Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Question 6 The SHA-2 hashes of 32-bit and 64-bit versions of Kali Linux have been analyzed to ensure file integrity. Output of the analysis
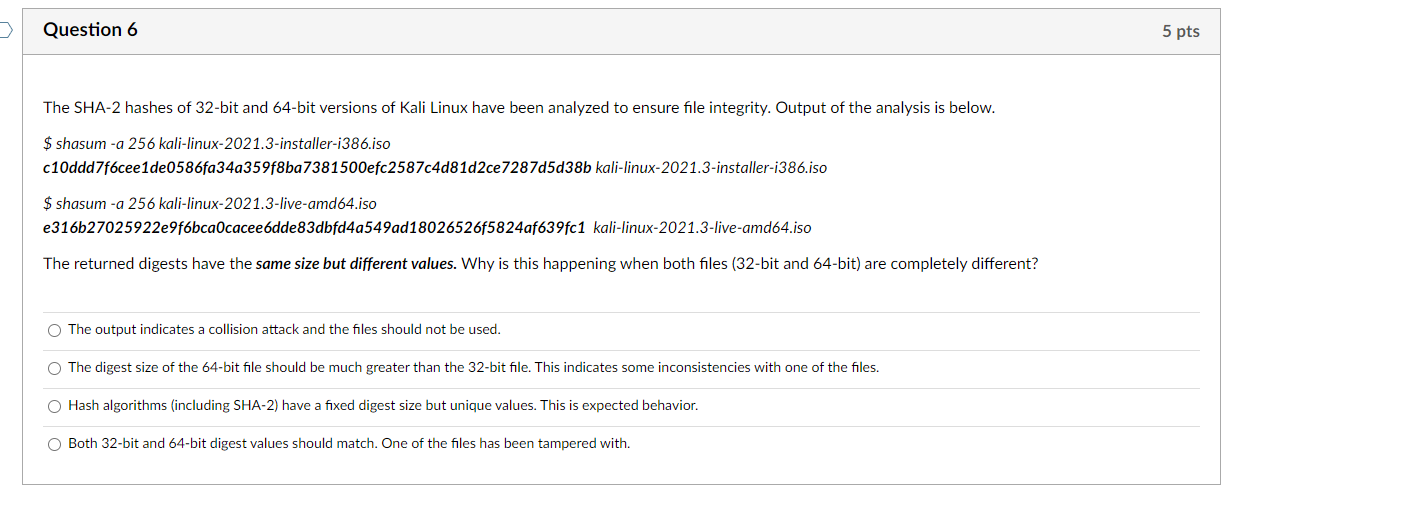
Question 6 The SHA-2 hashes of 32-bit and 64-bit versions of Kali Linux have been analyzed to ensure file integrity. Output of the analysis is below. $ shasum -a 256 kali-linux-2021.3-installer-i386.iso c10ddd7f6cee1de0586fa34a359f8ba7381500efc2587c4d81d2ce7287d5d38b kali-linux-2021.3-installer-i386.iso $ shasum -a 256 kali-linux-2021.3-live-amd64.iso e316b27025922e9f6bca0cacee6dde83dbfd4a549ad18026526f5824af639fc1 kali-linux-2021.3-live-amd64.iso The returned digests have the same size but different values. Why is this happening when both files (32-bit and 64-bit) are completely different? The output indicates a collision attack and the files should not be used. The digest size of the 64-bit file should be much greater than the 32-bit file. This indicates some inconsistencies with one of the files. Hash algorithms (including SHA-2) have a fixed digest size but unique values. This is expected behavior. Both 32-bit and 64-bit digest values should match. One of the files has been tampered with. 00 5 pts
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


