 Security Report:
Security Report:
The weekly assignment for the course is a comprehensive assignment. You should begin by reviewing the scenario document. Each week, you will complete part of this assignment based on the content covered in the week. You will add new content to the report each week to build a comprehensive security solution for an organization.
You have been hired by this company to suggest ways of securing its technology assets. ABC, Inc. requires you to complete the project and provide detailed recommendations for improving their security in the next five weeks. You will be assigned specific tasks in each of the weeks of this course based on the content covered in the week.
As you complete this assignment, you must also realize the importance of describing the implementation of the solution that you propose and explaining how to verify the solution by providing activities to test the security (such as intentionally using an incorrect password to make sure the system rejects the login attempt).
In this week, review the scenario and analyze the security requirements of the organization. On the basis of your understanding, create a 3- to 4-page report in a Microsoft Word document that includes the following:
- A paragraph summarizing the problems faced by the organization.
- A list of top five recommendations for implementing better security in the organization and an explanation of how each of these will benefit the organization. Justify the importance in your ranking.
- Outcomes for your report, such as what implementing your solution will do for the organization; this should be a preliminary report that will evolve as the weeks progress.
In addition, respond to the following questions in your report:
- How does an attack like the one suffered by ABC, Inc. impact consumer confidence in its product? Why would the company wish to remain anonymous during this process?
- Which basic user policies would you put in place to make sure employees cannot access each other's information?
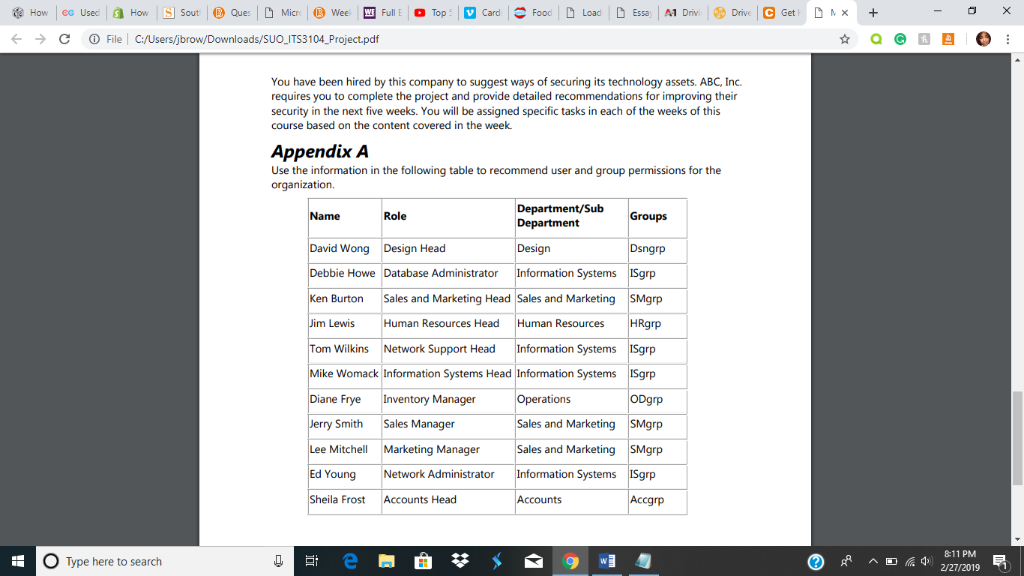
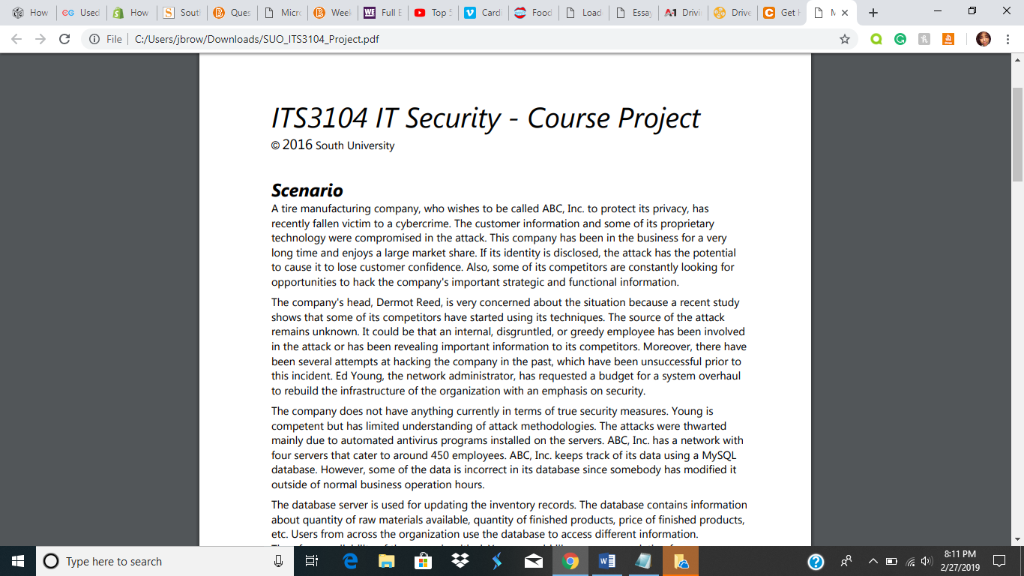
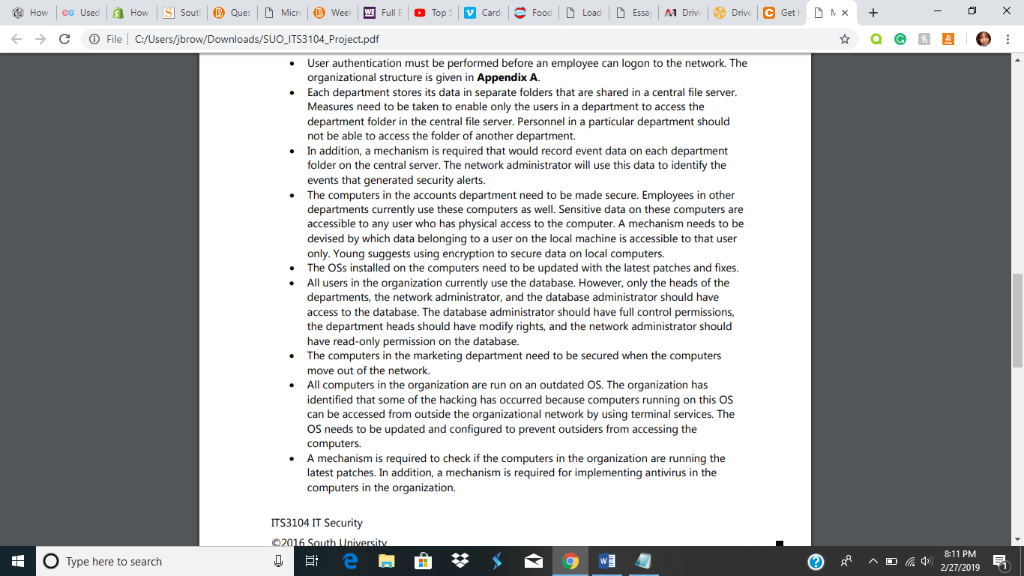
File | C:/Users/jbrow/Downloads/SUO-TS3 104-Project.pdf ITS3104 IT Security - Course Project 2016 South University Scenario A tire manufacturing company, who wishes to be called ABC, Inc. to protect its privacy, has recently fallen victim to a cybercrime. The customer information and some of its proprietary technology were compromised in the attack. This company has been in the business for a very long time and enjoys a large market share. If its identity is disclosed, the attack has the potential to cause it to lose customer confidence. Also, some of its competitors are constantly looking for opportunities to hack the company's important strategic and functional information. The company's head, Dermot Reed, is very concerned about the situation because a recent study shows that some of its competitors have started using its techniques. The source of the attack remains unknown. It could be that an internal, disgruntled, or greedy employee has been involved in the attack or has been revealing important information to its competitors. Moreover, there have been several attempts at hacking the company in the past, which have been unsuccessful prior to this incident. Ed Young, the network