Threat modeing
Confisuration review
Secunty owsreness and trairing
Responsible disdosure programs and notices
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


