Answered step by step
Verified Expert Solution
Question
1 Approved Answer
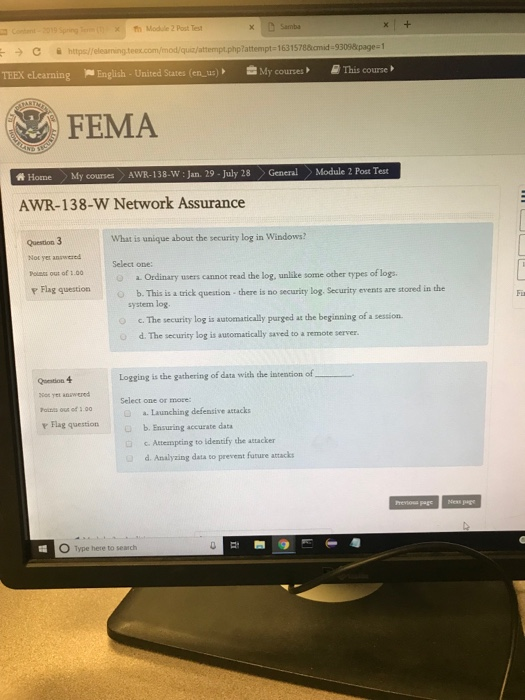
th Module 2 Past Test Samba C&https//eleaning.teex.com/mod/quiajattempt.phplattempt-16315788cmid-93088page-1 eLearning ~ English-United States (en_us) My courses This course , FEMA # Home My courses AWR-138-W : Jan.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