administrator, has requested a budget for a system overhaul to rebuild the infrastructure of the organization with an emphasis on security The company does not have anything currently in terms of true security measures. Young is competent but has limited understanding of attack methodologies. The attacks were thwarted mainly due to automated antivirus programs installed on the servers. ABC, Inc. has a network with four servers that cater to around 450 employees. ABC, Inc. keeps track of its data using a MySQL database. However, some of the data is incorrect in its database since somebody has modified it outside of normal business operation hours. The database server is used for updating the inventory records. The database contains information about quantity of raw materials available, quantity of finished products, price of finished products, etc. Users from across the organization use the database to access different information. 8-11 PM O Type here to search File | C:/Users/jbrow/Downloads/SUO-TS3 104-Project.pdf User authentication must be performed before an employee can logon to the network. The organizational structure is given in Appendix A. . Each department stores its data in separate folders that are shared in a central file server. Measures need to be taken to enable only the users in a department to access the department folder in the central file server. Personnel in a particular department should not be able to access the folder of another department. In addition, a mechanism is required that would record event data on each department folder on the central server. The network administrator will use this data to identify the . The computers in the accounts department need to be made secure. Employees in other departments currently use these computers as well. Senstive data on these computers are accessible to any user who has physical access to the computer. A mechanism needs to be devised by which data belonging to a user on the local machine is accessible to that user only. Young suggests using encryption to secure data on local computers. The OSs installed on the computers need to be updated with the latest patches and fixes. All users in the organization currently use the database. However, only the heads of the departments, the network administrator, and the database administrator should have access to the database. The database administrator should have full control permissions, the department heads should have modify rights, and the network administrator should have read-only permission on the database. .The computers in the marketing department need to be secured when the computers move out of the network. All computers in the organization are run on an outdated OS. The organization has identified that some of the hacking has occurred because computers running on this OS can be accessed from outside the organizational network by using terminal services. The OS needs to be updated and configured to prevent outsiders from accessing the .A mechanism is required to check if the computers in the organization are running the latest patches. In addition, a mechanism is required for implementing antivirus in the computers in the organization. ITS3104 IT Security O Type here to search 8-11 PM 2/27/2019 File | C:/Users/jbrow/Downloads/SUO-TS3 104-Project.pdf You have been hired by this company to