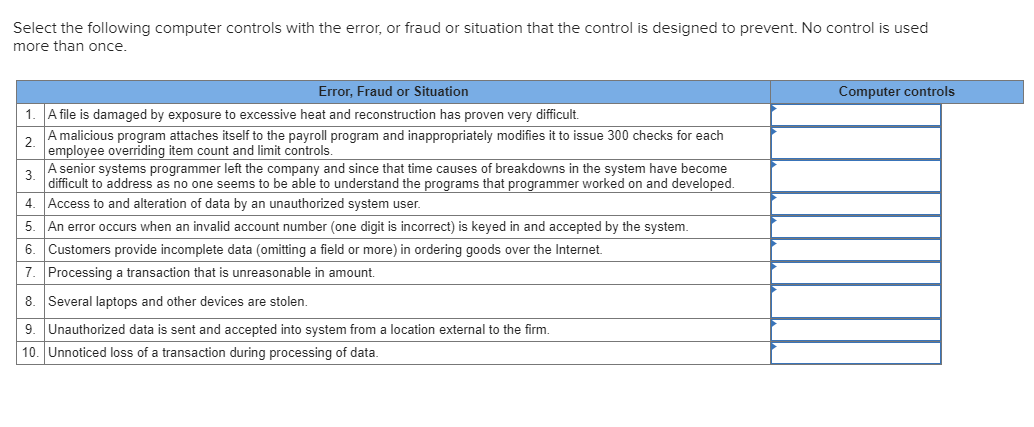
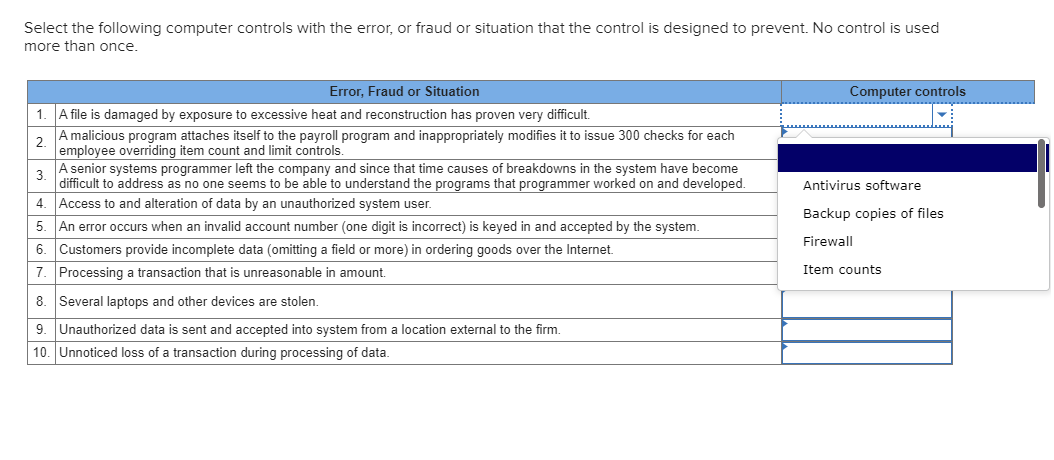
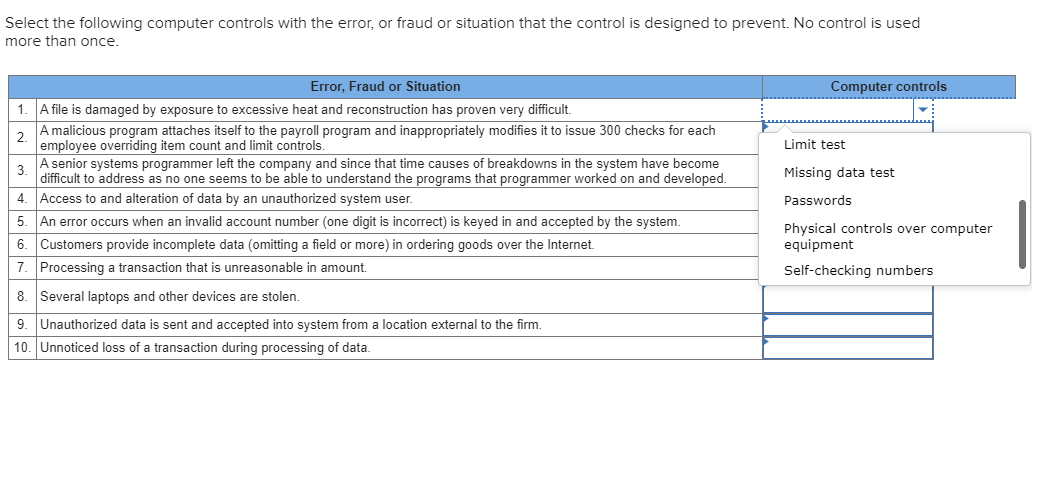
Select the following computer controls with the error, or fraud or situation that the control is designed to prevent. No control is used more than once. Computer controls Error, Fraud or Situation 1. A file is damaged by exposure to excessive heat and reconstruction has proven very difficult. A malicious program attaches itself to the payroll program and inappropriately modifies it to issue 300 checks for each employee overriding item count and limit controls. A senior systems programmer left the company and since that time causes of breakdowns in the system have become difficult to address as no one seems to be able to understand the programs that programmer worked on and developed. 4. Access to and alteration of data by an unauthorized system user. 5. An error occurs when an invalid account number (one digit is incorrect) is keyed in and accepted by the system. 6. Customers provide incomplete data (omitting a field or more) in ordering goods over the Internet. 7. Processing a transaction that is unreasonable in amount. 8. Several laptops and other devices are stolen. 9. Unauthorized data is sent and accepted into system from a location external to the firm. 10. Unnoticed loss of a transaction during processing of data. Select the following computer controls with the error, or fraud or situation that the control is designed to prevent. No control is used more than once. Computer controls Error, Fraud or Situation 1. A file is damaged by exposure to excessive heat and reconstruction has proven very difficult. A malicious program attaches itself to the payroll program and inappropriately modifies it to issue 300 checks for each employee overriding item count and limit controls. A senior systems programmer left the company and since that time causes of breakdowns in the system have become difficult to address as no one seems to be able to understand the programs that programmer worked on and developed. 