Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Suppose XYZ Software Company has a new application development project with projected revenues of $1.2 million. Using the following table, calculate the ARO and ALE
- Suppose XYZ Software Company has a new application development project with projected revenues of $1.2 million. Using the following table, calculate the ARO and ALE for each threat category the company faces for this project.
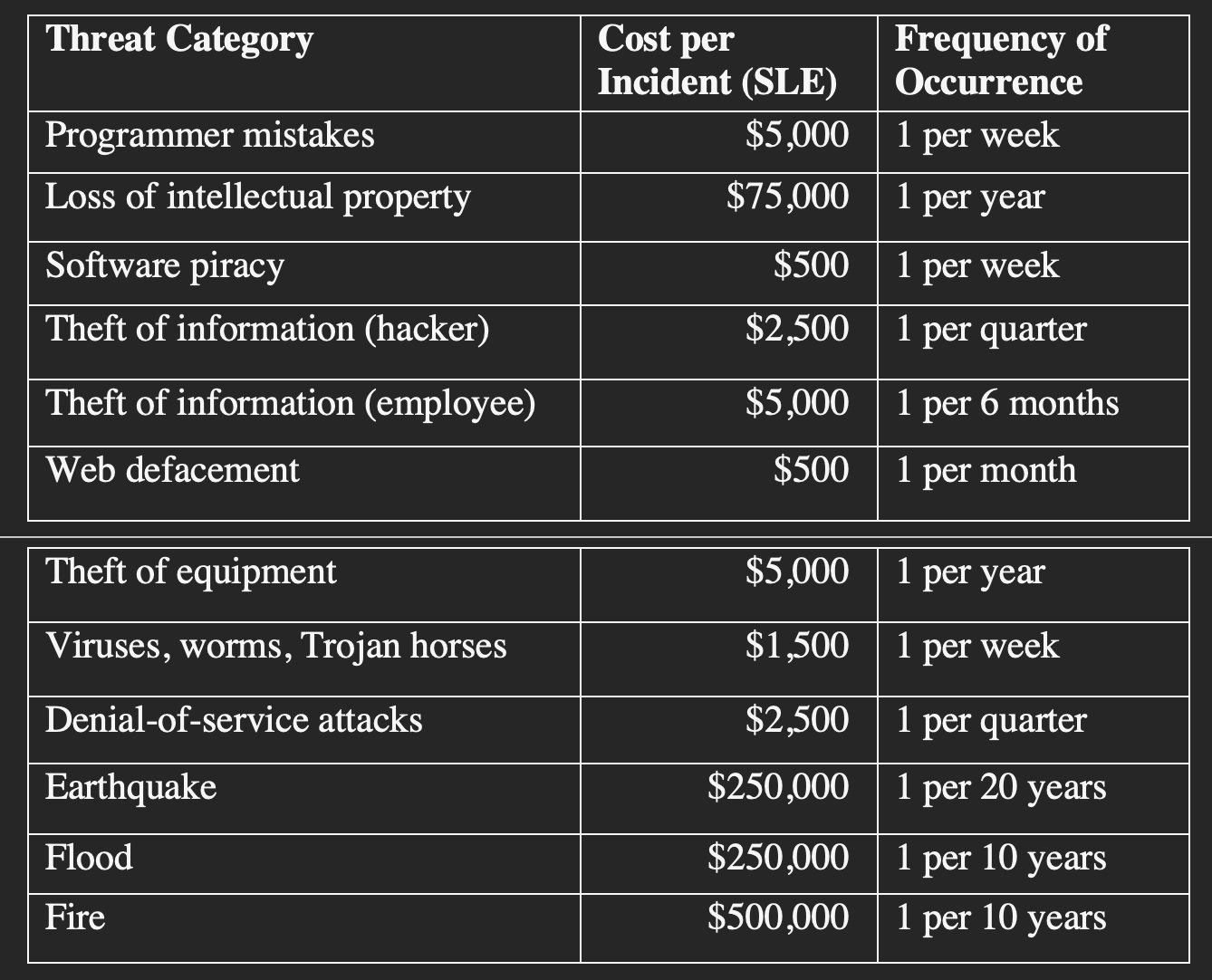
- Assume that a year has passed and XYZ has improved security by applying several controls. Using the information calculated above and the following table below, calculate the post-control ARO and ALE for each threat category listed.
