Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Read the following case study and answer below questions: Case study: Information Security Risk Management at XYZ Company XYZ Company is a mid-sized Financial Technology

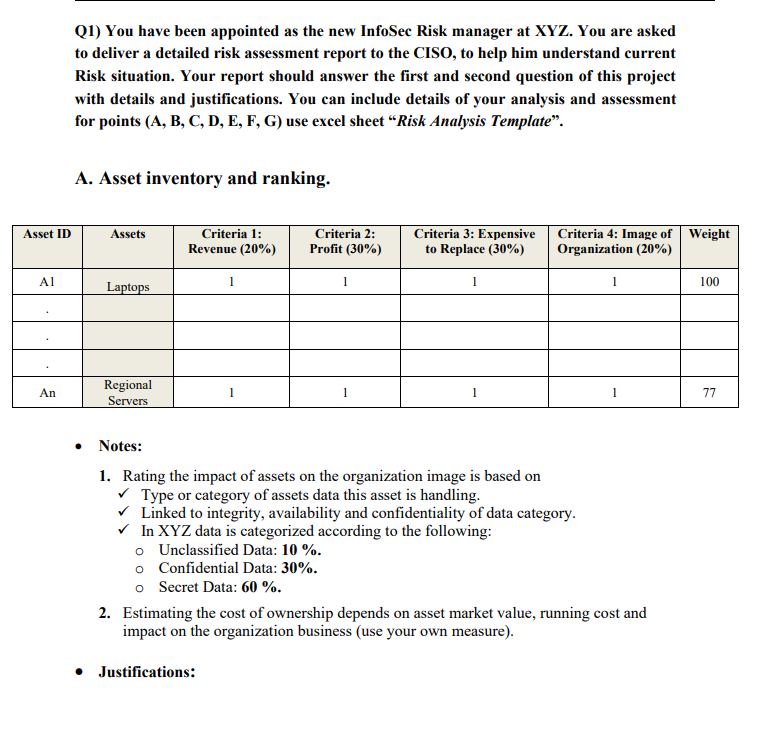 Read the following case study and answer below questions: Case study: Information Security Risk Management at XYZ Company XYZ Company is a mid-sized Financial Technology (Fintech) company that operates in the Fintech consultation and services provisioning business. The company has a range of departments such as HR, Customer service, Research and Development, marketing and Finance. The company provides services to its clients either in B2B or B2C model such as financial advices in investment. It also provides payment settlements and insurance products. The management at XYZ Company was concerned about the risks associated with information security, especially given the sensitive financial data that the company handles. Hence, the company decided to implement an information risk management program to mitigate these risks. The second key component of risk management is the identification of potential threats to these assets, which are not limited to cyber Attacks, data breaches, and employee errors. In addition, malware attacks, DoS/DDos attacks, phishing attacks, activity interruption and theft of personal data or intellectual property of provided products. Looking at XYZ Company's information technology context, its web site and e-services platform system are hosted on a cloud service provider. This allows XYZ to provide several online services to its clients and employees with a minimum equipment and maintenance costs. In addition, XYZ hosts some of its critical services and products within its internal data center. Access to all these online services is based on credentials offering access privileges to online users. Accordingly, credentials issuance, verification and utilization need careful attention especially for new enrolled employees or on-boarded clients. Hence, detailed bounds of cloud service provisioning needs to be considered. Network administrators at XYZ utilize Remote Desktop Protocol (RDP), which provides a graphical user interface for remote access connections over the network. Also, network administrators use telnet access to specific server machines to conduct some of their operations remotely. In addition, XYZ increased its dependability on third party for its applications and software development and implementation to fulfill increased customer demands. More network accessibility services are offered to XYZ employees, allowing them to bring and connect their own devices to company without device vulnerability scanning. Based on such details, XYZ Company is aiming to develop a comprehensive risk management plan. Q1) You have been appointed as the new InfoSec Risk manager at XYZ. You are asked to deliver a detailed risk assessment report to the CISO, to help him understand current Risk situation. Your report should answer the first and second question of this project with details and justifications. You can include details of your analysis and assessment for points (A, B, C, D, E, F, G) use excel sheet "Risk Analysis Template". A. Asset inventory and ranking. - Notes: 1. Rating the impact of assets on the organization image is based on Type or category of assets data this asset is handling. Linked to integrity, availability and confidentiality of data category. In XYZ data is categorized according to the following: - Unclassified Data: 10%. - Confidential Data: 30%. - Secret Data: 60%. 2. Estimating the cost of ownership depends on asset market value, running cost and impact on the organization business (use your own measure)
Read the following case study and answer below questions: Case study: Information Security Risk Management at XYZ Company XYZ Company is a mid-sized Financial Technology (Fintech) company that operates in the Fintech consultation and services provisioning business. The company has a range of departments such as HR, Customer service, Research and Development, marketing and Finance. The company provides services to its clients either in B2B or B2C model such as financial advices in investment. It also provides payment settlements and insurance products. The management at XYZ Company was concerned about the risks associated with information security, especially given the sensitive financial data that the company handles. Hence, the company decided to implement an information risk management program to mitigate these risks. The second key component of risk management is the identification of potential threats to these assets, which are not limited to cyber Attacks, data breaches, and employee errors. In addition, malware attacks, DoS/DDos attacks, phishing attacks, activity interruption and theft of personal data or intellectual property of provided products. Looking at XYZ Company's information technology context, its web site and e-services platform system are hosted on a cloud service provider. This allows XYZ to provide several online services to its clients and employees with a minimum equipment and maintenance costs. In addition, XYZ hosts some of its critical services and products within its internal data center. Access to all these online services is based on credentials offering access privileges to online users. Accordingly, credentials issuance, verification and utilization need careful attention especially for new enrolled employees or on-boarded clients. Hence, detailed bounds of cloud service provisioning needs to be considered. Network administrators at XYZ utilize Remote Desktop Protocol (RDP), which provides a graphical user interface for remote access connections over the network. Also, network administrators use telnet access to specific server machines to conduct some of their operations remotely. In addition, XYZ increased its dependability on third party for its applications and software development and implementation to fulfill increased customer demands. More network accessibility services are offered to XYZ employees, allowing them to bring and connect their own devices to company without device vulnerability scanning. Based on such details, XYZ Company is aiming to develop a comprehensive risk management plan. Q1) You have been appointed as the new InfoSec Risk manager at XYZ. You are asked to deliver a detailed risk assessment report to the CISO, to help him understand current Risk situation. Your report should answer the first and second question of this project with details and justifications. You can include details of your analysis and assessment for points (A, B, C, D, E, F, G) use excel sheet "Risk Analysis Template". A. Asset inventory and ranking. - Notes: 1. Rating the impact of assets on the organization image is based on Type or category of assets data this asset is handling. Linked to integrity, availability and confidentiality of data category. In XYZ data is categorized according to the following: - Unclassified Data: 10%. - Confidential Data: 30%. - Secret Data: 60%. 2. Estimating the cost of ownership depends on asset market value, running cost and impact on the organization business (use your own measure) Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