4. Access to and alteration of data by an unauthorized system user. 5. An error occurs when an invalid account number (one digit is incorrect) is keyed in and accepted by the system. 6. Customers provide incomplete data omitting a field or more) in ordering goods over the Internet. 7. Processing a transaction that is unreasonable in amount Antivirus software Backup copies of files Firewall Item counts 8. Several laptops and other devices are stolen. 9. Unauthorized data is sent and accepted into system from a location external to the firm. 10. Unnoticed loss of a transaction during processing of data. Select the following computer controls with the error, or fraud or situation that the control is designed to prevent. No control is used more than once. Computer controls Error, Fraud or Situation 1. A file is damaged by exposure to excessive heat and reconstruction has proven very difficult. A malicious program attaches itself to the payroll program and inappropriately modifies it to issue 300 checks for each employee overriding item count and limit controls. A senior systems programmer left the company and since that time causes of breakdowns in the system have become difficult to address as no one seems to be able to understand the programs that programmer worked on and developed 4. Access to and alteration of data by an unauthorized system user. 5. An error occurs when an invalid account number (one digit is incorrect) is keyed in and accepted by the system. 6. Customers provide incomplete data (omitting a field or more) in ordering goods over the Internet. 7. Processing a transaction that is unreasonable in amount. Limit test Missing data test Passwords Physical controls over computer equipment Self-checking numbers 8. Several laptops and other devices are stolen. 9. Unauthorized data is sent and accepted into system from a location external to the firm. 10. Unnoticed loss of a transaction during processing of data









