Question
Question 6 Alice wants to authenticate herself with Bob. Now, Bob to prevent DOS attack decides not to store any state (e.g., not to remember
Question 6
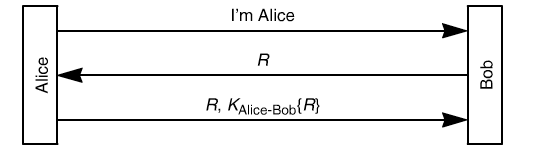
Alice wants to authenticate herself with Bob. Now, Bob to prevent DOS attack decides not to store any state (e.g., not to remember any random number). So the protocol they come up with is as shown in the image. Bob sends a Random number as challenge to Alice but promptly forgets it. Alice then responds back with both the random number and the encrypted version. Alice does remember the random number for a while. Which of the following are potential attacks on this protocol?
Question 6 options:
|
| Replay attack, where Trudy can replay the random number and its encrypted form to Bob. |
|
| Off-line dictionary attack - where Trudy spoofs Bob and sends her own choice of message to Alice. She then gets back from Alice the encrypted version of the text, making it easier for her to break the encryption. |
|
| Replay attack, where Trudy can replay the random number again to Alice and spoof Bob. |
|
| Off-line dictionary attack, where Trudy eavesdrops on the third message and gets a copy of the random number and its encrypted text. |
Question 7
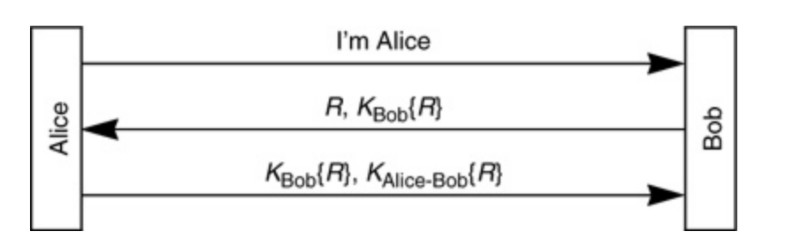
To fix atleast one possible attack of the previous protocol (protocol used in the previous question), a new protocol is created as shown in the image. Which of the following are potential attacks on this protocol?
| Off-line dictionary attack, where Trudy eavesdrops on the third message and gets a copy of the random number and its encrypted text. | |
| Replay attack, where Trudy can replay the random number and its encrypted form to Bob. | |
| Replay attack, where Trudy can replay the random number again to Alice and spoof Bob. | |
| Off-line dictionary attack - where Trudy spoofs Bob and sends her own choice of message to Alice. She then gets back from Alice the encrypted version of the text, making it easier for her to break the encryption. |
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


