Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Questions on Cryptography and Bitcoin. (a) (6 points) Describe how the Sybil Attack problem manifests in Bitcoin. That is, do not give a general definition
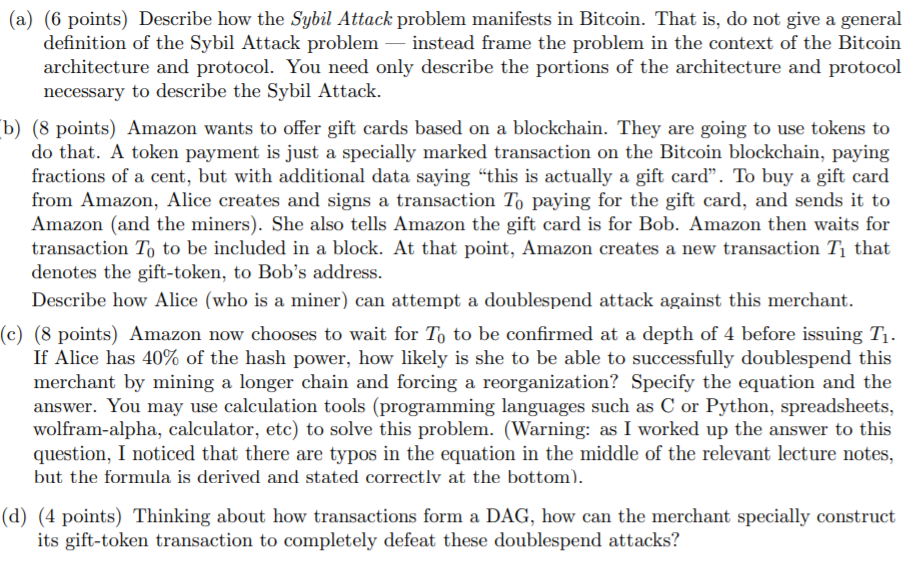
Questions on Cryptography and Bitcoin.
(a) (6 points) Describe how the Sybil Attack problem manifests in Bitcoin. That is, do not give a general definition of the Sybil Attack problem - instead frame the problem in the context of the Bitcoin architecture and protocol. You need only describe the portions of the architecture and protocol necessary to describe the Sybil Attack. b) (8 points) Amazon wants to offer gift cards based on a blockchain. They are going to use tokens to do that. A token payment is just a specially marked transaction on the Bitcoin blockchain, paying fractions of a cent, but with additional data saying "this is actually a gift card. To buy a gift card from Amazon, Alice creates and signs a transaction To paying for the gift card, and sends it to Amazon (and the miners). She also tells Amazon the gift card is for Bob. Amazon then waits for transaction To to be included in a block. At that point, Amazon creates a new transaction T that denotes the gift-token, to Bob's address. Describe how Alice (who is a miner) can attempt a doublespend attack against this merchant. (c) (8 points) Amazon now chooses to wait for To to be confirmed at a depth of 4 before issuing Tj. If Alice has 40% of the hash power, how likely is she to be able to successfully doublespend this merchant by mining a longer chain and forcing a reorganization? Specify the equation and the answer. You may use calculation tools (programming languages such as C or Python, spreadsheets, wolfram-alpha, calculator, etc) to solve this problem. (Warning: as I worked up the answer to this question, I noticed that there are typos in the equation in the middle of the relevant lecture notes, but the formula is derived and stated correctly at the bottom). (d) (4 points) Thinking about how transactions form a DAG, how can the merchant specially construct its gift-token transaction to completely defeat these doublespend attacks? (a) (6 points) Describe how the Sybil Attack problem manifests in Bitcoin. That is, do not give a general definition of the Sybil Attack problem - instead frame the problem in the context of the Bitcoin architecture and protocol. You need only describe the portions of the architecture and protocol necessary to describe the Sybil Attack. b) (8 points) Amazon wants to offer gift cards based on a blockchain. They are going to use tokens to do that. A token payment is just a specially marked transaction on the Bitcoin blockchain, paying fractions of a cent, but with additional data saying "this is actually a gift card. To buy a gift card from Amazon, Alice creates and signs a transaction To paying for the gift card, and sends it to Amazon (and the miners). She also tells Amazon the gift card is for Bob. Amazon then waits for transaction To to be included in a block. At that point, Amazon creates a new transaction T that denotes the gift-token, to Bob's address. Describe how Alice (who is a miner) can attempt a doublespend attack against this merchant. (c) (8 points) Amazon now chooses to wait for To to be confirmed at a depth of 4 before issuing Tj. If Alice has 40% of the hash power, how likely is she to be able to successfully doublespend this merchant by mining a longer chain and forcing a reorganization? Specify the equation and the answer. You may use calculation tools (programming languages such as C or Python, spreadsheets, wolfram-alpha, calculator, etc) to solve this problem. (Warning: as I worked up the answer to this question, I noticed that there are typos in the equation in the middle of the relevant lecture notes, but the formula is derived and stated correctly at the bottom). (d) (4 points) Thinking about how transactions form a DAG, how can the merchant specially construct its gift-token transaction to completely defeat these doublespend attacksStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