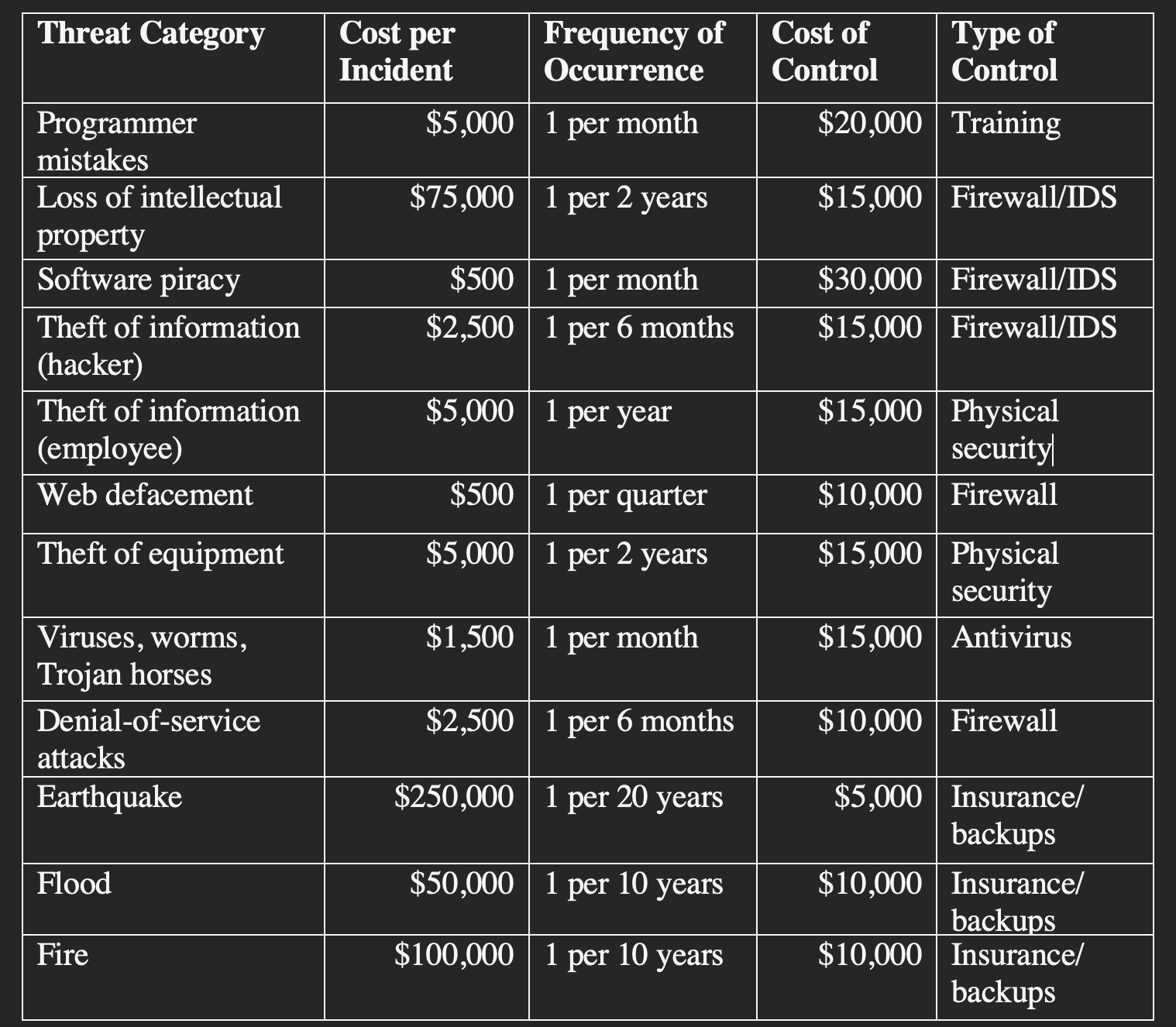
- Why have some values changed in the Cost per Incident and Frequency of Occurrence columns? How could a control affect one but not the other? Assume that the values in the Cost of Control column are unique costs directly associated with protecting against the threat. In other words, dont consider overlapping costs between controls. Calculate the CBA for the planned risk control approach in each threat category. For each threat category, determine whether the proposed control is worth the costs. EXPLAIN IN DETAIL.
\begin{tabular}{|l|r|l|} \hline Threat Category & CostperIncident(SLE) & FrequencyofOccurrence \\ \hline Programmer mistakes & $5,000 & 1 per week \\ \hline Loss of intellectual property & $75,000 & 1 per year \\ \hline Software piracy & $500 & 1 per week \\ \hline Theft of information (hacker) & $2,500 & 1 per quarter \\ \hline Theft of information (employee) & $5,000 & 1 per 6 months \\ \hline Web defacement & $500 & 1 per month \\ \hline Theft of equipment & $5,000 & 1 per year \\ \hline Viruses, worms, Trojan horses & $1,500 & 1 per week \\ \hline Denial-of-service attacks & $2,500 & 1 per quarter \\ \hline Earthquake & $250,000 & 1 per 20 years \\ \hline Flood & $250,000 & 1 per 10 years \\ \hline Fire & $500,000 & 1 per 10 years \\ \hline \end{tabular} \begin{tabular}{|l|r|l|r|l|} \hline Threat Category & CostperIncident & FrequencyofOccurrence & CostofControl & TypeofControl \\ \hline Programmermistakes & $5,000 & 1 per month & $20,000 & Training \\ \hline Lossofintellectualproperty & $75,000 & 1 per 2 years & $15,000 & Firewall/IDS \\ \hline Software piracy & $500 & 1 per month & $30,000 & Firewall/IDS \\ \hline Theftofinformation(hacker) & $2,500 & 1 per 6 months & $15,000 & Firewall/IDS \\ \hline Theftofinformation(employee) & $5,000 & 1 per year & $15,000 & Physicalsecurityl \\ \hline Webdefacement & $500 & 1 per quarter & $10,000 & Firewall \\ \hline Theftofequipment & $5,000 & 1 per 2 years & $15,000 & Physicalsecurity \\ \hline Viruses,worms,Trojanhorses & $1,500 & 1 per month & $15,000 & Antivirus \\ \hline Denial-of-serviceattacks & $2,500 & 1 per 6 months & $10,000 & Firewall \\ \hline Earthquake & $250,000 & 1 per 20 years & $5,000 & Insurance/backups \\ \hline Flood & $50,000 & 1 per 10 years & $10,000 & Insurance/backups \\ \hline Fire & $100,000 & 1 per 10 years & $10,000 & Insurance/backups \\ \hline \end{tabular}
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


