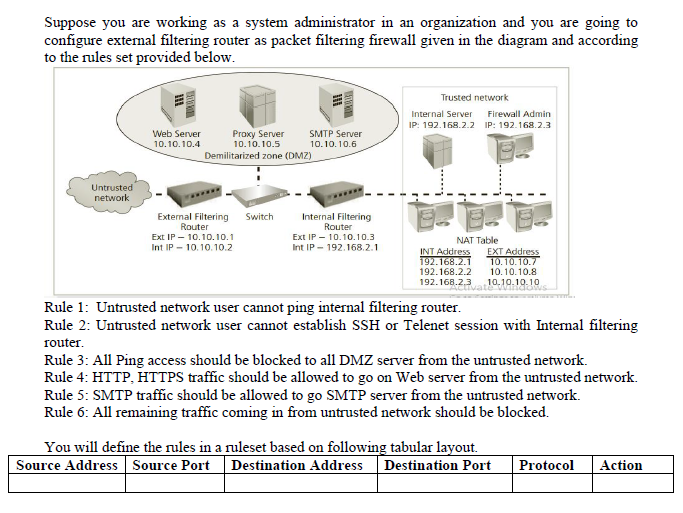
Suppose you are working as a system administrator in an organization and you are going to configure external filtering router as packet filtering firewall given in the diagram and according to the rules set provided below. Trusted network Internal Server Firewall Admin IP: 192.168.2.2 IP: 192.168.2.3 Web Server Proxy Server SMTP Server 10.10.10.4 10.10.10.5 10.10.10.6 Demilitarized zone (DMZ) Untrusted network Switch External Filtering Router Ext IP-10.10.10.1 Int IP - 10.10.10.2 Internal Filtering Router Ext IP - 10.10.10.3 Int IP - 192.168.2.1 NAT Table INT Address EXT Address 192.168.2.1 10.10.10.7 192.168.2.2 10.10.10.8 192.168.2.3 10.10.10.10 Rule 1: Untrusted network user cannot ping internal filtering router. Rule 2: Untrusted network user cannot establish SSH or Telenet session with Internal filtering router. Rule 3: All Ping access should be blocked to all DMZ server from the untrusted network. Rule 4: HTTP, HTTPS traffic should be allowed to go on Web server from the untrusted network. Rule 5: SMTP traffic should be allowed to go SMTP server from the untrusted network. Rule 6: All remaining traffic coming in from untrusted network should be blocked. You will define the rules in a ruleset based on following tabular layout. Source Address Source Port Destination Address Destination Port Protocol Action Suppose you are working as a system administrator in an organization and you are going to configure external filtering router as packet filtering firewall given in the diagram and according to the rules set provided below. Trusted network Internal Server Firewall Admin IP: 192.168.2.2 IP: 192.168.2.3 Web Server Proxy Server SMTP Server 10.10.10.4 10.10.10.5 10.10.10.6 Demilitarized zone (DMZ) Untrusted network Switch External Filtering Router Ext IP-10.10.10.1 Int IP - 10.10.10.2 Internal Filtering Router Ext IP - 10.10.10.3 Int IP - 192.168.2.1 NAT Table INT Address EXT Address 192.168.2.1 10.10.10.7 192.168.2.2 10.10.10.8 192.168.2.3 10.10.10.10 Rule 1: Untrusted network user cannot ping internal filtering router. Rule 2: Untrusted network user cannot establish SSH or Telenet session with Internal filtering router. Rule 3: All Ping access should be blocked to all DMZ server from the untrusted network. Rule 4: HTTP, HTTPS traffic should be allowed to go on Web server from the untrusted network. Rule 5: SMTP traffic should be allowed to go SMTP server from the untrusted network. Rule 6: All remaining traffic coming in from untrusted network should be blocked. You will define the rules in a ruleset based on following tabular layout. Source Address Source Port Destination Address Destination Port Protocol Action