suggest ways of securing its technology assets. ABC, Inc. requires you to complete the project and provide detailed recommendations for improving their security in the next five weeks. You will be assigned specific tasks in each of the weeks of this course based on the content covered in the week Appendix A Use the information in the following table to recommend user and group permissions for the organization Name Role Groups Department Design Dsngrp David Wong Design Head Debbie Howe Database Administrator Information Systems ISgrp Ken Burton Sales and Marketing Head Sales and Marketing SMgrp Lewis Human Resources Head Human Resources HRgrp Tom Wilkins Network Support Head Information Systems ISgrp Mike Womack Information Systems Head Information Systems ISgrp Diane Frye Inventory Manager ODgrp y SmithSales Manager Lee Mitchel Marketing Manager Ed Young Network Administrator Information SystemsISgrp Operations Sales and MarketingSMgrp Sales and Marketing SMgrp la Frost Accounts Head Accounts Accgrp O Type here to search 8-11 PM 2/27/2019 File | C:/Users/jbrow/Downloads/SUO-TS3 104-Project.pdf ITS3104 IT Security - Course Project 2016 South University Scenario A tire manufacturing company, who wishes to be called ABC, Inc. to protect its privacy, has recently fallen victim to a cybercrime. The customer information and some of its proprietary technology were compromised in the attack. This company has been in the business for a very long time and enjoys a large market share. If its identity is disclosed, the attack has the potential to cause it to lose customer confidence. Also, some of its competitors are constantly looking for opportunities to hack the company's important strategic and functional information. The company's head, Dermot Reed, is very concerned about the situation because a recent study shows that some of its competitors have started using its techniques. The source of the attack remains unknown. It could be that an internal, disgruntled, or greedy employee has been involved in the attack or has been revealing important information to its competitors. Moreover, there have been several attempts at hacking the company in the past, which have been unsuccessful prior to this incident. Ed Young, the network administrator, has requested a budget for a system overhaul to rebuild the infrastructure of the organization with an emphasis on security The company does not have anything currently in terms of true security measures. Young is competent but has limited understanding of attack methodologies. The attacks were thwarted mainly due to automated antivirus programs installed on the servers. ABC, Inc. has a network with four servers that cater to around 450 employees. ABC, Inc. keeps track of its data using a MySQL database. However, some of the data is incorrect in its database since somebody has modified it outside of normal business operation hours. The database server is used for updating the inventory records. The database contains information about quantity of raw materials available, quantity of finished products, price of finished products, etc. Users from across the organization use the database to access different information. 