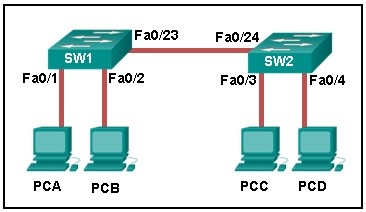
Refer to the exhibit. How is a frame sent from PCA forwarded to PCC if the MAC address table on switch SW1 is empty?
Question 4 options:
| | | a) | SW1 floods the frame on all ports on SW1, excluding the port through which the frame entered the switch. | |
| | | b) | SW1 floods the frame on all ports on the switch, excluding the interconnected port to switch SW2 and the port through which the frame entered the switch. | |
| | | c) | SW1 drops the frame because it does not know the destination MAC address. | |
| | | d) | SW1 forwards the frame directly to SW2. SW2 floods the frame to all ports connected to SW2, excluding the port through which the frame entered the switch. | |
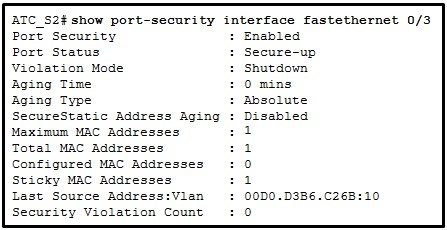
Q:6 Refer to the exhibit. What can be determined about port security from the information that is shown?
Question 6 options:
| | | a) | The port has been shut down. | |
| | | b) | The port has two attached devices. | |
| | | c) | The port violation mode is not the default for any port that has port security enabled. | |
| | | d) | The port has the maximum number of MAC addresses that is supported by a Layer 2 switch port which is configured for port security. | |
| | |
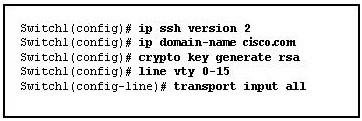
Q9:Refer to the exhibit. The network administrator wants to configure Switch1 to allow SSH connections and prohibit Telnet connections. How should the network administrator change the displayed configuration to satisfy the requirement?
Question 9 options:
| | |
| | | b) | Reconfigure the RSA key. | |
| | | c) | Configure SSH on a different line. | |
| | | d) | Specify to allow only SSH input. | |
| | |
Fa0/23 Fa0/24 Sw1 sW2 Fa0/1 Fa0/2 Fa0/3 Fa0/4 PCA PCB PCC PCD ATC S2#show port-security interface fastethernet 0/3 Port Security Port Status Violation Mode Aging Time Aging Type SecureStatic Address Aging Disabled Maximum MAC Addr e33e3 Total MAC Addresses Configured MAC Addresses 0 Sticky MAC Addresses Last Source Address:Vlan 00DO. D3B6.C26B: 10 Security Violation Count 0 : Enabled : Secure-up : Shutdown : 0 mins : Absolute 1 Switch! (config) ip ssh version 2 Switchl config) ip domain-name ciscocom Switchl (config) crypto key generate rsa Switch! (config)# line vty 0-15 Switch! (config-line) # transport input all









