Question
Study the diagram and answer the questions that follow. List all the types of traffic and activities that may occur, which you think would be
Study the diagram and answer the questions that follow.
List all the types of traffic and activities that may occur, which you think would be illicit or inappropriate, and could potentially pose a threat to network resources, as well as any activities be detected by the signature-based intrusion detection system, as deployed?
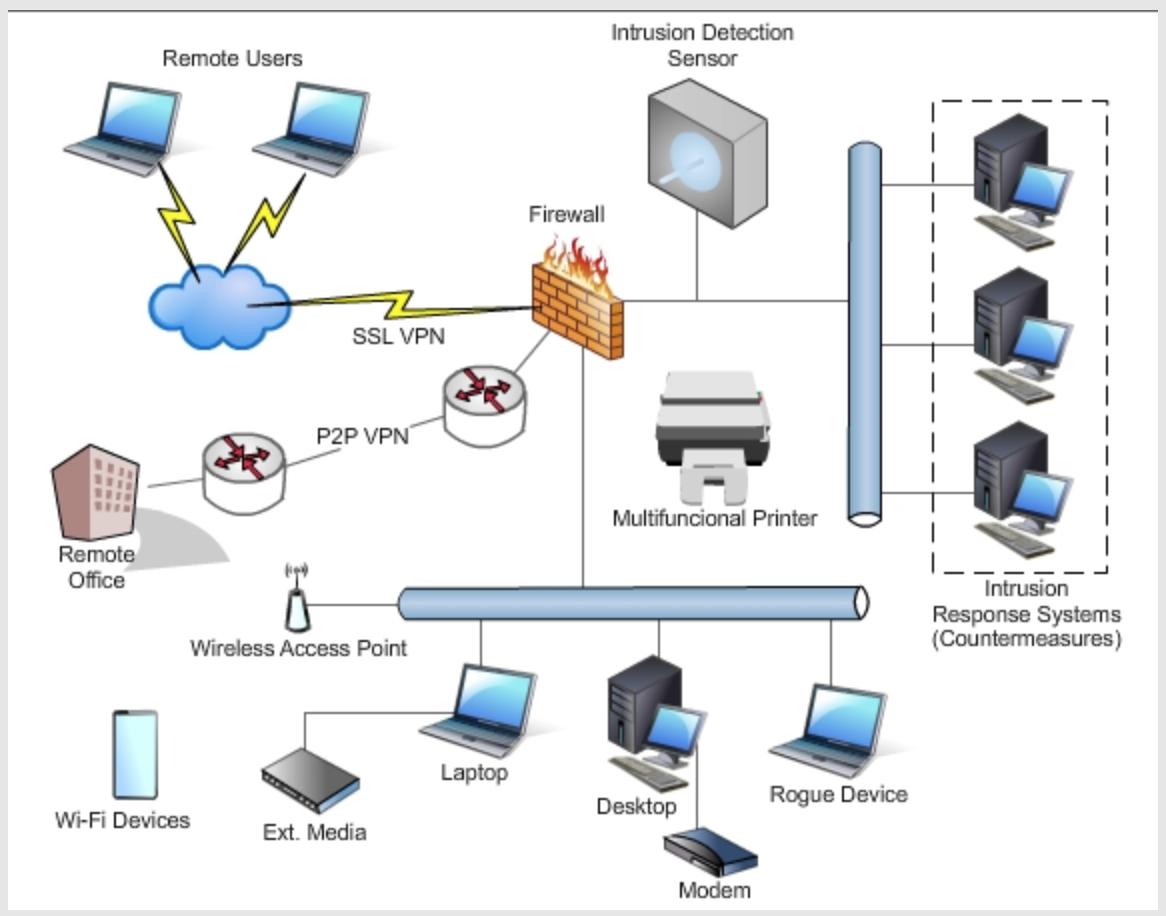
Remote Office Remote Users SSL VPN Wi-Fi Devices P2P VPN Wireless Access Point Ext. Media Laptop Firewall Intrusion Detection Sensor Multifuncional Printer Desktop Modem Rogue Device Intrusion Response Systems (Countermeasures)
Step by Step Solution
There are 3 Steps involved in it
Step: 1
The main activity from the above network model is sharingaccessing the information remotedly 1 The r...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get StartedRecommended Textbook for
Fundamentals Of Electric Circuits
Authors: Matthew Sadiku, Charles Alexander
3rd Edition
978-0073301150, 0073301159
Students also viewed these Computer Network questions
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
View Answer in SolutionInn App