8-11 PM O Type here to search File | C:/Users/jbrow/Downloads/SUO-TS3 104-Project.pdf User authentication must be performed before an employee can logon to the network. The organizational structure is given in Appendix A. . Each department stores its data in separate folders that are shared in a central file server. Measures need to be taken to enable only the users in a department to access the department folder in the central file server. Personnel in a particular department should not be able to access the folder of another department. In addition, a mechanism is required that would record event data on each department folder on the central server. The network administrator will use this data to identify the . The computers in the accounts department need to be made secure. Employees in other departments currently use these computers as well. Senstive data on these computers are accessible to any user who has physical access to the computer. A mechanism needs to be devised by which data belonging to a user on the local machine is accessible to that user only. Young suggests using encryption to secure data on local computers. The OSs installed on the computers need to be updated with the latest patches and fixes. All users in the organization currently use the database. However, only the heads of the departments, the network administrator, and the database administrator should have access to the database. The database administrator should have full control permissions, the department heads should have modify rights, and the network administrator should have read-only permission on the database. .The computers in the marketing department need to be secured when the computers move out of the network. All computers in the organization are run on an outdated OS. The organization has identified that some of the hacking has occurred because computers running on this OS can be accessed from outside the organizational network by using terminal services. The OS needs to be updated and configured to prevent outsiders from accessing the .A mechanism is required to check if the computers in the organization are running the latest patches. In addition, a mechanism is required for implementing antivirus in the computers in the organization. ITS3104 IT Security O Type here to search 8-11 PM 2/27/2019 File | C:/Users/jbrow/Downloads/SUO-TS3 104-Project.pdf You have been hired by this company to suggest ways of securing its technology assets. ABC, Inc. requires you to complete the project and provide detailed recommendations for improving their security in the next five weeks. You will be assigned specific tasks in each of the weeks of this course based on the content covered in the week Appendix A Use the information in the following table to recommend user and group permissions for the organization Name Role Groups Department Design Dsngrp David Wong Design Head Debbie Howe Database Administrator Information Systems ISgrp Ken Burton Sales and Marketing Head Sales and Marketing SMgrp Lewis Human Resources Head Human Resources HRgrp Tom Wilkins Network Support Head Information Systems ISgrp Mike Womack Information Systems Head Information Systems ISgrp Diane Frye Inventory Manager ODgrp y SmithSales Manager Lee Mitchel Marketing Manager Ed Young Network Administrator Information SystemsISgrp Operations Sales and MarketingSMgrp Sales and Marketing SMgrp la Frost Accounts Head Accounts Accgrp O Type here to search 8-11 PM 2/27/2019

 Security Report:
Security Report:






