Question
Scenario A college has two main operational sites which are five miles apart. With expansion, a new site is being developed particularly to cater for
Scenario
A college has two main operational sites which are five miles apart. With expansion, a new site is being developed particularly to cater for the Computing and Technology courses. This new site is almost ten miles from the two existing main sites. When ready, it will have state of the art technology, offering courses in the new fields of computing, particularly networking, data communications, wireless technology, multimedia and games developments to name but a few courses
It is expected that the new site as shown below, called the Technology Centre will cater for approximately 500 students in the first instance but will expand rapidly. In the ground floor there will be a lecturer theatre catering for approximately 400 computers, with facilities available for students to plug in their wireless laptops if needed, in the first floor there will be 4 classrooms equipped with 20 computers, in the second floor 3 rooms for staff and administration with a capacity of 20 computers in each room
You are the network manager who has been called in to advise the college management on how to build a network for the new site and advise on future expansion plans. The network you propose for the new site will need to be connected to the other two sites of the college, and should cater for all the student curriculum needs, staff and requirements specification. The network will need to support all floors see the diagram below
-The workstations will need secure, fast and robust access to the company database
-Staff will be expected to use email as a regular communication method and have access to the World Wide Web
-There will need to be provision for some, heavily controlled wireless access
-Security is a main priority as confidential information will be in constant use and is covered by GDPR
-There will need to be control of user accounts, system access, resource sharing and access permissions across the network you design
-There will need to be secure broadband access via the company Virtual Private Network to the different campuses
-It is proposed to use an intranet to disseminate company information internally to this site. Core hardware must be kept in a secure place
Task
A- Discuss the benefits and constraints of the above network
B- Explain how the following Protocols are used to support the above network:
Routed protocols e.g. IPv4, IPv6, FTP, HTTP, SMTP, SSL, TCP, POP3
C- Discuss of the various benefits and constraints relating to different network types and standards. e.g. OSI model, TCP/IP model; IEEE 802.x P
D- Explore the use, evolution, limitations, and industry developments in mobile/cellular networks, for the following key technologies; Wi-Fi (IEEE 802.11) , Bluetooth (IEEE 802.15) WiMAX (IEEE 802:16) ZigBee (IEEE 802.15.4) used in IoT and (3G, 4G, 5G). Furthermore, discuss the following network devices: Wireless Access Point (AP) Wireless NIC adapter
E- Explain of the impact different network topologies have on communication and bandwidth requirements. e.g
- Peer-based, client-server ,
Logical: Ethernet, Token Ring;
- Physical: star, ring, mesh, tree
Task
When you configure the TCP/IP protocol on a Microsoft Windows computer, an IP address, subnet mask, and usually a default gateway are required in the TCP/IP configuration settings. Subnetting allows you to create multiple logical networks that exist within a single Class A, B, or C network
Each student is given a separate Class B IP address.
Based on the information shown in the above diagram, design a network-addressing scheme (by completing the table below) that will supply the minimum number of subnets for all the devices on the Technology Centre. You need to allow enough extra subnets and hosts for 50% growth in all circled areas and explain how subnetting of TCP/IP suit of protocols will enable the effectiveness of above network systems.
Task
You will need to produce a discussion of the operating principles of the main networking devices and server types and relate this to the interdependence of workstation hardware to the appropriate networking software that could be used in the above network:
- Networking device
Servers; Hub, routers, switches, access point (wireless/wired), Load balancer, VPN, Firewall, HIDS, IOT gateway
- Networking softwar
Client operating system, server operating system, Internetwork Operating System (IOS) used on many Cisco Systems routers and current Cisco network switches using show version command.
- Workstation: the inter-dependence of workstation hardware with relevant networking software and hardware, e.g. network card, cabling (Fibre Optic, UTP, STP), file permissions
Task
An exploration of the range of available server types, choose and justify a suitable server for the requirements specification the company has given you with due regard to cost and performance optimisation.
Task
In most cases, having the same subnet mask for all subnets ends up wasting address space wasted address space due to the fact that the same subnet mask is being used for all the subnets. Use the Variable Length Subnet Masks (VLSM) to address the efficient utilisation of a networking system and show in the tables below the wasted address spaces and Point-to-Point link networks (only two hosts on each) are used. Furthermore, explain the advantages of using the VLSM in the above network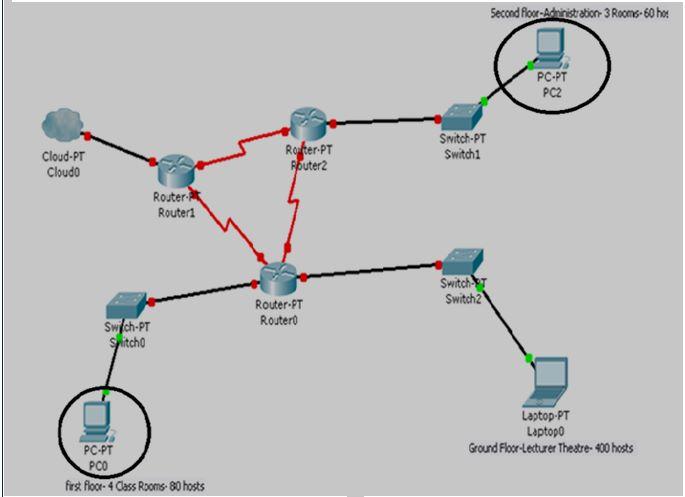
. 5 4. e: s: 3
.2 . s.1. 1
..........ges of using the VLSM in the above network.
Second flose-Adrinstrobion-3 Roons- 60 hos When you configure the TCP/IP protocol on a Microsoft Windows computer, an IP address, subnet mask and usually a default gateway are required in the TCP/IP configuration settings. Subnetting allows you to reate multiple logical networks that exist within a single Class A, B, or C network. Each student is aiven a separate Class B IP address. Based on the information shown in the above diagram, design a network-addressing scheme (by completing the table below) that will supply the minimum number of subnets for all the devices on the Technology Clentre". You need to allow enough extra subnets and hosts for 50% growth in all circlec areas and explain how subnetting of TCP/IP suit of protocols will enable the effectiveness of above network ystemsStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


